What Is Network Security Situational Awareness?
Situational awareness or situation awareness (SA) is the perception of environmental elements with respect to time or space, the comprehension of their meaning, and the projection of their future status. Currently, situational awareness mainly refers to network security situational awareness, that is, the application of situational awareness-related theories and methods to the network security field. Network security situational awareness enables personnel involved in network security to understand the security status of the entire network, identify problems and abnormal activities on the network, and provide feedback or make improvements. The analysis and projection of the network security situation within a period of time provide a strong foundation for high-level decision-making.
- Origin of Network Security Situational Awareness
- Why Is Network Security Situational Awareness Important?
- Application Scenarios of Network Security Situational Awareness
- How Is the Construction Result of Situational Awareness Evaluated?
- What Are the Three Levels of Situational Awareness?
- HiSec Insight — Huawei's Situational Awareness Product
Origin of Network Security Situational Awareness
Situational awareness is a term coined by the United States Air Force in the 1980s. It mainly covered analyzing the air combat environment information, analyzing the current and future situations, and ultimately making corresponding judgments and decisions. Through continuous development and improvement, related theories have been formed and widely used in domains such as the military, aviation, industrial production, security, and network domains. Network security situational awareness refers to the application of situational awareness-related theories and methods to the network security field.
The concept of situational awareness is abstract. To facilitate understanding, we can use weather forecasting as an example. With continuous observing and analyzing, we can predict the weather at a site over a certain period of time. In particular, the prediction of severe weather events, such as typhoon, smog, and snowstorm, is especially important to us. By transferring people and property in advance and preparing related disaster response measures, the impact of disasters can be greatly reduced. This is the key purpose of situational awareness.
Why Is Network Security Situational Awareness Important?
With the continuous development of network and information technologies, people's security awareness is gradually increasing. Networks are never completely secure. It is inevitable that they will be attacked eventually. Although we cannot prevent attacks, we can identify and detect attacks in advance to minimize losses. In other words, security protection has shifted from passive defense to proactive and intelligent protection.
Furthermore, IoT and cloud technologies are developing rapidly, giving rise to many new disruptive technologies that bring new security issues. For example, massive terminal access, disappearance of traditional network borders, and increased concealment and complexity of network attacks pose new challenges and higher requirements on the capabilities of network security personnel.
Against this backdrop, products and solutions centering on network security situational awareness technologies have developed rapidly. Network security situational awareness can drive the upgrade of the entire security protection system and implement the following three changes:
- The goal of security construction changes from compliance to enhanced defense and deterrence capabilities, with greater emphasis placed on confrontation. This poses higher requirements on intelligence technologies.
- The object of attack detection changes from known threats to unknown threats. Technologies such as big data analytics, anomaly detection, situational awareness, and machine learning are used to detect advanced threats.
- The response to threats changes from manual analysis and handling to automatic and closed-loop response, with an emphasis on emergency response and collaboration, achieving elastic security.
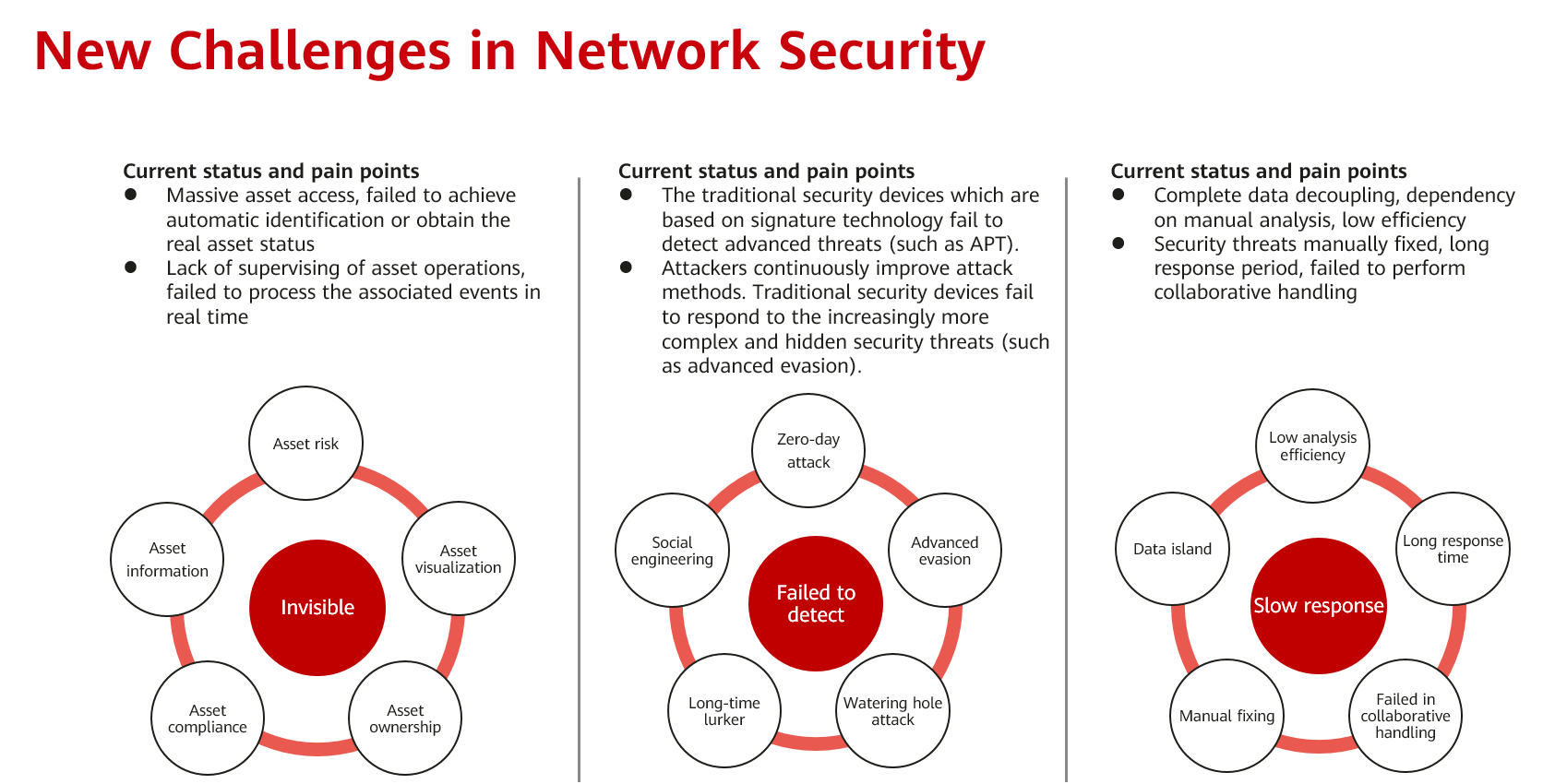
New challenges in network security
Application Scenarios of Network Security Situational Awareness
Constructing a network security situational awareness system is complex and expensive. Such a system is used mainly in large and midsize enterprises and large organizations. For small businesses, a single integrated product offering lower performance and simpler functions and architecture can be selected.
- Government agencies: From the perspective of countries or provinces/cities, the system manages and monitors the network security situation of related information infrastructure.
- Large industries: From the perspective of industries, the system manages and monitors the network security situations of internal systems in an industry. Currently, network security situational awareness is mainly applied to sectors such as government, finance, network operations, and education.
- Large organizations or enterprises: From the perspective of routine security O&M, the system manages and monitors the security status of core assets and service systems.
How Is the Construction Result of Situational Awareness Evaluated?
The construction result of network security situational awareness can be evaluated from the following aspects:
- Defense: Whether the obtained intelligence and asset investigation information can be used to improve the defense system and eliminate asset risks
- Detection: Whether continuous network security monitoring capabilities are provided to quickly and accurately detect security threats
- Response: Whether response capabilities covering terminals and networks are provided to support attack forensic, event source tracing, threat fixing, and other items
- Prediction: Whether improvement suggestions can be provided based on the comprehensive analysis of historical security situations, live-network popular attacks, and intelligence systems
What Are the Three Levels of Situational Awareness?
In Toward a Theory of Situation Awareness in Dynamic Systems (1995), Mica Endsley proposed a classic situational awareness model that mimics the cognitive process of humans. Although the model is simple, it has formed the basis of many subsequent theories. It is generally called the Endsley's model.
Endsley's model divides the situational awareness into three levels: perception, comprehension, and projection.
- Perception (Level 1): The first level of situational awareness is to perceive the status, attributes, and dynamics of related elements in the environment.
- Comprehension (Level 2): The second level of situational awareness involves a synthesis of disjointed elements through the processes of pattern recognition, interpretation, and evaluation. This level also requires integrating the information to understand how it will impact upon the goals.
- Projection (Level 3): The third level of situational awareness involves the ability to project the future actions of the elements in the environment. This is achieved through comprehension of the situation in level 1 and level 2.
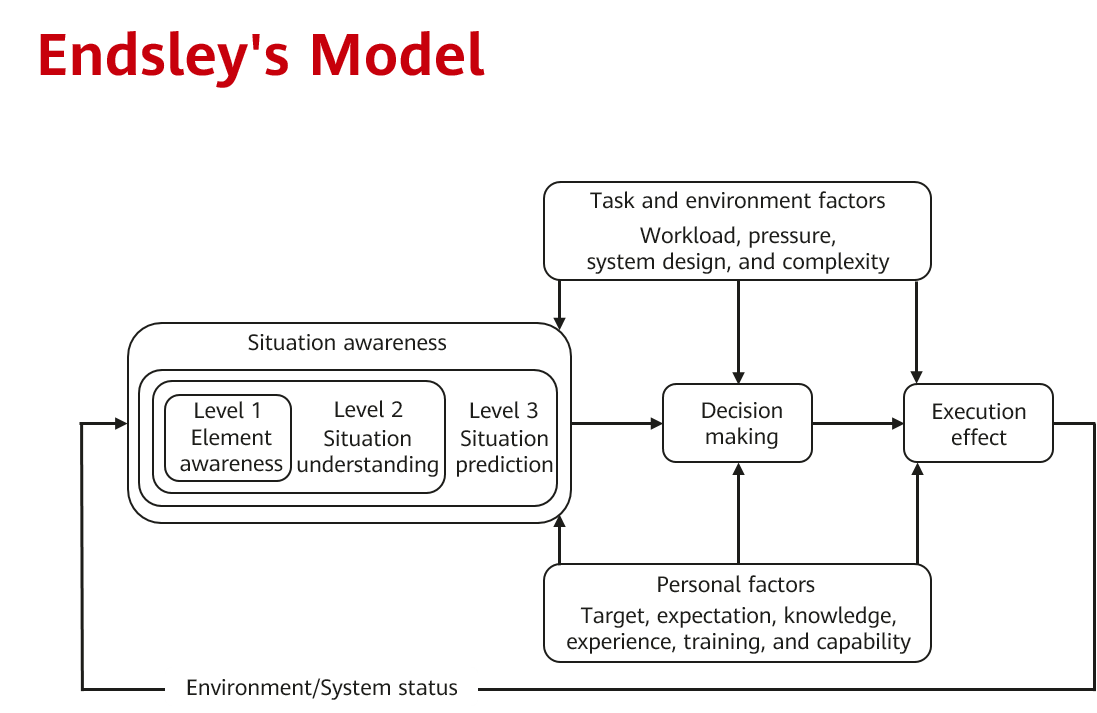
Endsley's model
HiSec Insight — Huawei's Situational Awareness Product
Oriented toward small-, medium-, and large-sized enterprises, such as finance, network security, government, and carrier enterprises, Huawei launched HiSec Insight Advanced Threat Analytics System (HiSec Insight for short). This big data-based APT defense product implements security situational awareness on the entire network by collecting massive amounts of basic data (such as network traffic and network and security logs of various devices) and identifying potential and advanced threats on the network through big data analytics and machine learning technologies.
Advanced Threat Detection
Based on machine learning and the big data platform, HiSec Insight quickly and accurately detects advanced threats on borders and intranets.
- It analyzes multi-source data, including original traffic, logs, and NetFlow data.
- It leverages multiple anomaly detection models, including encrypted traffic detection, web anomaly detection, mail anomaly detection, C&C anomaly detection, and covert channel detection models.
- It covers the entire kill chain of advanced threats, involving resource reconnaissance, external penetration, command and control (C&C), internal diffusion, and data sending.
Network-wide Security Situational Awareness
HiSec Insight dynamically integrates information about attacks, threats, vulnerabilities, and assets on a network and provides users with network security status from a global perspective through big data processing and integration capabilities. Graphical attack source tracing is used to display a complete attack path, providing effective and intuitive reference for subsequent decision-making and actions.
- Comprehensive security situation: displays the security situation of the entire network from multiple dimensions, such as the threat map, asset risks, vulnerabilities, threat sources, and security information.
- Intranet security situation: displays information such as intranet security-related threat events, compromised hosts, top external communication ports, and external communication traffic trend.
- Website security situation: displays website-related threat events, vulnerabilities, top threat sources, threat distribution by type, and access trend.
- Asset security situation: displays information, such as the asset vulnerability distribution, risk ranking, high-risk port distribution, and asset distribution by type.
- Vulnerability situation: displays the number of vulnerabilities, vulnerability distribution, top high-risk asset vulnerabilities, vulnerability trends, and vulnerability types.
- Threat event situation: displays trending events, threat event statistics, top threat event types, real-time threat events, and other information.
- Profile analysis on attackers: displays attacker information, kill chain, attack trends, attack-related events, and other information.
- Profile analysis on compromised host: displays asset risks, fingerprint information, asset vulnerabilities, threat events, and other information.
Security Response Collaboration
Based on smart search, HiSec Insight quickly and accurately implements investigation and backtracking. In addition, HiSec Insight can work together with HiSec security solution to implement network security collaboration, shift from single-point defense to global defense, and ultimately achieve automatic threat handling to quickly block threats.
- It quickly searches for logs and original traffic based on keywords.
- It investigates events based on kill chains, associates original traffic, and downloads PCAP files to facilitate network forensics.
- It supports collaborative investigation and forensics with the endpoint detection and response (EDR) system to quickly identify the infection scope.
- It supports interworking with the network controller, security controller, firewall, and EDR system.
- It supports Security Orchestration, Automation and Response (SOAR) based on security data sources or security events to implement automatic and closed-loop response.
- Author: Yan Guanghui
- Updated on: 2021-09-30
- Views: 4320
- Average rating:







