What Is 802.1X?
802.1X is a port-based network access control protocol. 802.1X authentication refers to 802.1X-based user authentication, which has been widely used on networks that have high requirements on information security.
Background of 802.1X
In the early IEEE 802 LAN protocols, users can access devices or resources in a LAN as long as they can access the control device (for example, an access switch) in the LAN. This obviously brings security risks. To resolve security issues on wireless LANs (WLANs), the IEEE 802 committee proposed the 802.1X protocol to control the network access rights of users. This protocol effectively prevents unauthorized users from transmitting and receiving data. Due to its good universality, 802.1X has also been widely used on wired LANs.
Different from other access control mechanisms, 802.1X implements user-level access control by controlling access ports. The 802.1X protocol defines two logical port entities for a physical access port — the controlled port and the uncontrolled port — to separate services from authentication. The uncontrolled port is primarily used to transmit Extensible Authentication Protocol over LAN (EAPoL) frames in both directions to ensure that the client can always send and receive authentication packets. The controlled port is able to transmit service packets in both directions when it is in authorized state, but denies all packets from clients when it is in unauthorized state.
In other words, 802.1X authentication ultimately determines whether the access port of a user is available for transmitting services. If the authentication is successful, the port is authorized to allow all packets from the client to pass through. If the authentication fails, the port remains in unauthorized state and allows only EAPoL frames to pass through.
When Is 802.1X Used?
- 802.1X is a Layer 2 protocol and does not involve Layer 3 processing. Therefore, it does not require high performance of access devices, reducing network construction costs.
- A port in unauthorized state does not exchange service packets with clients, ensuring service security.
For example, on an enterprise network, employees' terminals need to access the office network and have high security requirements. Therefore, 802.1X authentication is recommended.
802.1X authentication requires that the 802.1X client software be installed on terminals. Therefore, it is not applicable to public places such as airports and business centers, as these places feature high user mobility, complex terminal types, and relatively low security requirements; instead, Portal authentication can be used in this case. In addition, for dumb terminals (such as printers and fax machines) that do not support 802.1X client software or user name and password input, MAC address authentication is used, rather than 802.1X authentication.
How Does 802.1X Work?
As shown in the following figure, the 802.1X authentication system uses a standard client/server architecture with three components: client, access device, and authentication server.
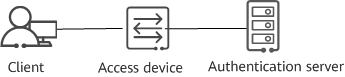
802.1X authentication system
- The client is usually a user terminal, which must support the EAPoL protocol and have the 802.1X client software installed. Users can initiate 802.1X authentication once they start the client software.
- The access device is usually a network device that supports the 802.1X protocol, for example, a switch. It provides a port, either physical or logical, for the client to access the LAN.
- The authentication server performs authentication, authorization, and accounting on users. A Remote Authentication Dial-In User Service (RADIUS) server is typically used as an authentication server.
A user can initiate an authentication request to the connected access device on the terminal that has the 802.1X client software installed. After exchanging information with the user terminal, the access device sends the user information to the authentication server for authentication. If the authentication succeeds, the access device enables the interface connected to the user and allows the user to access the network. If the authentication fails, the access device rejects the user's access request.
- The client and access device exchange EAP packets encapsulated in EAPoL format across the LAN.
- The access device and authentication server exchange authentication information in EAP termination or EAP relay mode.
- EAP termination mode: The access device parses the received EAP packet to obtain user authentication information, and encapsulates the information into a RADIUS packet, which is then sent to the RADIUS server for authentication. As most RADIUS servers support PAP and CHAP authentication, this mode eliminates the need to upgrade servers. However, this mode does not support most EAP authentication methods (except MD5-Challenge), and the access device must have high processing capability.
- EAP relay mode: also known as the EAP over RADIUS (EAPoR) mode. In this mode, the access device directly encapsulates the received EAP packet into a RADIUS packet, and sends the RADIUS packet to the RADIUS server for authentication. This mode simplifies the processing on the access device and supports various authentication methods. However, the authentication server must support EAP and have high processing capability.
The following figure shows the 802.1X authentication process in EAP relay mode. In this example, the client sends an EAPoL-Start packet to trigger authentication.
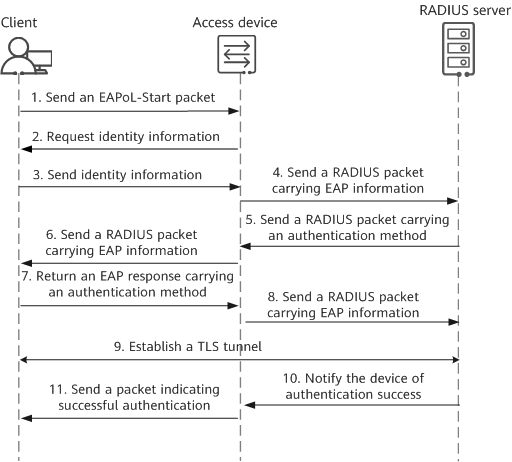
Authentication process in EAP relay mode
- The client sends an EAPoL-Start packet to trigger 802.1X authentication.
The access device sends an EAP request packet to the client to request the user identity information.
The client sends an EAP response packet carrying the user identity information to the access device.
The access device encapsulates the received EAP packet into a RADIUS packet, and sends the resulting packet to the authentication server.
After receiving the user identity information from the access device, the RADIUS server starts to negotiate the EAP authentication method with the client. The RADIUS server sends a RADIUS packet carrying an EAP authentication method to the access device.
The access device forwards the EAP information in the received RADIUS packet to the client.
The client parses the received EAP information to obtain the EAP authentication method selected by the RADIUS server. If the client supports this method, it sends an EAP response packet carrying this method to the access device. If the client does not support this method, it sends an EAP response packet carrying the EAP authentication method it supports to the access device.
- The access device encapsulates the EAP information obtained from the received EAP response packet into a RADIUS packet, and sends the RADIUS packet to the RADIUS server.
- Upon receipt of the RADIUS packet, the RADIUS server checks whether it supports the EAP authentication method specified in the packet. If so, negotiation of the EAP authentication method succeeds, and authentication starts. Assuming that the negotiated EAP authentication method is EAP-PEAP authentication, the server then sends a RADIUS packet carrying its own certificate to client through the access device. The client negotiates TLS parameters and establishes a TLS tunnel with the RADIUS server. This tunnel is used to transmit TLS-encrypted user information among the client, access device, and RADIUS server.
- After authenticating the client, the RADIUS server notifies the access device of the authentication success.
- The access device then sends a packet indicating successful authentication to the client, and changes the port status to authorized, allowing the user to access the network through this port.
- Author: Zhu Yue
- Updated on: 2023-09-01
- Views: 21802
- Average rating:







