What Is an AI Firewall?
An artificial intelligence (AI) firewall, a next-generation product of a next-generation firewall (NGFW), uses intelligent detection technologies to improve the capability of detecting advanced threats and unknown threats. The NGFW uses a static rule database to detect threats, which is difficult to cope with advanced threats of variants. The AI firewall uses the intelligent detection engine to train threat detection models based on massive samples and continuously optimize the models based on real-time traffic data, improving threat detection capabilities.
Why Do We Need the AI Firewall?
Defined by Gartner in 2009, the NGFW deeply integrates basic firewall services with a variety of security services, such as application identification, intrusion protection system (IPS), and antivirus for parallel processing and in-depth traffic security detection. Now, more than 10 years later, with the rapid development of network cloudification, mobility, and the Internet of Things (IoT), NGFWs are facing a number of significant challenges, such as increasing advanced threats and a wide range of variants. The static rule database-based detection of NGFWs can no longer sufficiently tackle these challenges.
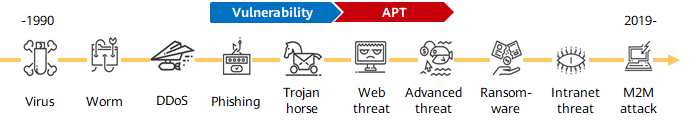
Emerging new threats
As shown in the preceding figure, in addition to traditional threats such as viruses and Trojan horses, advanced threats, for example, advanced persistent threats (APTs), are constantly evolving. As a result, attacks such as ransomware and M2M attacks are becoming increasingly diversified, due to huge economic benefits. Advanced threats are more covert and spread faster, and up to 70% of network attack traffic is encrypted. Facing the rapidly changing threat types, traditional NGFWs must address the following challenges:
- Signature-based threat detection cannot cope with advanced and unknown threats.
Signature-based threat detection relies on signature databases (static rule databases). Signatures in a signature database describe known threats and the database has a limited capacity. The signature database cannot detect unknown and variant advanced threats. This leads to the high false positive rate of threat detection and delayed threat response.
- Multi-layer, three-dimensional, and more covert threats occur, and systems are unable to mitigate the entire kill chain through signature matching.
The popularization of IoT brings more security threats. According to statistics, the number of threats from the intranet increases significantly, indicating that the attacks are not limited to the external network. Hackers infiltrate from the outside, gain remote control, spread to the inside, steal, and destroy important data, forming a complete kill chain. The NGFW matches packet content against signatures and cannot identify the entire kill chain process. As a result, the NGFW cannot accurately mitigate attacks.
In addition, threats are becoming more covert. Most threats are hidden within encrypted channels. Using signatures to match against traffic cannot extract the features of such encrypted traffic. The firewalls must be able to analyze data from all aspects without decrypting the data, so that any threats can be exposed.
- Threat handling is labor intensive and time consuming.
As firewall deployment is not a one-time operation, follow-up O&M is critical. Administrators need to continuously tune policies to cope with changing threats, analyze attack logs, promptly handle threat events, and strengthen enterprise facilities. However, these tasks depend on the skill level of administrators and are complex, and the effect cannot be ensured. Firewalls must have automated data analysis and threat handling capabilities.
To sum up, NGFWs must be upgraded to cope with the continuous evolution of networks and threats. In this regard, the development of AI technologies brings new opportunities for firewalls. Huawei has launched AI firewalls that leverage intelligent detection technology. They use machine learning and in-depth learning to build threat detection models, greatly improving the accuracy and timeliness of threat detection. In addition, the automatic handling technology is introduced to automatically commission policies and analyze threat traffic, relieving the pressure on O&M.
Differences Between AI Firewalls and NGFWs
The main NGFW capabilities defined by Gartner are application identification and IPS integration for in-depth traffic detection. As mentioned above, NGFWs need to be upgraded, and vendors are embracing new technologies to enhance firewall functions. However, there is no standard industry definition of next-generation NGFW product. The following table lists the major differences between Huawei AI firewalls and NGFWs.
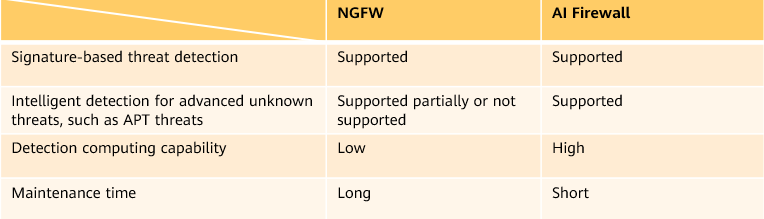
Capability comparison between NGFWs and AI firewalls
The main advantage of AI firewalls lies in intelligence. The AI firewalls not only leverage signatures to mechanically identify known threats, but also use a large number of samples and algorithms to train threat detection models, enabling detection of advanced and unknown threats. However, higher requirements are imposed on computing hardware in order to maximize this newly introduced intelligent detection technology. The AI firewall must provide dedicated hardware for intelligent detection computing to improve threat detection performance.
AI Firewall Detection of Advanced Threats
As mentioned above, AI firewalls can detect advanced threats. Well, what is the implementation? AI firewalls are intelligent, as evidenced by the embedded intelligent detection engine which detects advanced threats based on a threat detection model created through machine learning.
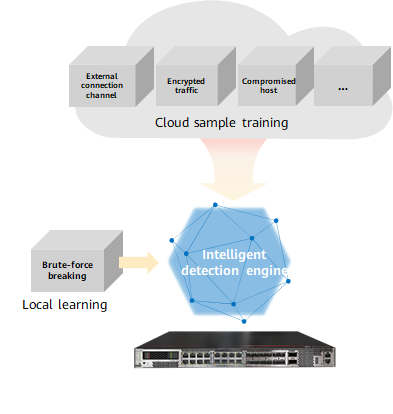
The detection models used by the intelligent detection engine come from the following:
- Cloud Sample Training (Supervised Learning)
The cloud uses supervised learning to train millions of samples, extracts threat detection models, and delivers the models to firewalls for detection.
- Local Learning (Unsupervised Learning)
Unsupervised learning is used locally, and the learning is performed continuously by extracting data from live network traffic.
Supervised learning and unsupervised learning can more effectively detect malicious files that are frequently mutated, detect compromised hosts and remotely controlled zombies, monitor encrypted data that is sent and stolen, and identify malicious behavior, such as slow and distributed brute force attacks. During the learning process, mass data analysis is leveraged to train and generate threat detection models, and the models are continuously optimized based on live network data for self-evolution. The updated model trained on the cloud is delivered directly to a firewall without the need to upgrade system software.
AI firewall intelligent detection engine
An advanced threat is often an organized and planned attack process. The AI firewall provides multiple technologies designed to block attacks on key kill chain nodes:
- External penetration phase: The first step of an attack is to spread malicious files to the intranet through phishing emails and USBs. The kill chain is interrupted once the spread of malicious software is blocked on the node.
The AI firewall leverages the intelligent malicious-file detection algorithm to extract file features, instead of using the traditional static rule database to detect malicious files, greatly improving the detection rate.
- Interaction between an attacker and a compromised host: A host that executes malware becomes a compromised host. An attacker communicates with the compromised host through a command and control (C&C) channel. For example, the attacker sends instructions to the compromised host, and the compromised host sends data.
The AI firewall provides C&C channel detection and Domain Generation Algorithm (DGA) based domain name detection to block unauthorized communication. To hide the communication process, C&C traffic is usually encrypted for transmission. The AI firewall can detect encrypted traffic without decryption, ensuring that C&C traffic cannot be hidden.
AI Firewall Products
In 2018, Huawei launched the mid- and low-end USG6000E series AI firewalls, followed by high-end USG12000 series AI firewalls and the new-generation mid- and low-end USG6000F series AI firewalls. The AI firewalls are equipped with the intelligent detection engine to detect advanced threats and is able to detect those concealed threats in encrypted traffic without decrypting the traffic. With the built-in dedicated hardware processing engine, the AI firewalls provide high threat detection performance.

Huawei AI firewall products
For more information, see Huawei AI Firewall Product Documentation.
- Author: Liu Shui
- Updated on: 2023-11-22
- Views: 19330
- Average rating:







