What Is a Brute Force Attack?
A brute force attack deciphers passwords by cycling through them individually until the actual password is found. For example, if a 4-digit password containing just digits involves a maximum of 10,000 combinations, it can be decrypted within a maximum of 10,000 attempts. For a password that is manually set (a non-random password is manually set, with a rule that can be followed), a password dictionary (for example, a rainbow table) may be used to search for a frequently used password, greatly shortening the cracking time.
Setting long and complex passwords, using different passwords in different places, avoiding the use of personal information as passwords, and periodically changing passwords are effective methods to defend against brute force attacks.
Methods Used to Initiate Brute Force Attacks
Exhaustive Attack
The exhaustive attack refers to generating a set of all possible passwords based on a preset password length and a selected character set, and performing a blanket search in the password set. For example, if a 4-digit password containing just digits involves a maximum of 10,000 combinations, it can be decrypted within a maximum of 10,000 attempts. While this method can theoretically be used to crack any password, the time required to do so increases exponentially as passwords grow in complexity.
The exhaustive attack can be used to guess a randomly generated SMS verification code and the like, since the possibility of occurrence of various randomly generated passwords is the same and is not affected by human memory.
Dictionary Attack
The most frequently used passwords are stored in a file, which is known as a dictionary. A dictionary attack involves an attacker trying every password in the dictionary in an attempt to uncover the real one.
The dictionary attack is usually used to guess manually set passwords. The possibility of using such a password is related to how easy it is to memorize. 12345678 and "password" are more likely to be used as a password than fghtsaer. The dictionary attack has a slightly lower hit rate but takes less time than the exhaustive attack.
Rainbow Table Attack
A rainbow table attack is a type of dictionary attack that can effectively crack hash algorithms, such as MD5, SHA1, and SHA256/512.
To enhance security, a website does not store user passwords directly in a database. Instead, the website hashes each password into a string of meaningless characters. The hash algorithm is irreversible, meaning no decryption algorithm can be used to restore the original passwords. There are two methods to crack a hashed password. One is to try all possible combinations of a password using the exhaustive key search, and then compare each result with the target hashed value using the hash encryption algorithm, which is extremely time consuming. The other method is to generate a mapping table of all possible passwords and corresponding recomputed hash strings in advance, which is space consuming. For example, if a password is an alphanumeric string of 14 characters, the mapping table of passwords and 32-digit hash strings occupies a storage space of 5.7 x 1014 TB.
A rainbow table is a time-space tradeoff method. The core idea is to hash a cleartext string to obtain a hashed value, use the reduction function to compute the hashed value to obtain another cleartext string, and repeat the preceding steps to generate a hash chain. Then only the start and end strings in the hash chain is stored in the table, with the middle strings deleted. As such, the storage space to be consumed is reduced by half, and the number of calculation times does not increase greatly. Various reduction functions are used to compute hash chains, with each chain represented by a different color, leading to a rainbow effect. Hence the name is "rainbow table".
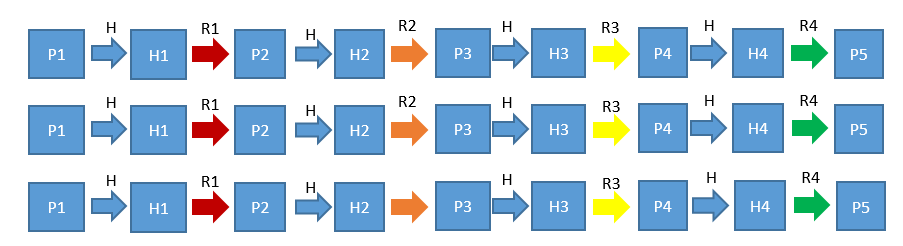
Rainbow table
When using the rainbow table to crack passwords, even an ordinary PC can reach an astonishing speed of more than 100 billion times per second. To improve security, a string may be hashed multiple times. For example, MD5 is performed again after a previous MD5 process. Also, a device adds a string (which is called salt) at the beginning and end of an original password to increase the password length, and then performs the hash operation. All the results can be added to the rainbow table. The most complete rainbow table can be used to crack about 99.9% of existing passwords on the Internet.
What Is Most Vulnerable for a Brute Force Attack?
Many people set passwords that are too simple, such as phone numbers, dates of birth, names of relatives or pets, or the same password on different websites, which makes the passwords easy to crack.
At the end of 2020, NordPass published the 200 most commonly used passwords for that year. The password offenders are 123456, 123456789, "password", 12345678, 111111, 123123, 12345, 1234567890, 1234567, 000000, 1234, and so on. Other commonly used passwords involve combinations of digits and letters, such as qwerty, abc123, and picture1.
Brute force attacks do not cause direct intrusion but are used by attackers to obtain the accounts and passwords of systems and users to prepare for subsequent intrusions. In the context of individuals, attackers may intend to steal money or identities, the latter of which can lead to even further financial losses. For enterprises, attackers use brute force attacks to access the Telnet, POP3, and MySQL services. Successful access may lead to high-risk events, such as user information leakage, file sharing, email leakage, or email sending failures.
Methods Used to Protect Against Brute Force Attacks
Manual Optimization: Enhancing Password Security
- Increase the password length and complexity.
A password should consist of digits, uppercase letters, lowercase letters, and special characters. The longer a password is, the longer the time is taken to crack the password. If a password exceeds a certain length, it cannot be cracked by brute force attacks. For example, a server cluster can make a maximum of 350 billion attempts per second. It takes only 4.08 seconds to crack a 6-digit password, 6.47 minutes to crack a 7-digit password, 10.24 hours to crack an 8-digit password, 40.53 days to crack a 9-digit password, and 10.55 years to crack a 10-digit password.
- Use different passwords in different places.
Repeated use of the same password for e-mail, banking, and social media accounts is more likely to result in identity theft. The abbreviation of a website name can be used as the suffix of a password. In this way, an independent password is used at each website and is not easy to forget.
- Do not use words from the dictionary, digit-only combinations, combinations of adjacent keys on a keyboard, or strings of repetitive characters.
For example, do not use "password", 12345678, asdfg, aaaa, or 123abc.
- Avoid setting passwords comprised of people's names, non-confidential personal information (phone number, date of birth, and so on), or names of relatives, children, or pets. When we click on the "Forgot Password" link at some websites, the system sometimes asks a series of private questions. However, the answers are usually found in our social media profiles, making the accounts easier to crack.
- Regularly change passwords.
System Enhancement: Brute Force Cracking Prevention Design for Passwords
The following techniques can be used during system design:
- Lockout policy: A user is temporarily locked if the user enters incorrect passwords for a specified number of times.
- Verification code: Users can log in to the system only after completing simple tasks, which can be easily completed by users but cannot be completed by brute force tools. For example, a graphic verification code or SMS message confirmation is required.
- Password complexity requirement: Users are forced to set a long and complex password and change the password periodically.
- Two-factor authentication: Two authentication factors are combined to authenticate users. For example, any two of the following are combined: the password, ID card, security token, fingerprint, facial recognition, and geographic information.
How Does Huawei HiSec Insight Defend Against Brute Force Attacks?
Huawei has launched the HiSec Insight Advanced Threat Analysis System, a big data-based APT defense product. This system not only effectively defends against brute force attacks, but also traces the intent of brute force attacks to prevent potential risks.
The HiSec Insight collects massive basic network data, such as network traffic and network and security logs of various devices. Based on real-time and offline big data analysis, the HiSec Insight intuitively displays analysis information about threat events, such as brute force attacks. Users can make decisions based on the analysis information and take appropriate measures, such as containment, source tracing, and cleaning, to efficiently handle threats in a closed-loop manner.
Analysis and evidence collection: The HiSec Insight can intuitively display the number of brute force attacks within a time window (for example, 20 seconds). The HiSec Insight reports an alarm to alert to a threat event, if the number of brute force attacks complies with the brute force attack behavior (for example, the number of consecutive authentication times exceeds 8 within a short period of time) and the login is successful after the brute force attack is initiated.
Containment: Configure an IP address blacklist on a firewall to block the attack source hosts used to launch brute force attacks. For successful brute force attacks, disconnect the network connections to the threatened hosts to prevent continuous spread of attacks.
- Source tracing: View the historical attack events of the threatened host and check whether there are other abnormal behaviors, such as scanning events.
- Cleaning: To deal with successful brute force attacks, change account passwords to prevent such events from happening again, and use terminal antivirus software to scan all disks and kill viruses.
- Prevention: Strengthen password management for open services. For example, require users to set strong passwords and periodically change them. It is recommended that intrusion detection devices or firewalls be deployed at the network ingress to enhance protection.
- Author: Jiao Cuicui
- Updated on: 2021-09-30
- Views: 10406
- Average rating:






