What Is Network Admission Control (NAC)?
The NAC solution implements security control over access users to provide end-to-end security. The solution allows only authorized users and secure terminals to access the network, isolates unauthorized and insecure users and terminals, or allows only authorized users and terminals to access limited resources. In this way, the security protection capability of the entire network is improved.
What Is the Purpose of NAC?
On a traditional enterprise network, the intranet is typically considered secure and security threats mainly come from external networks. Therefore, various security measures, such as deploying firewalls, are taken to defend against external attacks. However, many major security vulnerabilities often occur on the intranet. For example, when employees on the campus browse some websites, malicious software such as spyware and Trojan horses may be downloaded to computers and spread on the intranet, causing serious security risks. On a campus network, the security status of any terminal affects the security of the entire network. The security status refers to the antivirus capability, patch level, and system security settings. In addition, when a large number of unauthorized access users exist on the campus network, the service system may be damaged and critical information assets may be leaked.
The NAC solution can effectively manage network access rights, update system patches in a timely manner, and upgrade the antivirus database. This allows administrators to quickly locate, isolate, and repair insecure terminals, meeting intranet security requirements of the campus network.
What Are the Capabilities of NAC?
NAC provides the following capabilities.
Identity Authentication
- After a user with a secure terminal enters the correct user name and password, the user can be normally connected to the network.
- A user with an insecure terminal can only be connected to the network isolation domain and then connected to the network after terminal security is repaired.
- Unauthorized users are not allowed access to the network.
Access Control
Users can be precisely matched based on the user identity, access time, access location, terminal type, terminal source, and access mode (5W1H for short) to control the resources available to users. The following explains 5W1H:
Who are connected to the network (employees or guests)?
Whose devices (enterprise devices or BYOD devices)?
What devices (PCs or mobile phones) are used?
When is the access initiated (during working hours or non-working hours)?
Where is the access initiated (in the R&D area, in a non-R&D area, or at home)?
How do devices access the network (through wired or wireless networks)?
Terminal Security Check and Control
- Scans terminals before they are connected to the network to obtain their security status, for example, antivirus software installation, patch update, and password strength.
- Associates with the NAC device to block the terminals that do not pass security check. This prevents damages to the service system and helps terminals complete automatic security issue repair.
- Denies network access of terminals whose security problems cannot be repaired in a timely manner.
System Repair and Upgrade
The NAC solution provides automatic and manual system repair and upgrade functions. It can automatically download and upgrade system patches, trigger antivirus database updates, and enforce security measures such as killing illegal or violating processes.
How Does NAC Work?
The NAC solution consists of three key components: security terminal, NAC device, and server system.
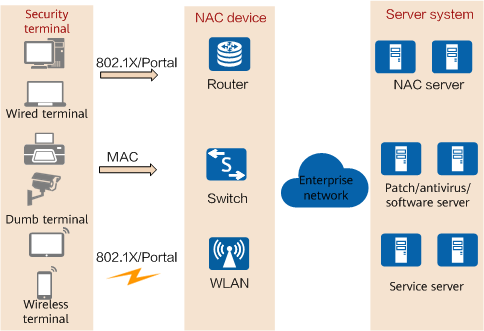
Components of the NAC solution
- Security terminal: is the software installed on the user terminal system. It authenticates user terminals, evaluates the security status, and implements security policies on user terminals.
- NAC device: enforces security policies, that is, allowing, rejecting, isolating, or restricting the access of users based on the security policies customized for enterprise networks.
The Huawei NAC solution supports multiple authentication modes, including 802.1X authentication, MAC address authentication, and Portal authentication. In these authentication modes, the NAC device assists authentication between a user terminal and NAC server. The NAC device can be a switch, router, access point (AP), or other security device. It authenticates access users forcibly, rejects the access of unauthorized users, and isolates insecure terminals to provide network services only for authorized users and secure terminals.
- Server system: consists of the NAC server, antivirus/patch/software server, and service server.
The NAC server is the core of the NAC solution. Users can access the NAC server before passing identity authentication and security check. The NAC server authenticates users, performs security audits on users, implements security policies on users, and associates with the NAC device to deliver user rights. If a user passes identity authentication but fails terminal security check, the user usually accesses the antivirus/patch/software server to automatically update the antivirus database on the terminal and install as well as update the patches of the operating system and application software to meet the terminal security check requirements. The service server is used for enterprise service management. Only authenticated and authorized users can access the service server.
For example, on an enterprise network, users are classified into employees, partners, and guests. The NAC solution allows customizing network access and permission control rules for different user roles.
- Employees: refer to those who have fixed office locations and long-term work contracts. Employees typically use company devices as office devices. Company devices often have security terminals installed before employees obtain the devices. After passing authentication, employees have sufficient access rights to the company network.
- Partners: refer to those who frequently move and are under few enterprise constraints. These personnel are connected to the enterprise network for a certain period of time and access some servers on the network. Partners usually use the company devices that have security terminals installed. However, the rights of partners must be strictly controlled because their terminal security is low.
- Visitors: refer to those who are connected to enterprise networks temporarily. Typically, visitors are wirelessly connected to the enterprise network and can only access the Internet through the enterprise network. Visitors are strictly isolated from employees and partners to prevent enterprise information asset leakage.
NAC Applications
The Network Admission Control (NAC) solution can be applied to many network scenarios, such as enterprise campus network, bring your own device (BYOD), Internet of Things (IoT), and public Wi-Fi network scenarios.
Enterprise Campus Network
The NAC solution strictly differentiates network access rights of employees and non-employees based on user roles on an enterprise network.
BYOD
To meet employees' pursuit of new technologies and personalization and improve their work efficiency, many enterprises start to consider allowing employees to connect to the intranet using their own smart devices (such as mobile phones, tablets, and laptops). This is called BYOD. Generally, no security terminal is installed on employees' own devices. Accessing the enterprise intranet through these devices may bring security risks. The NAC solution uses the terminal type identification technology to automatically identify the types of devices that employees use to connect to the enterprise intranet. This implements authentication and authorization based on user information, device type, and device operating environment.
IoT
Most IoT devices do not support traditional authentication protocols or security certificates. The NAC solution automatically identifies IoT devices based on their electronic identity information (including the device version, vendor information, version number, product name, and terminal type), and completes network access authentication for the IoT devices based on the configured security policies.
Public Wi-Fi Network
Public Wi-Fi networks are widely used. Almost all cafes, shops, airports, hotels, and other public places provide public Wi-Fi access for their customers and guests. A completely open public Wi-Fi network has low security. This is because anyone can log in to the network without identity authentication. Therefore, exercise caution when connecting to the network. NAC provides WeChat authentication and SMS authentication. When a user accesses a public Wi-Fi network, the user can scan the QR code through WeChat or enter the mobile number on the web portal page to access the network using the real name.
- Author: Dou Cuicui
- Updated on: 2024-02-27
- Views: 17807
- Average rating:






