What Is Network Slicing?
Network slicing is a new network architecture that provides multiple logical networks on the same shared network infrastructure. Each logical network serves a specific service type or industry user. Each network slice can flexibly define its logical topology, SLA requirements, reliability, and security level to meet differentiated requirements of different services, industries, or users.
Network slicing enables carriers to reduce the cost of constructing multiple private networks and provide highly flexible network services that can be scheduled and allocated on demand based on service requirements. This improves the network value and monetization capability of carriers and facilitates digital transformation of various industries.
Why Do We Need Network Slicing?
With the emergence of diversified new services in the 5G and cloud era, different industries, services, or users pose various service quality requirements on networks. For example, mobile communication, environment monitoring, smart home, smart agriculture, and smart meter reading require huge numbers of device connections and frequent transmission of many small packets. Other examples are live streaming, video uploading, and mobile healthcare services, which require higher transmission rates; and Internet of Vehicles (IoV), smart grid, and industrial control services, which require millisecond-level latency and near-100% reliability. As such, 5G networks must provide capabilities such as massive access, deterministic latency, and ultra-high reliability. Flexible and dynamic networks need to be built to meet diversified service requirements of users and vertical industries.
To meet the preceding requirements, network slicing is introduced. With network slicing, carriers can build multiple dedicated, virtualized, and isolated logical networks on a general physical network to meet differentiated requirements of different customers for network capabilities. The following figure shows an example of 5G network slicing.
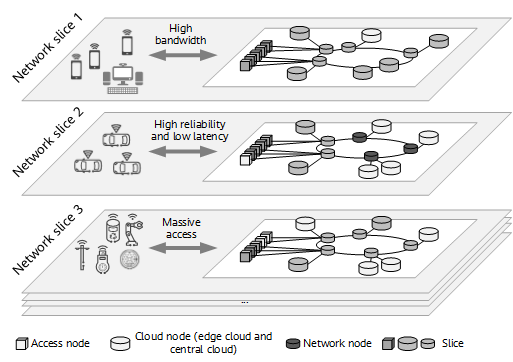
Example of 5G network slicing
5G E2E network slicing cover the RAN, mobile core network, and IP transport network slicing. The network slicing architectures and technical specifications of the RAN and mobile core network are defined by 3GPP, whereas those of the IP transport network are mainly defined by the IETF, BBF, IEEE, and ITU-T. The following sections focus on IP transport network slicing.
In 5G E2E network slicing, the IP transport network slices mainly provide customized network topology connections between network elements and between services in the RAN and core network slices; but not only this, they also provide differentiated SLA guarantee for services of different slices. Another thing the IP transport network needs to provide is open network slice management interfaces for slice lifecycle management. In this way, it can work with the RAN and core network for E2E collaborative slice management, as well as providing network slices as a new service to tenants of verticals.
What Benefits Does Network Slicing Bring?
The benefits of IP transport network slices are mainly reflected in four aspects: resource and security isolation, deterministic latency, flexible topology connection customization, and automated slice management.
Resource and Security Isolation
From the perspective of service quality, the purpose of network slice isolation is to prevent a service burst or abnormal traffic in a slice from affecting other slices in the same network, which ensures that services in different network slices do not affect each other. This is especially important for services such as smart grid, smart healthcare, and smart port, which have strict requirements on latency and jitter and whose performance is highly sensitive to impact from other services. From the perspective of security, if information about services (private line services, such as finance and government services) or users in a network slice is not expected to be accessed or obtained by users in other network slices, effective security isolation measures need to be taken between different slices.
Based on the degree of isolation, IP transport network slices provide three levels of isolation: service, resource, and O&M isolation.
- Service isolation: Service packets in one network slice will not be sent to service nodes in another network slice on the same network in any way. In other words, service connections are isolated between different network slices, making services of different tenants invisible to each other on the same network.
- Resource isolation: Network resources used by one network slice are isolated from those used by another network slice. Resource isolation includes hard isolation and soft isolation, which differ in the degree of isolation. Hard isolation ensures that slices are provided with exclusive network resources, preventing any interference between services. Soft isolation, on the other hand, allows each slice to use both a set of dedicated resources and the resources shared with other network slices. The benefit of soft isolation is that services are isolated to some degree, without having to sacrifice certain statistical multiplexing capabilities. By mixed use of hard and soft isolation, carriers can select the optimal combination of network slices to meet their resource requirements. This allows a single physical network to meet differentiated service SLAs.
- O&M isolation: In addition to service isolation and resource isolation, some tenants require independent O&M of network slices allocated by carriers, similar to using private networks. Network slicing provides O&M isolation through the openness of interfaces on the management plane.
Deterministic Latency
Different services have different requirements on bandwidth and latency. Traditional services have low requirements on network E2E latency, which is typically greater than 100 ms. However, real-time interactive and industrial control services, such as differential protection services for power grids, require a latency of 2 ms on an IP transport network. In addition, the network must provide deterministic and committed latency assurance. Network slicing enables different services to be deployed in different slices, providing deterministic latency assurance for interactive and control services.
Flexible Topology Connection Customization
Services and traffic evolve from a single to multiple directions, resulting in more flexible, complex, and dynamic network connections.
Network slicing can provide customized logical network topologies and connections for different industries, services, or users, meeting differentiated network connection requirements. Users in a network slice only need to be aware of the network slice's logical topology and connection instead of the basic network's full topology. In addition, services in a network slice are limited to be deployed in the topology corresponding to that network slice. This simplifies the network information that needs to be perceived and maintained for network slice users. For carriers, excessive internal information of basic networks is prevented from being exposed to network slice users, improving network security.
Automated Slice Management
As service types and scales continuously increase, network management complexity increases rapidly. As such, managing networks manually is not a feasible option. Instead, managing networks dynamically and efficiently calls for automatic network management technologies.
The network slice manager provides full lifecycle management for network slices; streamlines the entire process from user intent to service provisioning; supports network slice planning and deployment, flexible mapping from services to slices, real-time visualization of slice services, and dynamic adjustment and optimization of slices; and provides tenant-level refined service management.
As network management automation continuously develops, intelligence technologies may be widely used in each phase of network slice management to implement intelligent network management.
How Does Network Slicing Work?
Network Slicing Architecture
As shown in the following figure, the IP transport network slicing architecture can be divided into three layers: network slice forwarding layer, network slice control layer, and network slice management layer.
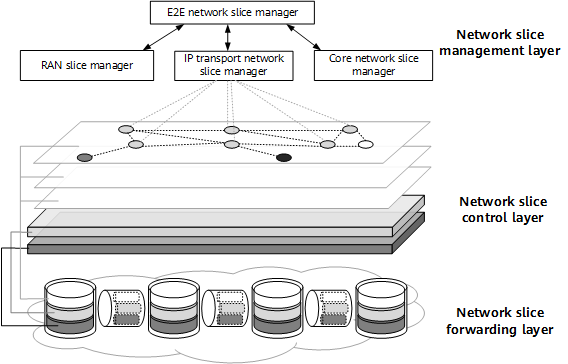
IP transport network slicing architecture
Network slice forwarding layer
The network slice forwarding layer needs to have flexible and refined resource reservation capabilities and needs to be capable of dividing the physical network's forwarding resources into multiple sets of isolated resources that are allocated to different network slices. Such resource isolation can be achieved using methods such as FlexE sub-interfaces, channelized sub-interfaces, and HQoS.
Network slice control layer
The network slice control layer provides different logical network slice instances on a physical network and customized logical topology connections, and associates the logical topologies of slices with the set of network resources allocated to the slices. In this way, network slices are formed to meet specific service requirements. The control layer can be further divided into control and data planes. The control plane mainly distributes, collects, and calculates network slice information, whereas the data plane identifies and forwards network slice resources. Current common technologies used at the control layer include SRv6 and Flex-Algo.
Network slice management layer
The network slice management layer provides network slice lifecycle management functions, including network slice planning, deployment, maintenance, and optimization.
Network Slice Address Identification
The most significant change network slicing brings is evolving a traditional physical network plane into a three-dimensional network with many logical networks. A traditional two-dimensional network allocates a unique IP address to each network node to identify this network node. When packets are being forwarded, IP addresses are used to identify network nodes. This identification method causes great trouble in a three-dimensional network. Different slices may have different forwarding paths or network resources, and an IP address needs to be allocated to each node in each slice for identification. For example, if there are 1000 network nodes and 200 network slices need to be created, 200000 IP addresses need to be planned, which brings great challenges to network deployment complexity and network performance.
To resolve the address identification problem of network slices, two-dimensional address identifiers are introduced. The IP address of a network physical node and a slice ID are used to uniquely identify a logical node in the network slice. In this way, regardless of the number of network slices planned for a network, only one set of address identifiers is required. As such, deploying network slices does not require additional address planning or configuration. In addition, using a two-dimensional address identifier can also greatly reduce the number of routes in a slice network to better support a large number of network slices.
Two-Dimensional Address Identifier Forwarding Process of a Network Slice
For a slice ID-based network slice, a device needs to generate two forwarding tables: one is a routing table, which is used to determine the outbound interface based on the destination address of a packet; the other is a slice interface's slice ID mapping table, which is used to determine a slice's reserved resources (which can be sub-interfaces or channels) on the interface based on the slice ID in a packet. After a service packet reaches a device, the device searches the routing table based on the destination address to obtain the outbound interface, searches the slice interface's slice ID mapping table based on the slice ID to determine reserved resources (sub-interfaces or channels) on the outbound interface, and then uses the corresponding sub-interface or channel to forward the service packet.
How Are Network Slices Managed?
As shown in the following figure, network slices are managed in four phases: planning, deployment, maintenance, and optimization.
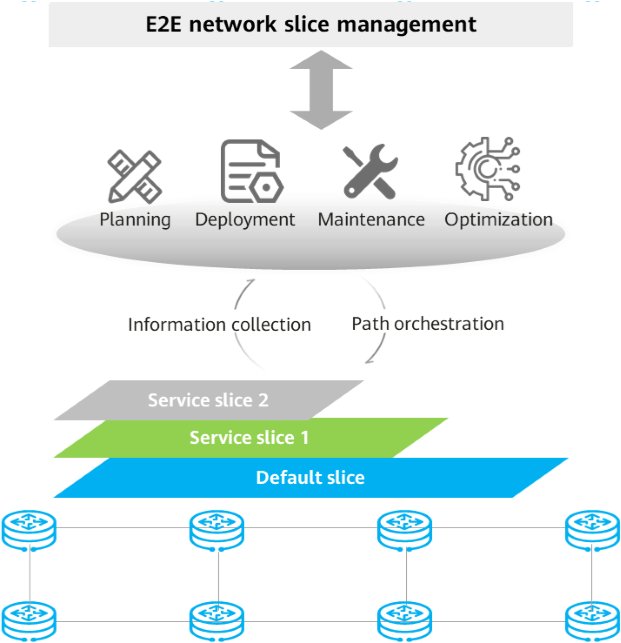
Network slice lifecycle management
Slice planning: According to service assurance requirements, the slice planning phase focuses on slice scope, bandwidth, and latency planning.
- Scope planning: Defines a slicing scope, which can be flexible or cover the entire network or a specific area. Scope planning resolves issues in slice interface bandwidth usage and network load balancing.
- Bandwidth planning: Defines rules for bandwidth usage in slices. For a shared slice (for example, an industry slice), the ratio of the slice bandwidth to the network-wide bandwidth needs to be defined. For a dedicated slice, an absolute bandwidth value needs to be defined.
- Latency planning: Specifies the network latency range.
Slice deployment: A controller is used to deploy slice instances, including creating slice interfaces and configuring slice bandwidth, VPNs, and tunnels.
- Create a network slice on the controller. The slice interface type can be a physical interface, FlexE interface, or channelized sub-interface.
- Activate the network slice to generate its basic configurations, including configuring the slice interface's IP address and enabling IGP. The device reports the slice's Layer 3 topology to the controller through BGP-LS.
- Deploy an SRv6 path in the slice.
- Deploy VPNs (such as L3VPN and EVPN L2VPN) in the slice.
Slice maintenance: The controller uses technologies such as iFIT to monitor service latency and packet loss. Telemetry technology is used to report a network slice's traffic volume, link status, and service quality information, displaying the network slice status in real time.
- Slice visualization: monitors information such as network slice traffic volume, link status, and service quality, comprehensively displays the network status, and provides a network slice profile.
- Fault diagnosis and prediction: monitors the network slice status in real time, proactively analyzes the root causes of network faults, and predicts possible network faults.
- Fault rectification: automatically takes measures (such as path adjustment and optimization) to rectify faults in traffic congestion and fault scenarios.
Slice optimization: Based on SLA requirements, seek the optimal balance between slice network performance and network costs. Slice optimization is implemented through bandwidth optimization and slice capacity expansion.
- Bandwidth optimization: If there are sufficient resources in a slice but insufficient partial bandwidth resources, bandwidth optimization can be used to guarantee bandwidth.
- Slice capacity expansion: If a slice is overloaded and the service bandwidth cannot be assured through optimization, the slice capacity needs to be expanded.
- Author: Liu Xiaoyang
- Updated on: 2021-11-04
- Views: 24427
- Average rating:







