What Is PPPoE? What Problems Does PPPoE Solve?
PPPoE is the point-to-point protocol running over the Ethernet at the link layer. It provides PPPoE connections on the Ethernet, sets up PPP sessions, and encapsulates PPP frames into PPPoE frames. PPPoE connects users to a remote access device, providing cost-effective user access and excellent user access control.
PPPoE supports remote access to multiple user hosts over an Ethernet and provides accounting data for transmission to resolve application issues, such as Internet access charging issues. PPPoE is therefore widely used for carrier network access.
What Problems Does PPPoE Solve?
PPP is a point-to-point protocol, meaning that one node can access only one another specified node. PPP is located at the second layer of the Open Systems Interconnection (OSI) reference model and the data link layer of the TCP/IP model. It is mainly used for point-to-point data transmission over full-duplex asynchronous links. An important function of PPP is identity authentication. Although PPP supports identity authentication for both communication parties, it does not provide address information. Because Ethernet is a broadcast multi-access network, PPP cannot be directly applied to Ethernet links.
Despite the characteristics of Ethernet technology, such as easy-to-use and cost-effective, the attributes of the Ethernet broadcast network make it impossible for two communication parties to authenticate each other's identity. As such, the communication is insecure.
How can we solve the preceding problems while at the same time ensuring low-cost network operations based on the existing network structure? The answer is the PPPoE technology. PPPoE integrates PPP's function of authenticating the identities of the two communication parties. Based on the PPP networking structure, PPP frames are encapsulated into PPPoE frames to implement point-to-point communication on an Ethernet. In this way, clients on the Ethernet can be connected to the remote broadband access device.
PPPoE Characteristics
PPPoE provides the following characteristics:
- PPPoE integrates the advantages of PPP and implements functions such as identity authentication, encryption, and compression unsupported by traditional Ethernet.
- PPPoE uses unique session IDs to ensure user security.
In terms of applications:
- PPPoE dial-up is the most common method of enabling terminals to connect to the ISP network for broadband access.
- PPPoE can be used on Ethernet cables, such as cable modems and digital subscriber lines (DSLs), to provide access services for users through Ethernet protocols.
Simply put, PPPoE combines the cost-effectiveness of Ethernet with the manageability and controllability of PPP to provide Internet access. For carriers, it can fully utilize the current architecture of the telecommunication access network and the current dial-up network resources, without requiring major changes in the operations and management modes. For users, they obtain a similar experience to that obtained using the original dial-up Internet access.
How Is a PPPoE Connection Established?
This section describes the PPPoE packet structure and the stages of PPPoE connection establishment.
PPPoE Packets
Before learning about PPPoE connection establishment, you need to understand the PPPoE packet structure. A PPPoE packet is a PPP packet encapsulated in an Ethernet frame. The following figure shows the packet encapsulation structure.
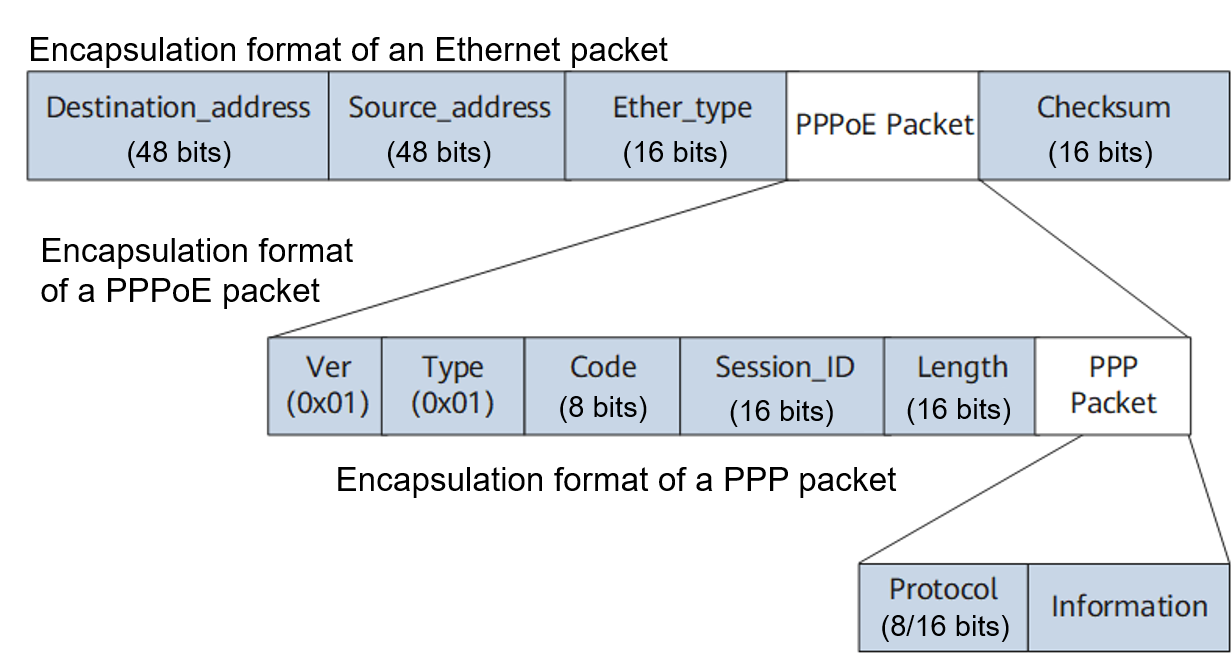
Structure of a PPPoE packet
Field |
Description |
|---|---|
Ver |
Indicates a PPPoE version number. This field is 4 bits long and must be set to 0x1. |
Type |
Indicates a PPPoE type. This field is 4 bits long and must be set to 0x1. |
Code |
Indicates a PPPoE packet type. This field is 8 bits long. The value can be: 0x00 (session data), 0x09 (PADI packet), 0x07 (PADO or PADT packet), 0x19 (PADR packet), and 0x65 (PADS packet) |
Session_ID |
Indicates a PPP session ID. This field is 16 bits long. The value is fixed for a given PPP session and defines a PPP session along with Ethernet source and destination addresses. A value of 0xffff is reserved for future use and must not be used. |
Length |
Indicates the length of the PPPoE payload. This field is 16 bits long, excluding the length of the Ethernet and PPPoE headers. |
Stages of PPPoE Connection Establishment
Before learning about the stages of PPPoE connection establishment, you need to understand the roles involved in the PPPoE network architecture.
PPPoE adopts the client/server model. As shown in the following figure, the basic roles in PPPoE networking are the PPPoE client, PPPoE server, and RADIUS device.
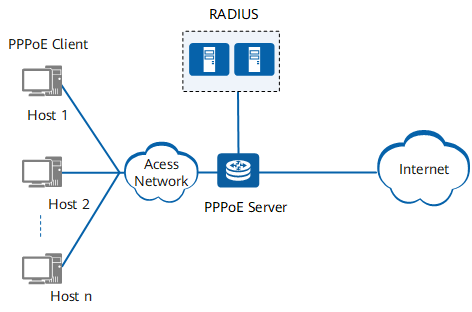
Networking diagram of PPPoE access
The process in which a PPPoE user goes online involves two stages: discovery stage and PPP session stage. In the discovery stage, a PPPoE server is selected and the ID of the session to be established is determined. The PPP session stage refers to the standard PPP process, including LCP negotiation, PAP/CHAP authentication, and NCP negotiation.
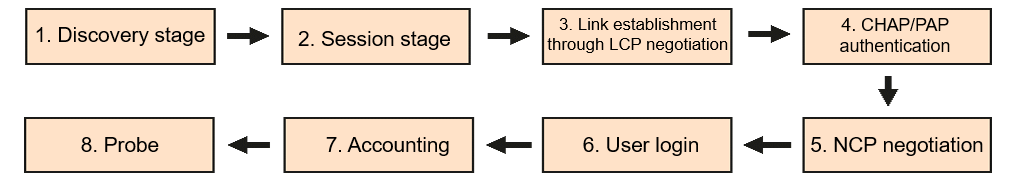
Working process of PPPoE
The following figure shows the time sequence of the PPPoE discovery and PPP session stages.
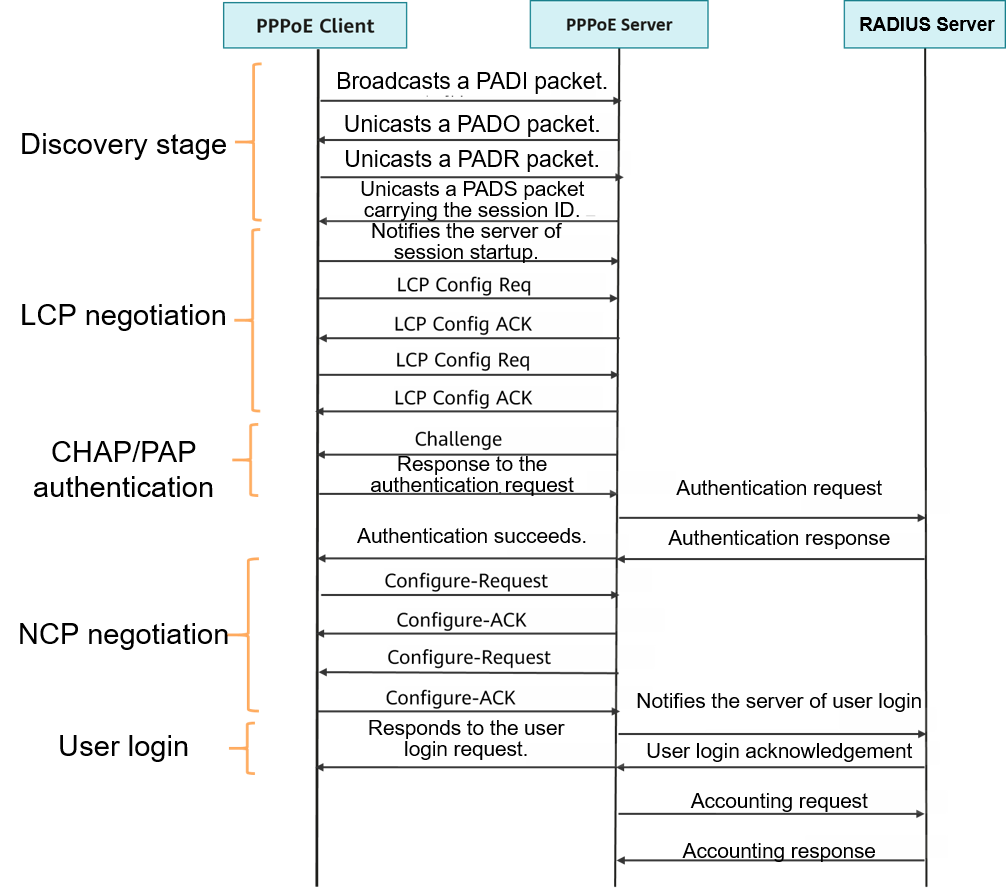
Time sequence of the PPPoE discovery and PPP session stages
Discovery stage
In the discovery stage, the device allocates a session ID to the user. The session ID identifies a PPPoE virtual link between the user and the device.
- The PPPoE client broadcasts a PPPoE Active Discovery Initiation (PADI) packet carrying the type of the service being requested.
- After receiving the PADI packet, all PPPoE servers on the Ethernet compare the requested service in the packet with the services that they can provide. The PPPoE server that can provide the requested service responds with a PPPoE Active Discovery Offer (PADO) packet.
- The PPPoE client may receive PADO packets from multiple PPPoE servers. The PPPoE client selects a qualified PPPoE server among those that return PADO packets based on certain conditions. The client then sends a PPPoE Active Discovery Request (PADR) packet back to the selected server. The PADR packet carries information about the requested service.
- After receiving the PADR packet, the selected PPPoE server generates a unique session ID to identify the PPPoE session between the PPPoE server and PPPoE client. The PPPoE server replies to the PPPoE client with a PPPoE Active Discovery Session-confirmation (PADS) packet carrying the unique session ID. If no error occurs, the PPPoE server enters the PPP session stage. The PPPoE client also enters the PPP session stage if no error occurs after it receives the PADS packet.
PPP session stage
The PPP session stage includes LCP negotiation, PAP/CHAP authentication, and NCP negotiation.
- LCP negotiation
After the PPP session stage is entered, LCP negotiation starts. The LCP negotiation process is as follows:
- The PPPoE client and PPPoE server send LCP Configure-Request packets to each other.
- After receiving the Configure-Request packet, the client and server respond based on the negotiation options in the packet (For details, see the following table.) If both ends reply with a Configure-ACK packet, the LCP link is successfully established. Before this occurs, both ends keep sending LCP Configure-Request packets.
- If both ends reply with a Configure-ACK packet within the specified LCP negotiation interval and before the timer for LCP negotiation expires, the LCP link is successfully established.
- If no Configure-ACK packet is received before the timer for LCP negotiation expires, LCP negotiation is terminated.
- After the LCP link is established, the PPPoE server periodically sends LCP Echo-Request packets to the PPPoE client and receives Echo-Reply packets from the PPPoE client to check whether the LCP link is normal.
Table 1-2 List of response packet typesResponse Packet Type
Description
Configure-ACK
If the LCP options received in a Configure-Request packet are all supported, the receive end replies with a Configure-ACK packet that carries the same LCP options as those in the Configure-Request packet.
Configure-NAK
If the negotiation options received in a Configure-Request packet are supported but some values are not acceptable, the receive end replies with a Configure-NAK packet that carries the expected values of the local device. For example, if the Configure-Request packet carries an MRU value of 1500 but the local end expects an MRU value of 1492, the receive end fills the MRU value 1492 in the Configure-NAK packet.
Configure-Reject
If negotiation options received in a Configure-Request packet are not supported, the receive end replies with a Configure-Reject packet that carries the unsupported options.
- PAP/CHAP authentication
After LCP negotiation is complete, the authentication stage starts. Two authentication modes are supported: PAP and CHAP.
PAP authentication
PAP is a two-way handshake protocol that authenticates users based on usernames and passwords. The usernames and passwords are transmitted in cleartext. The PPPoE server (or RADIUS server) checks whether the usernames and passwords are correct based on the local user table. This mode applies to environments with low network security requirements.
CHAP authentication
CHAP authentication is a three-way handshake protocol. It can be used by the PPPoE server (or RADIUS server) to check whether the username and password are correct based on the local user table. In CHAP authentication mode, only the username (and not the user password) is transmitted over the network. As such, CHAP authentication is more secure than PAP authentication.
- NCP negotiation
NCP negotiation mainly deals with network-layer parameters, such as IPCP and IPv6CP, in PPP packets. A PPPoE client mainly uses IPCP to obtain the IP address or IP address segment for network access.
The NCP negotiation process is similar to the LCP negotiation process. After NCP negotiation succeeds, the PPPoE client can normally access the network.
The PPPoE client automatically goes online upon successful NCP negotiation. In this case, the PPPoE server (usually a BRAS) sends an accounting request packet to the RADIUS server, which performs accounting for the PPPoE client.
What Are the Differences Between PPPoE and IPoE?
PPPoE and IPoE are the two most common user access modes in widespread use. This section describes the differences between PPPoE and IPoE.
IPoE is a user access mode in which IP packets are directly encapsulated and transmitted over an Ethernet. IPoE relies on DHCP (which does not provide functions such as link establishment, user authentication, or link monitoring) to provide IP addresses. IPoE combines DHCP and Extensible Authentication Protocol (EAP), such as web or 802.1x, to provide the same functions as PPPoE. For comparison details, see the following figure.
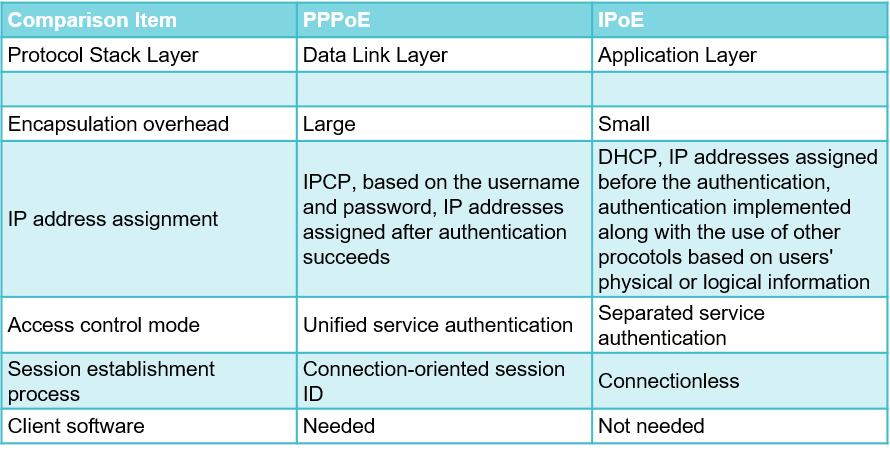
Comparison between PPPoE and IPoE
PPPoE authentication is easy to manage and has high security. However, it restricts the network application scope and multicast service development. As such, PPPoE is widely used in high-speed Internet (HSI) services and fiber broadband dial-up Internet access services, providing fast and convenient broadcast access for campus, enterprise, and home users. IPoE supports management of the validity period of IP addresses and can be easily configured on a LAN, without requiring client software. However, IPoE needs to work with other protocols to perform authentication. IPoE is widely used in IPTV and VoIP services.
In terms of security, IPoE requires the collaboration of the home gateway, network access device, and broadband network gateway. The security policies include anti-address spoofing, restriction on the number of terminals, anti-DoS, service isolation, suppression of unauthorized multicast sources, and port isolation. In IPoE multicast service scenarios, the multicast replication function can be implemented by devices close to users. As such, IPoE is widely used in Internet TV and voice services.
- Author: Huang Huixian
- Updated on: 2021-09-30
- Views: 35108
- Average rating:






