What Is Ransomware?
Ransomware, or ransom malware, is a type of malware that implements denial-of-access attacks. What makes ransomware unique is that it locks victims' computers or systematically encrypts files on the victims' hard disks until a ransom is paid.
Ransomware requires the victims to pay a ransom in return for regaining control of their computers or for receiving decryption keys required to decrypt the files. Ransomware is often spread through Trojan horses. Disguised as a legitimate file, it usually uses phishing emails or other social engineering methods to deceive victims into clicking links for downloading. Ransomware, like many other worm viruses, may also spread among computers on the Internet by exploiting software vulnerabilities.
Types of Ransomware
Differing in how victims' systems are controlled, ransomware can be classified into the following types:
- Kidnapping user data
User files or data is encrypted using an encryption algorithm (such as AES or RSA) and cannot be operated by users without the corresponding keys, even though users can access their devices.
Typical ransomware includes WannaCry, GlobeImposter, CryptoLocker, and TeslaCrypt.
- Locking user devices
User files are not encrypted, but users are denied access to their devices due to the modification of some configurations or system files.
Typical ransomware includes NotPetya.
- Locking user devices and kidnapping data
User files are encrypted, and user devices are locked. This type of ransomware is a combination of types 1 and 2.
Typical ransomware includes BadRabbit.
Ransomware Intrusion Methods
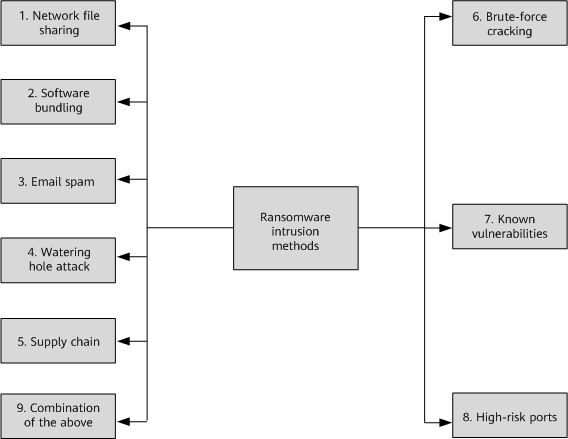
Figure 1-2 shows the common intrusion methods of ransomware.
- Network file sharing
Some ransomware is spread within a small scope through file sharing. Specifically, hackers upload the ransomware to, for example, shared network spaces, cloud disks, messaging groups, or online forums, and share the malware with specific people to trick them into downloading and installing it.
In addition, unscrupulous hackers often trick victims into closing the antivirus software by concocting excuses, such as stating that the antivirus software is unreliable and needs to be closed.
Typical examples include ransomware that is carried in external plug-ins or "green" software tools.
- Bundled propagation
Ransomware is bundled with legitimate software and posted on download websites or forums. Once users download the software, they become victims.
- Email spam
This is the most widespread form of ransomware attack.
- Social engineering techniques are used to send phishing emails, which disguise malicious scripts/programs as common files, and trick victims into downloading and running them.
- Botnets are sometimes used to increase the probability of users succumbing to deception. For example, the GameOver Zeus botnet uses a technique known as man-in-the-browser (MITB) to steal bank credentials and distributes phishing emails for ransomware such as CrytoLocker, making users more likely to become victims.
Typical examples include Locky, Cerber, GlobeImposter, and CrytoLocker.
- Watering hole attack
Extortionists exploit flaws in high-value, authoritative, or heavily visited websites to plant malicious code. When victims visit the sites or download related files, they get infected.
Typical examples include Cerber and GandCrab.
- Exploiting software supply chain
Ransomware makers intrude into software development, distribution, upgrade, or other stages. For example, during software development, they install viruses in product components, and infiltrate and hijack software download sites and upgrade servers. When users install software or upgrade services, they get infected with ransomware. Such a method exploits the trust between users and software vendors, and successfully bypasses the traditional security products. While this method is more covert, the harm is more serious. Petya, the global ransomware attack, for example, was spread by hijacking the Medoc software update service.
Typical examples include Petya.
- Brute-force cracking (directed attack)
For servers, individual users, or specific targets, permissions are illegally obtained by exploiting weak passwords, penetrations, and vulnerabilities. For example, NotPetya cracks passwords by brute force and is propagated on LANs.
Typical examples include NotPetya, Crysis, and GlobeImposter.
- Exploiting known vulnerabilities
Known vulnerabilities in systems or third-party software are exploited to launch attacks. WannaCry, for example, exploited a set of vulnerabilities in SMBV1 for attack and propagation.
Typical examples include WannaCry and Satan.
- Exploiting high-risk ports
The service mechanisms of some ports are exploited to find the port vulnerabilities for attacks. For example, WannaCry exploited the vulnerabilities in port 445 of the Windows operating system for propagation and featured self-replication and proactive propagation. Common high-risk ports include 135, 139, 445, 3389, and 5800/5900. Disabling these ports is recommended.
Such typical examples include WannaCry.
- Combination of the preceding methods
Usually, ransomware does not launch attacks or spread only in one way, but through a combination of several ways.
How Can We Prevent Ransomware Attacks?
The most effective way to prevent ransomware attacks is to prevent them from entering organizations.
Host Protection
First, it is recommended that hosts be centrally configured using an organization-level IT infrastructure solution. Measures such as utilizing the group policies of AD servers and the control center of the enterprise-edition antivirus software can ensure proper implementation of security actions without relying on employees to carry out operations.
Second, it is vital that employees are properly educated on information security. A large amount of ransomware uses emails or other social engineering techniques to lure employees into downloading malware or visiting malicious websites. Employees can avoid activating the attack media if they ignore the temptation. An effective method of preventing ransomware attacks is to promote information security and train employees to form good working habits, as well as to identify and prevent typical attacks.
The following lists the most important host protection measures. Most of them can be implemented centrally using the IT infrastructure solution. For small and micro enterprises that do not have a comprehensive IT system, employees can carry out these measures after receiving necessary training. The measures include but are not limited to:
- Enable the system firewall to block connections to specific ports or disable specific ports.
- Upgrade the antivirus software to the latest version or deploy a professional antivirus tool.
- Update patches to fix the vulnerabilities exploited by ransomware.
- Ensure that the user names and passwords used for login and authentication meet the complexity requirements.
- Set account lock policies.
- Prevent macros from running automatically and exercise caution when enabling macros.
- Download software only from approved locations.
- Do not open email attachments or links from unknown sources.
- Perform regular remote backups. This is the best way to ensure that data can be quickly restored after the system is infected, because local data may not be decrypted even if a ransom payment is made.
- Display file name extensions in Windows folders. This makes it easier to detect potential malicious files.
For details about host protection measures, see "Host Protection" in What Is Ransomware and How to Remove Ransomware?.
Network Protection
The key to prevent ransomware attacks is to intercept attacks before they enter the organization and cause substantial damage. The best solution is to set up a multi-layer security protection system based on firewalls, as attackers can easily break through a single-layer defense system. Strict security policies are the simplest and most effective protection measures. Only necessary services should be opened to external systems, and high-risk ports should be blocked to reduce risk exposure (attack surface). Blocking known threats forces attackers to create ransomware or exploit new vulnerabilities, increasing their attack costs. In addition, file filtering can be enabled to prevent high-risk files from entering networks, and URL filtering can be used to block malicious websites, preventing users from accidentally downloading malware. On a network requiring high security, the FireHunter, HiSec Insight, and deception system can be deployed to comprehensively detect security situation.
To prevent ransomware attacks on the network side, Huawei provides a layered defense system that:
- Deploys strict security policies on firewalls to restrict the use of networks and applications.
- North-south security policies: Strict network access policies are configured at the network border to open only necessary services to external systems and enable only trusted IP addresses or users to access necessary services.
- East-west security policies: The internal network is divided into different security zones based on functions and risk levels, and strict security policies are configured between the security zones. Blocking high-risk ports (such as ports 135, 137, 138, 139, 445, and 3389) or restricting accessible users is recommended to reduce the possibility of lateral spreading of ransomware. On network devices such as switches and routers, traffic policies can also be used to block high-risk ports.
- Detects and blocks known threats through the IPS, antivirus, and URL filtering functions.
- IPS: An IPS profile is referenced in the security policy to ensure that the action for brute-force cracking and vulnerability signatures is Block. If the default action for the signatures is not Block, you can configure an exception signature and change the action to Block.
- Antivirus: The default action is used for file transfer protocols (HTTP and FTP) and file sharing protocols (NFS and SMB). For mail protocols, setting the action to Declare or Delete Attachment is recommended. The firewall then adds a message to the emails to notify recipients that the attachment may contain viruses.
- URL filtering: It is recommended that the whitelist mechanism be used for determining the website types required by services. If the whitelist mechanism cannot be applied, malicious websites and other types of websites must be blocked and malicious URL detection enabled.
- Detects unknown threats through sandbox interworking.
A firewall is used to restore the traffic into files and send the files to the sandbox for detection. The firewall then periodically queries the detection result on the sandbox and updates the list of malicious files and URLs in the cache based on the detection result. When traffic with the same characteristics matches the list, the firewall directly blocks the traffic.
- Uses the HiSec Insight and deception system to prevent lateral spreading.
The HiSec Insight as well as switches and firewalls that support the deception feature are deployed. The deception system can induce ransomware to intrude on simulation services. After capturing the intrusion behavior, it reports the detection result to the HiSec Insight, which then delivers policies across the network to block the spread of ransomware. The deception system helps reduce the probability of attacks on the real system and minimize losses.
- Deploys a log audit system for investigation, evidence collection, and attack source tracing.
The log audit system can centrally store and manage the logs of network devices and servers, facilitating monitoring and post-event analysis. In addition, the log audit system can prevent attackers from encrypting or deleting host logs.
For the detailed operation guide, see "Network Protection" in What Is Ransomware and How to Remove Ransomware?.
How Can We Handle Ransomware?
If you are subject to a ransomware attack, perform the following operations.
- Do not rush to pay the requested ransom. Paying the ransom is equivalent to encouraging cybercrime, and there is no guarantee that encrypted files can be recovered.
- In principle, encrypted ransomware cannot be cracked, unless the ransomware design has a defect or the hacker organization discloses the decryption key (such as in the case of Shade).
- If the encrypted datais important or extremely sensitive and no decryption solution is available for ransomware, confirm that the cyber criminal can decrypt the data before deciding whether to pay the ransom.
Common suggestions for handling ransomware include but are not limited to:
- Isolate devices infected with ransomware.
Disconnect network cables or modify network connection settings to isolate all devices infected with ransomware from the network, preventing ransomware from spreading and controlling the impact scope. Then, check the number of affected hosts and record the fault symptoms.
Disable high-risk ports (such as ports 135, 139, 445, and 3389) on other uninfected devices on the LANs, or specify users or computers that can access the ports.
- Clear ransomware.
Restart the operating system, enter the safe mode, and install antivirus software to scan all disks and clear ransomware.
It takes some time for ransomware to search for and encrypt files. Clear ransomware as early as possible to limit its damage and prevent it from repeatedly locking the system or encrypting files.
- Decrypt.
Do not directly reinstall the operating system. If the encrypted data is important, back it up and protect the environment to prevent decryption failures caused by environment damage.
Access the website No More Ransom, use Crypto Sheriff to determine the type of ransomware, and check whether there is an available decryption solution to crack and restore files.
- Perform forensic investigation.
Seek help from professional cyber security teams to collect evidence in order to analyze and trace the attack path of ransomware.
Check security logs in the Event Viewer of the operating system, paying particular attention to login failure events. Check security logs and session logs on network devices, especially major vulnerability attacks such as brute-force cracking and SMB.
Determine the cause of virus infection and fully rectify the security problems in the system to prevent it from being infected again.
- Reinstall the system.
If the ransomware cannot be removed and the encrypted data cannot be restored, back up the encrypted data (which may be restored in the future), format the hard disk drive, delete all data (including infected data), and reinstall the operating system and application programs.
- Author: Jin Desheng
- Updated on: 2022-12-27
- Views: 6097
- Average rating: