What Is Terminal Identification?
Terminal identification is a refined management method for campus network access. It analyzes and extracts terminal characteristics based on the digest fields of some protocol packets to identify terminal information such as terminal types and operating systems. The campus network management system can implement digital presentation and security access control on campus terminals based on the identified characteristics. Terminal identification methods include passive fingerprint collection and proactive scanning.
Why We Need Terminal Identification?
With the popularization and application of ICT technologies such as WLAN and IoT, the enterprise network scale is expanding rapidly, and access terminal types are becoming increasingly diversified and complex. On a campus network, access terminals include smart terminals (such as PCs and mobile phones) and dumb terminals (such as IP phones, printers, and IP cameras). Currently, terminal management on campus networks faces the following challenges:
- The network management system (NMS) can only display the IP and MAC addresses of access terminals, but cannot identify terminal types. As a result, the NMS cannot provide more refined visualized management for network terminals.
- Different service configurations and policies need to be deployed for different types of terminals after they access the network. Consequently, administrators need to manually configure different services and policies for each type of service terminals, complicating service deployment and operations.
To solve these problems, the terminal identification function is introduced. This function offers diversified terminal identification methods. On the NMS, you can view summary information about terminals on the entire campus network, including their terminal types and operating systems. Based on this information, refined management can be performed on the terminals, for example, access authorization by terminal type can be performed. For dumb terminals that typically use MAC address authentication such as IP phones, printers, and IP cameras on the campus network, automatic access based on terminal identification results can be implemented, reducing the configuration workload of administrators.
What Are the Terminal Identification Methods?
Terminal identification methods include passive fingerprint collection and proactive scanning.
Passive Fingerprint Collection
Network devices collect the fingerprint of terminal packets and report it to the NMS, which then matches it against the built-in fingerprint database to identify the terminal types. In this situation, terminals can be identified through a MAC organizationally unique identifier (OUI), HTTP User-Agent, DHCP Option, LLDP, and multicast DNS (mDNS).
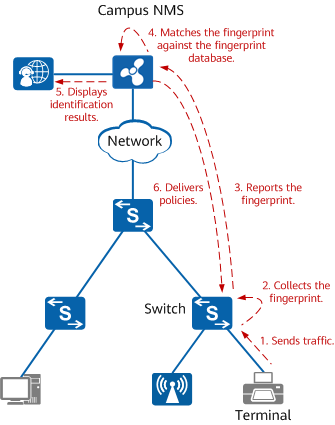
Terminal identification using the passive fingerprint collection method
By MAC OUI
A MAC OUI is the leftmost three bytes in a MAC address that uniquely identifies an organization. MAC OUIs are allocated to organizations by the Institute for Electrical and Electronic Engineers (IEEE).
MAC OUI-based terminal identification is inaccurate. MAC information is related to NIC vendors. Many terminals use a NIC chip provided by another vendor, so the vendor information collected based on the MAC OUI may not be the vendor information of the terminal. Therefore, in terminal identification, MAC OUI-based terminal identification is the last choice or should be used with other methods.
By HTTP User-Agent
Terminals can be identified based on the User-Agent field in HTTP packets because the contents in the User-Agent field vary according to the terminal type. This method is well suited for identifying PCs and mobile terminals, because in most cases, the User-Agent field in HTTP packets sent by these terminals during website access through the browser contains comprehensive terminal information, including the terminal type, operating system, vendor, and browser type.
The following methods are available to obtain the User-Agent information:
- Obtain the information from the Portal server. During Portal authentication, the Portal server extracts the User-Agent information.
- Obtain the information from the device. During Portal authentication, the device reports the information to the NMS.
By DHCP Option
Terminal types can be identified based on options carried in DHCP messages, such as:
–Option 55 (requested parameter list)
–Option 60 (vendor id)
–Option 12 (host name)
Compared with other methods, terminal identification based on DHCP options is more accurate and ideal for identifying terminals that dynamically obtain IP addresses.
By LLDP
The Link Layer Discovery Protocol (LLDP) defines a standard method for Ethernet network devices, such as switches, routers, and WLAN access points (APs), to advertise their presence to neighboring devices and save discovery information about neighboring devices. Detailed device information, including device configurations and identification, can all be advertised using this protocol.
Cisco Discovery Protocol (CDP) and LLDP can help obtain device information, including the device operating system, software version, and description, and then identify the terminal type based on such information.
By mDNS
mDNS enables hosts on a LAN to discover and communicate with each other without the presence of a traditional DNS server.
mDNS operates over port 5353 by default. If the mDNS service is enabled on a host on a LAN, the host will multicast a message that contains its name and IP address to all the other hosts on the LAN. Then other mDNS-enabled hosts will send a response that contains their names and IP addresses.
Currently, many terminals and Linux devices provide the mDNS service. Therefore, these devices be identified using mDNS. The identification method is as follows: Network devices collect the service type characteristics of mDNS packets and send the characteristics to the campus NMS, which then identifies terminal types based on the characteristics.
Proactive Scanning
The campus NMS proactively detects or scans terminals and identifies terminal types based on the feedback information from the terminals. In this situation, terminals can be identified through SNMP query or network mapper (Nmap).
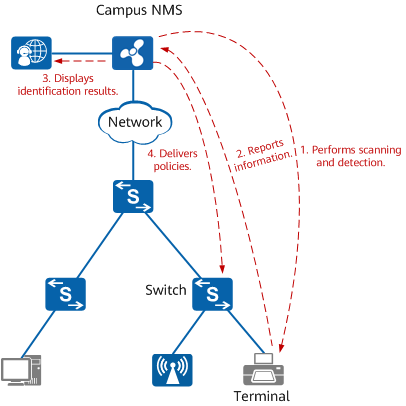
Terminal identification using the proactive scanning method
By SNMP Query
Using the SNMP query method, the campus NMS proactively reads MIB information of terminals and identifies terminals based on the information obtained through SNMP MIB objects. Common MIB objects that can be used to identify terminals include sysDescr and hrDeviceDescr.
sysDescr: specifies basic system information.
hrDeviceDescr: specifies terminal description, including the manufacturer, model, and serial number (optional).
By Nmap
Nmap is an open-source network detection and security auditing tool. It is mainly used in scenarios such as host discovery, port scanning, service version detection, and operating system detection.
The Nmap operating system detection function can be used to detect the operating system types and device types of target hosts. Nmap identifies different operating systems and devices based on the TCP/IP protocol stack fingerprint. The RFC does not mandate TCP/IP implementation. Therefore, different TCP/IP solutions may have their own TCP/IP implementation. Nmap mainly determines the operating system type based on the differences in TCP/IP implementation. The following describes the proactive scanning implementation:
- Nmap uses the fingerprint database that contains the fingerprint features of more than 5600 known systems as a sample database for fingerprint comparison.
- Nmap selects an open port and a closed port, sends a well-designed TCP, UDP, or ICMP data packet to the ports, and generates a system fingerprint based on the returned data packet.
- Nmap compares the generated fingerprint with those in the fingerprint database to find the matching operating system and device type.
Nmap provides terminal identification based on proactive scanning. It does not require networking and devices to support itself, but identifies terminals at a low speed.
What Are the Application Scenarios of Terminal Identification?
Terminal Visualization
During network terminal management and O&M, administrators can view terminal types and operating systems on the entire network through the campus NMS, for example, dumb terminals such as printers, IP cameras, and access control systems, to implement refined management.
Through the campus NMS, administrators can collect terminal type-based statistics and analyze and manage traffic data.
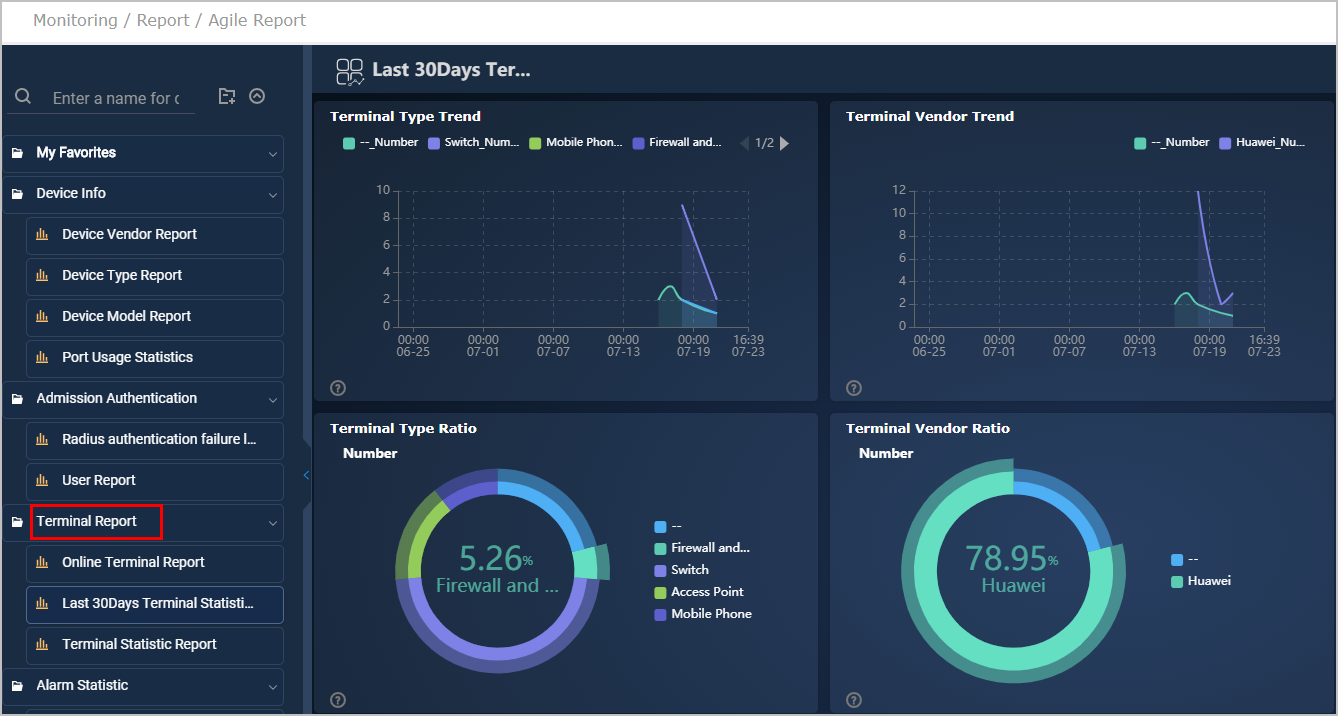
Terminal type-based statistics collection and traffic data analysis and management
Differentiated Terminal Policies
In some scenarios, administrators want to enforce different policies on different types of terminals. For example, different access policies can be configured for mobile phones and PCs. Mobile phones can access only the Internet, while PCs can access both the intranet and Internet.
Administrators can enable terminal identification on the RADIUS server that supports terminal identification and specify authorization policies based on the terminal type. When a terminal accesses the network, the RADIUS server automatically identifies the terminal type and delivers an authorization policy based on the terminal type. Differentiated terminal policies based on the terminal type
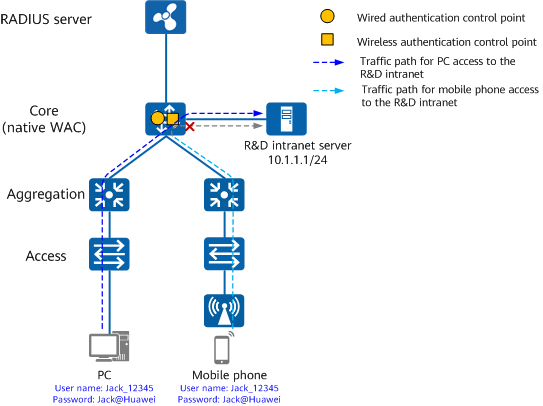
Authentication and authorization based on the terminal type
Terminal Plug-and-Play
On a campus network, access terminals include smart terminals (such as PCs and mobile phones) and dumb terminals (such as IP phones, printers, and IP cameras). Different types of terminals require different network service configurations and policies. Administrators need to manually collect MAC addresses of dumb terminals for access authentication and configure services such as VLANs for each terminal type, complicating service deployment.
Administrators can enable terminal identification on the RADIUS server that supports terminal identification and specify access and authorization policies based on the terminal type. When a terminal goes online, the RADIUS server automatically identifies the terminal type and delivers the corresponding automatic access policy and authorization policy to implement plug-and-play of the terminal.
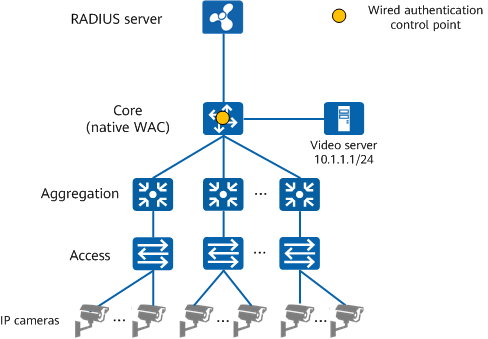
Automatic access based on the terminal type
- Author: Xu Hailin
- Updated on: 2022-05-07
- Views: 5330
- Average rating:






