What Is UDP Flood?
UDP flood is one of the most classic Distributed Denial of Service (DDoS) attacks on the Internet. The attacker sends a large number of UDP packets to the targeted device within a short period of time, causing network congestion and failures. Generally, in the framework of UDP flood, the UDP packets forged by attack tools have the same characteristics in the data segments. Besides, the UDP packets may also be sent by the genuine network equipments. In this situation, although the data segments are different, the fixed destination ports can also be used as the characteristics.
After the characteristics are determined, the UDP attack packets can be filtered based on them. Characteristic filtering, also known as fingerprint filtering, can customize the filtering attributes according to the characteristics of attack packets. It includes static fingerprint filtering and dynamic fingerprint learning.
How Does a UDP Flood Occur?
A UDP flood is a type of denial-of-service (DoS) attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim of overwhelming that device's ability to process and respond. Unlike TCP, UDP is a connectionless protocol, which means that no connection is established between the client and server before packets are transmitted. In addition, UDP does not detect packet loss or display any message about packet loss during client-server communication. Therefore, UDP features low resource consumption and high processing speed. Such advantages make UDP widely used, but also present an opportunity for attackers to initiate UDP flood attacks.
Traditional UDP flood attacks are bandwidth attacks that consume resources of both the attacking and attacked parties. An attacker sends a large number of forged UDP packets to the target device through a botnet. These packets are usually large in size and are transmitted at a high rate, causing link congestion or even network breakdown. This traditional type of attack mode is rarely used due to its low technological requirements.
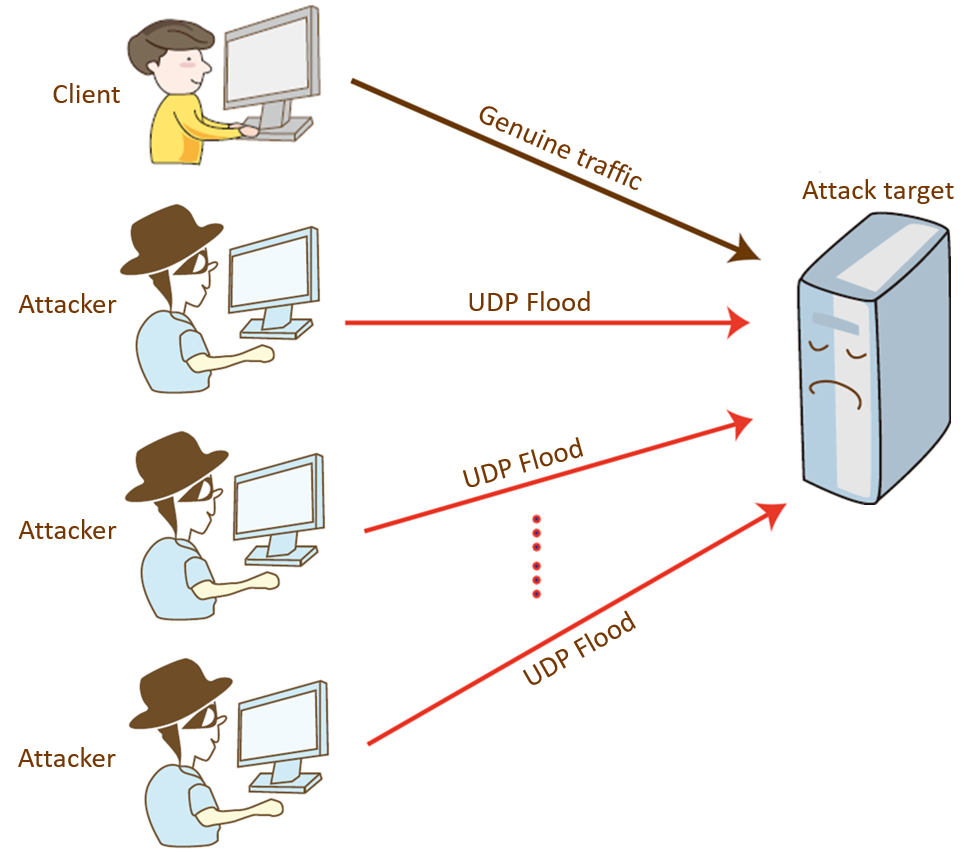
Traditional UDP flood attack
In recent years, more and more attackers use UDP reflection amplification attacks. UDP reflection amplification attacks have two characteristics: attacks are UDP-based and the port number of the attack target is fixed. The underlying principles of different types of UDP reflection amplification attacks are similar. A common type is the Network Time Protocol (NTP) reflection amplification attack, which has two main features: reflection and amplification.
Reflection Attacks
During UDP communication, the client sends a request packet to the server, and the server returns a response packet to the client. No verification is needed throughout the communication. The UDP protocol is connectionless and lacks a source authentication mechanism. These features are exploited by attackers to launch reflection attacks. In a reflection attack, the source IP address of the request packet from a client is changed to the IP address of the attack target, and the response packet returned by the server is sent to the attack target.
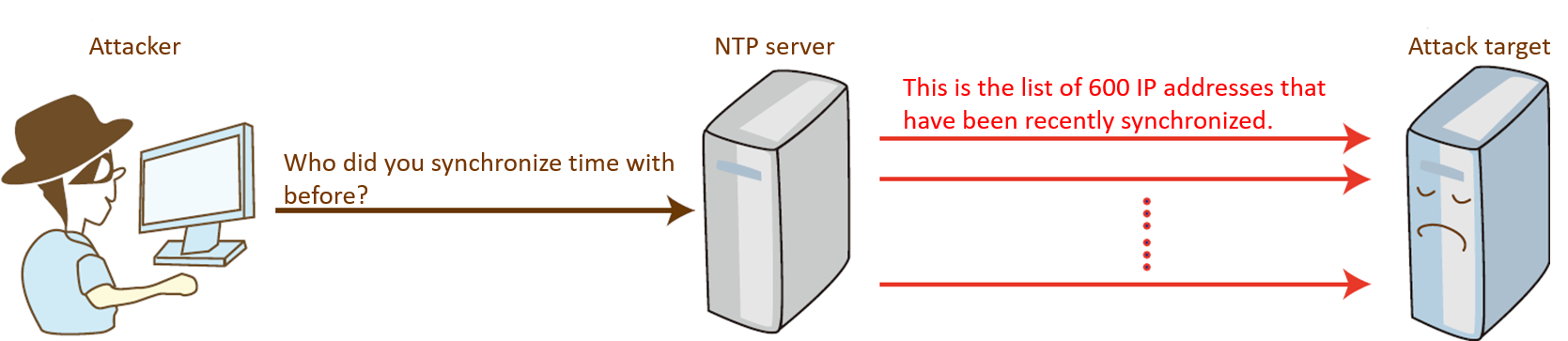
Reflection attack
Amplification Attacks
Attackers usually leverage the Internet infrastructure to launch amplification attacks. There are a large number of open NTP servers on the Internet. Attackers may use zombie hosts to send a large number of monlist requests to NTP servers at the same time. One monlist request packet can trigger 100 response packets. Generally, the size of an NTP request packet (one monlist request) is 90 bytes, and the size of a response packet is 482 bytes. Therefore, the size of response packets triggered by one monlist request is 48200 bytes (100 x 482), 500 times the size of the request packet. An amplification attack is launched by sending monlist requests, causing link congestion or even network breakdown.
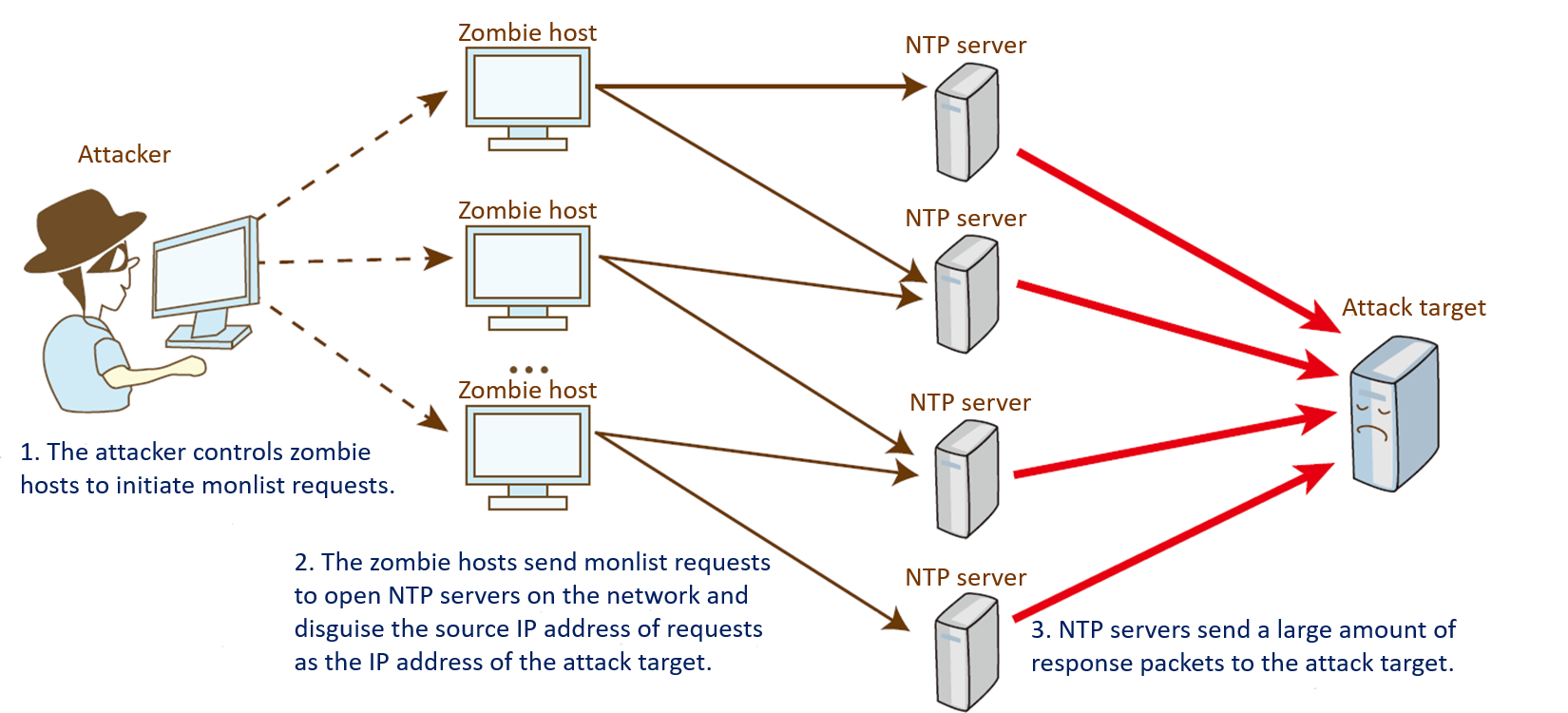
Amplification attack
How Do We Defend Against UDP Flood Attacks?
UDP is a connectionless protocol, which means the source detection technology used in SYN flood attack defense is not suitable for defending against UDP flood attacks. At first, the firewall defends against UDP flood attacks by limiting the rate of UDP packets within a proper bandwidth range based on destination IP addresses, destination security zones, and sessions. Although rate limiting can effectively reduce the link load, some normal packets may be discarded in this way. Therefore, new methods are required.
Attack packets forged by attack tools usually have the same feature fields, for example, the packets all contain a character string or the entire packet content is the same. However, the packets sent by real network devices do not have the same feature field in the data segment, but the destination ports of attack packets are fixed. Therefore, it is easy to find that UDP flood attack packets have certain features. Attack packets can be filtered after their features are determined. Feature-based filtering is also called fingerprint filtering. Fingerprint filtering includes static fingerprint filtering and dynamic fingerprint learning.
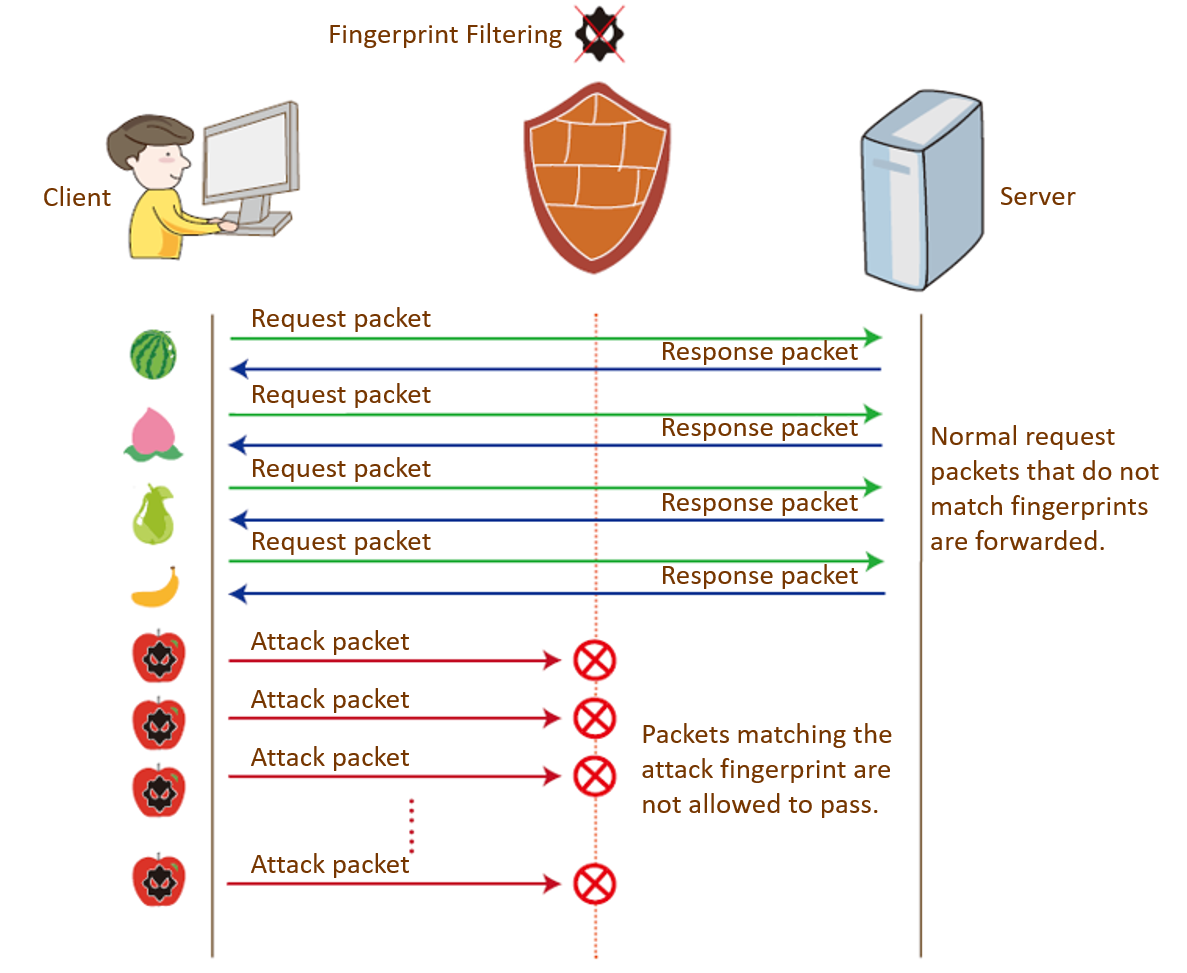
Fingerprint filtering
Static Fingerprint Filtering
The features of attack packets may be hidden in the data segment, source IP address, source port, destination IP address, and destination port of UDP packets. The known attack features can be directly added to the filter parameters of the device. After static fingerprint filtering is configured, the device discards or rate-limits the traffic of the packets that match the attack features.
Dynamic Fingerprint Learning
If attack features are unknown, dynamic fingerprint learning can be used to defend against attacks. For UDP flood attacks launched by certain attack tools, attack packets usually have the same feature fields. With fingerprint learning, statistics are collected on regular UDP flood attack packets and their features are identified. When the number of UDP packets with the same characteristics in a consecutive period exceeds the alarm threshold, fingerprint learning starts. If the same feature occurs frequently, it is learned as a fingerprint. Subsequent packets matched against the fingerprint are identified as attack packets and are discarded or rate-limited.
- Author: Zhao Jie
- Updated on: 2022-08-09
- Views: 5132
- Average rating:






