What Is a Virtual System (VSYS)?
Virtual system (VSYS) is a virtualization technology that divides a physical device into multiple independent logical devices. Each virtual system functions as a real device that has its own resources and runs its own services, which can be independently configured and managed by an administrator. As network management becomes increasingly complex, users have higher requirements on service isolation, system security, and reliability. VSYS technology can be used to physically isolate resources and services, simplify network deployment and management, and enhance system security and reliability.
Virtual System Classification
Huawei firewalls have two types of virtual systems: public system (public) and virtual system (VSYS), as shown in the following figure.
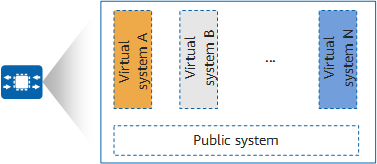
Classification of virtual systems
- The public system is the default virtual system on a device. It manages other virtual systems, including allocating resources to virtual systems and providing services for communication between virtual systems. The public system exists even if the virtual system function is disabled and configuring the device is equivalent to configuring the public system in this scenario. After the virtual system function is enabled on the device, the public system inherits all of the device's configurations.
- A virtual system is a logical device that runs independently on a physical device, and must be created and allocated with resources in the public system.
How Does a Virtual System Work?
With the virtualization technology, the public system administrator can create virtual systems on a Huawei firewall and allocate required resources (including security zones, interfaces, public IP addresses, and session resources) to the virtual systems so that they can work independently as physical firewalls.
If no virtual systems are configured on a firewall, the firewall forwards packets based on policies and various tables (such as the session table, MAC address table, and routing table) of the public system. After virtual systems are configured on the firewall, each virtual system functions as an independent device and has its own policies and tables for packet processing. In this case, after receiving a packet, the firewall must first determine the destination virtual system of the packet.
When creating virtual systems on a firewall:
- If an interface is bound to a virtual system, all packets received at this interface belong to the bound virtual system, and the firewall processes the packets based on the configuration of the virtual system.
- If a VLAN is bound to a virtual system, the firewall forwards packets from this VLAN to the bound virtual system. After the packets enter the virtual system, the virtual system searches its MAC address table for the outbound interface to determine the inter-zone relationship of the inbound and outbound interfaces, and then forwards or discards the packets based on the inter-zone policy.
- If a VXLAN Network Identifier (VNI) is bound to a virtual system, the firewall forwards packets from the corresponding VXLAN to the bound virtual system. Based on the VNI in the VXLAN header and the binding relationship between the VNI and virtual system, the firewall determines the virtual system to which the decapsulated packets are sent. After the packets enter the virtual system, the virtual system searches its routing table for the outbound interface to determine the inter-zone relationship of the inbound and outbound interfaces, and then forwards or discards the packets based on the inter-zone policy.
What Are the Advantages of Virtual Systems?
Virtual systems enable Huawei firewalls to implement virtualization in the following aspects:
- Device resource virtualization: The administrator can allocate exclusive software and hardware resources to each virtual system and limit the resource quota. As a result, when one virtual system is busy, other virtual systems are not affected, ensuring that the physical device's resources are fully utilized.
- Service configuration virtualization: In the virtual system management view, the administrator can configure services for virtual systems in the same way as for physical devices. This simplifies network management and service configuration, which is ideal for large-scale networks.
- Routing entry virtualization: Each virtual system has its own routing table enabling subnets connected to different virtual systems to communicate properly, even if these subnets use the same address range. In addition, the traffic from each virtual system is isolated. Secure access between virtual systems can be configured to meet service requirements.
- Security function virtualization: Each virtual system can have independent security policies and functions configured to protect connected subnets. These security policies and functions apply only to the packets forwarded or generated by the virtual system.
What Is the Relationship Between a Virtual System and a VRF?
Virtual routing and forwarding (VRF) is a widely used technology that isolates routing tables of a physical router to virtualize the physical router into multiple independent logical routers. These logical routers are also known as VPN instances, and the same or overlapped IP addresses can be used in different VPN instances without conflict. As such, forwarding services are isolated and network resources are maximized.
The application scope of VPN instances is narrowed down on Huawei firewalls. Underlying forwarding between virtual systems with isolated routing is implemented through the route distinguishers (RDs) of VPN instances, while the isolation of resources, configurations, and services is implemented through VSYS IDs. The following figure shows the logical relationship between a virtual system and VPN instance.
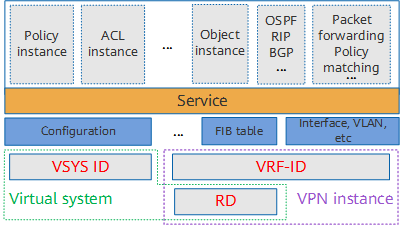
Logical relationship between a virtual system and VPN instance
When a virtual system is created, the firewall automatically generates a VPN instance named after the virtual system. The VPN instance is bound to the virtual system and cannot be deleted separately. The instance ID is the same as the VSYS ID. In addition, the administrator can manually create VPN instances on the firewall. This type of VPN instance is irrelevant to virtual systems and are used for route isolation. Therefore, the names of these VPN instances must be different from the names of existing virtual systems.
- Author: Zhang Na
- Updated on: 2023-07-04
- Views: 16990
- Average rating:







