What Is ICMP?
ICMP is a network layer protocol used to transmit control messages between hosts and routers to report whether hosts are reachable and routes are available. It plays an important role in the TCP/IP protocol suite and is typically used by the IP or higher layer protocols (TCP or UDP). Although these control messages do not transmit user data, they are crucial for collecting network information, diagnosing and rectifying network faults, and transmitting user data.
Why Do We Need ICMP?
During data transmission, IP provides best-effort services. That is, IP tries its best to send data packets to the destination. IP does not verify whether the destination host receives the data packet, and cannot perform flow control and error control. Therefore, various errors are inevitable during data packet transmission. To forward IP packets more effectively and improve the chance of successful packet delivery, ICMP comes into being. ICMP enables hosts or devices to report errors and exceptions to upper-layer protocols when packet transmission experiences errors on the network. Upper-layer protocols then can use their own error control programs to determine whether communication is normal for flow control and error control, ensuring service quality.
How Does ICMP Work?
ICMP is an error reporting mechanism. If an error occurs during packet processing, ICMP reports the error to the source device of the packet. ICMP neither corrects the error nor notifies the intermediate network devices of the error. An ICMP message is encapsulated as a part of an IP datagram and transmitted through the Internet. An IP datagram contains information about only the source and destination, and can record information about all nodes along the path it traverses only if its Record Route option is set. Therefore, a device that detects an error reports the error to only the source but not intermediate devices.
After receiving the error report, the source cannot determine which intermediate device causes the error. However, the source can determine the error type according to the ICMP message and determine how to retransmit the data packet that fails to be transmitted.
The following figure shows the ICMP message format. Each ICMP message contains the complete IP header of the data packet that triggers the ICMP message, and the ICMP message is encapsulated in the IP data packet. The ICMP header contains the following fixed fields, which are the basis for the source to determine the error type:
- Type: message type.
- Code: specific message type.
- Checksum: checksum of an ICMP message.
Different values of the Type and Code fields indicate different types of ICMP messages, which correspond to different errors that may occur during data packet processing. ICMP messages are classified into error and query messages.
ICMP does not generate ICMP error messages in the following situations:
- ICMP error messages do not generate ICMP error messages, but ICMP query messages may generate ICMP error messages. This prevents infinite generation and transmission of ICMP messages.
- IP packets are destined for broadcast or multicast addresses.
- Packets are broadcast at the data link layer.
- The packet is not the first IP fragment.
- The source address of a packet is not a single host address. That is, the source address is an address of all 0s, loopback address, broadcast address, or multicast address.
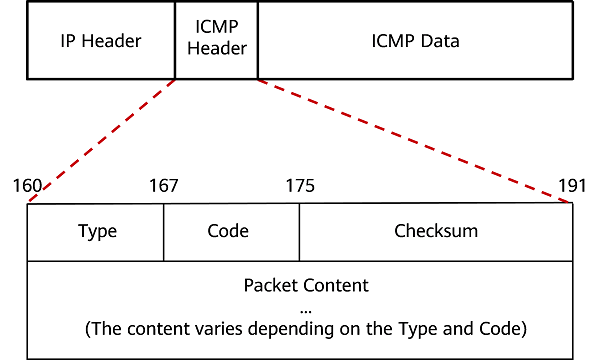
ICMP message format
Type |
Code |
Description |
Query/Error |
|---|---|---|---|
0 – Echo Reply |
0 |
Echo reply |
Query |
3 – Destination Unreachable |
0 |
Destination network unreachable |
Error |
1 |
Destination host unreachable |
Error |
|
2 |
Destination protocol unreachable |
Error |
|
3 |
Destination port unreachable |
Error |
|
4 |
Fragmentation required, and DF flag set |
Error |
|
5 |
Source route failed |
Error |
|
6 |
Destination network unknown |
Error |
|
7 |
Destination host unknown |
Error |
|
8 |
Source host isolated |
Error |
|
9 |
Network administratively prohibited |
Error |
|
10 |
Host administratively prohibited |
Error |
|
11 |
Network unreachable for ToS |
Error |
|
12 |
Host unreachable for ToS |
Error |
|
13 |
Communication administratively prohibited |
Error |
|
14 |
Host precedence violation |
Error |
|
15 |
Precedence cutoff in effect |
Error |
|
5 – Redirect Message |
0 |
Redirect datagram for the network |
Error |
1 |
Redirect datagram for the host |
Error |
|
2 |
Redirect datagram for the ToS and network |
Error |
|
3 |
Redirect datagram for the ToS and host |
Error |
|
8 – Echo Request |
0 |
Echo request |
Query |
9 – Router Advertisement |
0 |
Router advertisement |
Query |
10 – Router Solicitation |
0 |
Router discovery/selection/solicitation |
Query |
11 – Time Exceeded |
0 |
TTL expired in transit |
Error |
1 |
Fragment reassembly time exceeded |
Error |
|
12 – Parameter Problem |
0 |
Pointer indicates the error |
Error |
1 |
Missing a required option |
Error |
|
2 |
Bad length |
Error |
|
13 – Timestamp |
0 |
Timestamp |
Query |
14 – Timestamp Reply |
0 |
Timestamp reply |
Query |
15 – Information Request |
0 |
Information request |
Query |
16 – Information Reply |
0 |
Information reply |
Query |
Typical Applications of ICMP
IP and other programs, among which the ping and tracert (traceroute) applications are the most common, can use ICMP messages to implement multiple applications. In network management and monitoring, network quality analysis (NQA) makes full use of ICMP.
Ping
Ping is the most common debugging method to detect whether IPv4/IPv6 network devices are reachable. It uses ICMP echo messages to test the following:
- Reachability of a remote device
- Round-trip delay in communicating with the remote host
- Whether packets are lost
Tracert
Tracert checks network connectivity by checking the path of packets from the source to the destination. When a network fault occurs, you can use tracert to locate the fault.
Tracert determines the routes from a host to other hosts on the network based on ICMP timeout messages and destination unreachable messages. In addition, it helps determine the delay of each hop on the IP network. The delay indicates the time required for sending a packet from the information source to the destination. The delay can be classified into propagation delay, transmission delay, processing delay, and queuing delay.
NQA
NQA is a technology that measures network performance in real time and collects statistics on network information, such as the delay, jitter, and packet loss rate. It helps learn network service quality in real time and effectively diagnoses and locates network faults.
NQA extends and enhances the ping and tracert functions by using different types of ICMP messages. It can accurately test the network operating status and output statistics. NQA tests include ICMP tests, ICMP jitter tests, and trace tests.
- ICMP test
In an ICMP test, ICMP Echo Request and Echo Response messages are sent to test the destination reachability and calculate the network response time and packet loss rate. The test result clearly reflects the network performance and connectivity. The ICMP test functions similarly to the ping command. The difference is that the ICMP test can provide detailed output information.
- ICMP jitter test
An ICMP jitter test calculates the delay, jitter, and packet loss rate using timestamps carried in ICMP messages. Jitter is calculated by subtracting the interval for sending two consecutive messages from the interval for receiving the two messages.
- Trace test
An NQA trace test monitors the forwarding path from a source to a destination and collects statistics such as delay about each device along the path. The trace test functions similarly to the tracert command. The difference is that the trace test can provide detailed output information. Information about each hop includes the average delay, packet loss rate, and time when the last packet is received.
ICMP Security
ICMP is of great significance to network security. ICMP does not have an authentication mechanism. As a result, ICMP is easy to be used to attack network devices such as switches and routers.
ICMP Attacks
Currently, most ICMP attacks are denial of service (DoS) attacks. The most common ICMP flood attack occurs when an attacker sends a large number of forged ICMP packets to the target device in a short period of time. As a result, the target device is busy with processing these useless packets and cannot provide services for legitimate users. The following figure shows the process.
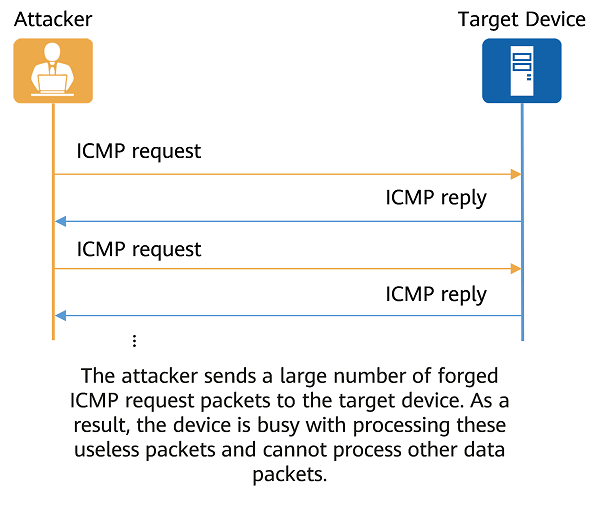
ICMP flood attack
ICMP flood attacks are classified into bandwidth-consuming DoS attacks and port scanning attacks (connection-based DoS attacks).
- Bandwidth-consuming DoS attack
An attacker sends a large number of forged ICMP Echo Request packets. The CPUs of network devices, such as switches and routers, need to respond to these packets, occupying a large amount of bandwidth and CPU resources. This DoS attack, like other DoS attacks, consumes a large number of device resources and makes the devices unable to provide normal services.
ICMP Echo Reply messages have a higher priority. In most cases, internal hosts are allowed to use the ping command. Such attacks target only the network bandwidth and can be initiated by a single attacker. More severe attacks, such as smurf attacks, can enable hosts on the entire subnet to attack the target host, increasing ICMP traffic.
- Port scanning attack (connection-based DoS attack)
A port scanning attack occurs when an attacker sends a large number of port scanning packets to a switch. The switch needs to respond with a large number of ICMP destination unreachable messages, consuming system resources and allowing the attacker to easily access the ports enabled on the switch. Then the attacker can attack these ports, affecting network connections of all IP devices.
In addition, there are DoS attacks targeting hosts, which are also called ping-of-death attacks. These DoS attacks mainly exploit operating system vulnerabilities.
In the early stage, routers limit the maximum size of packets. Many operating systems specify 64 KB as the maximum size of an ICMP message in the TCP/IP protocol stack. After the header of an ICMP message is read, a buffer is generated for the payload based on the information contained in the header. When receiving a malformed packet whose size is claimed to exceed the maximum size of an ICMP message, that is, 64 KB, a device will allocate a payload of more than 64 KB, leading to a memory allocation error. As a result, the TCP/IP protocol stack crashes and the device breaks down.
According to this, an attacker can send an invalid ICMP Echo Request packet to crash or restart the target system. Many systems, including Windows, Unix, Macintosh, and some switches, routers, and printers, are vulnerable to such attacks. If the version of the operating system used by the user is outdated, ensure that required patches are installed.
ICMP Attack Defense
ICMP plays a significant role in network data transmission, network management and monitoring, and network security. Therefore, the ICMP attack defense technology is of great importance to reduce the burden of the device in processing ICMP packets and defend against ICMP attacks. Currently, ICMP packet rate limiting, ICMP packet validity check, discarding ICMP packets that do not need to be processed, and no response to unreachable packets are used to defend against attacks and protect device CPU resources.
- Rate limiting
ICMP packet rate limiting includes port-based rate limiting, VLAN-based rate limiting, and global rate limiting. In addition, chip-based rate limiting is implemented to defend against ICMP flood attacks.
- Validity check and discarding of packets that do not need to be processed
Invalid ICMP packets, such as the packets whose TTL is 0 and ICMP types are 15, 16, or 17 are discarded directly. You can also configure the function of discarding the ICMP packets that are seldom used, including the ICMP packets whose TTL is 1, ICMP packets with options, and ICMP unreachable packets.
- No response to unreachable packets
When a user sends a large number of Destination Port Unreachable or Destination Network Unreachable packets to attack a device, the device discards these packets without responding to them to protect CPU resources.
- Author: Xiang Fulin
- Updated on: 2021-11-24
- Views: 10007
- Average rating:






