What Is IPoE? How Does IPoE Differ from PPPoE?
IPoE is an access authentication technology that enables a user to access a network after dynamically obtaining an IP address through Dynamic Host Configuration Protocol (DHCP). It provides a flexible and efficient access control mode. User terminals can access the network without needing to install dedicated client software. IPoE is applicable to access of various network devices, such as smartphones, digital TVs, and PSPs.
The simple and fast access provided by IPoE reduces the maintenance workload of clients and facilitates the expansion of carrier services on authentication pages, such as advertisement pushes, slogan promotions, and relevant announcements. IPoE access is widely used on networks of chain hotels, campuses, railway stations, and more.
What Problems Does IPoE Solve?
Both IPoE and Point-to-Point Protocol over Ethernet (PPPoE) are access authentication technologies. In traditional PPPoE, data is encapsulated in the Ethernet framework in point-to-point mode. PPPoE provides access, control, and accounting functions to users by establishing PPP sessions and encapsulating PPP packets into PPPoE packets. Because client software needs to be installed on user devices before they access the network through PPPoE, access efficiency is low. In addition, PPPoE technology is based on PPP, a point-to-point protocol. This means that PPPoE has weak support for multicast services with high network overheads, limiting its application scope and the deployment of multicast services. PPPoE does not apply to emerging services, especially those that require multicast technology, such as IPTV services. IPoE is an access authentication technology that can carry multiple services.
IPoE access authentication technology encapsulates users' IP packets into IPoE packets on an Ethernet. IPoE packets carry users' physical and logical information for authentication and authorization. IPoE works with other authentication protocols to implement efficient user access and authentication. Because it does not require client software to be installed on user devices, IPoE implements fast device access. Furthermore, it does not require additional protocol encapsulation. Multicast data flows can be replicated on the Layer 2 switch closest to users, significantly reducing network overheads and improving transmission efficiency. IPoE is suitable for carrying one-to-many video services such as IPTV.
IPoE Characteristics
- Support for multicast services IPoE has flexible multicast capabilities, implements efficient multicast replication, and reduces network pressure. It applies to one-to-many video services.
- Simple protocol process. IPoE has low requirements on terminal and device performance. In addition, it uses the physical and logical information of users in DHCP messages to implement zero-touch deployment of service terminals. This simplifies the service process of terminals and reduces the design requirements of terminals.
- Low network overheads. IPoE supports long-duration online services. A terminal that accesses the network through IPoE needs to renew the lease only when half of the DHCP lease elapses. Except during lease renewal, the DHCP server does not interact with the access device, reducing network overheads.
How Is IPoE Access Authentication Performed?
This section describes the IPoE access authentication process and different authentication modes.
IPoE Access Authentication Process
Before learning about the IPoE access authentication process, it is necessary to understand the roles in IPoE networking. The following figure shows the typical IPoE networking, which consists of four basic elements: user terminal, BRAS, RADIUS server, and DHCP server.
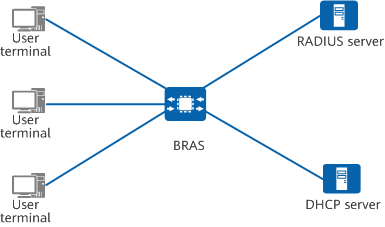
IPoE networking
- User terminal: refers to a terminal that accesses a broadband access device through a local area network (LAN) or wide area network (WAN).
- BRAS: refers to a Layer 3 broadband access device (such as a router) and provides the following functions:
- Prevents users from accessing Internet resources before authentication.
- Interacts with the RADIUS and DHCP servers during authentication to implement identity authentication, IP address application, authorization, and accounting.
- Allows authenticated users to access authorized Internet resources after authentication succeeds.
- RADIUS server: interacts with the BRAS to authenticate users.
- DHCP server: interacts with user terminals and BRASs to manage and allocate IP addresses to user hosts.
The following figure shows the IPoE user access process.
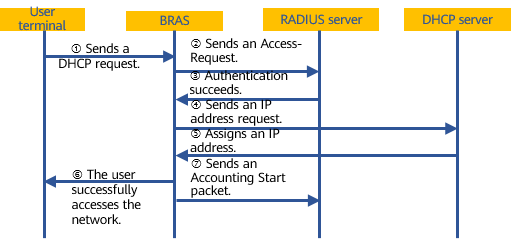
IPoE user access authentication process
- The user terminal sends a DHCP Request message to request network access.
- Upon receipt, the BRAS automatically generates authentication information based on the information in the message and sends the authentication information to the RADIUS server.
- The RADIUS server receives the authentication information and authenticates the user. If the authentication fails, the RADIUS server returns an Access-Reject packet and terminates the session with the user terminal. If the authentication succeeds, the RADIUS server returns an Access-Accept packet to the BRAS.
- After receiving the Access-Accept packet, the BRAS sends a message to the DHCP server requesting an IP address.
- The DHCP server assigns an IP address based on the user's service information.
- After receiving the IP address, the BRAS sends a DHCP ACK message to the user terminal. The user terminal accesses the network successfully.
- The BRAS sends an Accounting Start packet to the RADIUS server to perform accounting for the user's online behavior.
IPoE Authentication Modes
In the preceding user access authentication process, the BRAS automatically generates authentication information according to the request from the user terminal, and sends the information to the RADIUS server for authentication. This authentication mode is referred to as DHCP authentication. In practice, IPoE also uses DHCP to divide a network into two domains: a pre-authentication domain and an authentication domain. Users are authenticated in the pre-authentication domain and access the authentication domain after passing the authentication. Three authentication modes are available:
- Web authentication
Web authentication, also called portal authentication, allows users to enter the username and password on a web page to access the network. Web authentication is often used on networks in public places such as campuses and railway stations and can provide convenient management functions for carriers. It allows carriers to carry out advertisements, community services, and other personalized services on their portals, enabling bandwidth carriers, device vendors, and content and service providers to form an industry ecosystem. Web authentication is classified as proactive web authentication and mandatory web authentication.
- Proactive web authentication: A user accesses the authentication page of a web server and enters the username and password. After obtaining the username and password, the web server sends them to the BRAS, which then exchanges messages with the RADIUS server to complete user authentication.
- Mandatory web authentication: A user attempts to access other websites using HTTP/HTTPS and is forcibly redirected by the BRAS to the web authentication page to enter the username and password. After obtaining the username and password, the web server sends them to the BRAS, which then exchanges messages with the RADIUS server to complete user authentication.
- Web+MAC authentication
Web+MAC authentication, also called simplified MAC authentication, requires a user to enter the username and password on a web page when accessing the network for the first time. After authenticating the user, the RADIUS server automatically records the terminal's MAC address and associates it with the username. When accessing the network again within a certain period of time, the user can directly access the network without needing to enter the username and password again.
- Fast authentication
Fast authentication is a simplified authentication mode in which a user accesses the authentication page of a web server for authentication, without entering the username or password. The BRAS automatically generates the username and password for authentication based on information about the BAS interface that the user accesses.
How Does IPoE Differ from PPPoE?
PPPoE and IPoE are two widely used user access modes. Although both provide authentication for user access, they differ greatly. The following figure shows the comparison between the two.
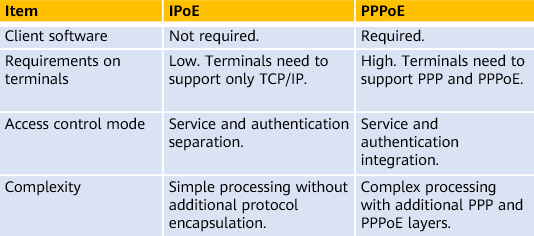
Comparison between IPoE and PPPoE
IPoE and PPPoE meet different network requirements. IPoE can manage the validity period of IP addresses and can be easily configured on a LAN. It is easy to use and does not require client software. However, IPoE needs to work with other protocols to perform authentication. It is widely used in IPTV and voice over IP (VoIP) services. In contrast, PPPoE features high manageability and high security. However, it has limited application scope and hinders the deployment of multicast services. As such, PPPoE is widely used in high speed Internet (HSI) and fiber broadband dial-up access services.
In terms of security, point-to-point encapsulation and transmission in PPPoE provide high security for user access and authentication. In contrast, IPoE requires collaboration among the home gateway, network access device, and broadband network gateway.
- Author: Wang Tianshu
- Updated on: 2023-01-11
- Views: 27236
- Average rating:







