What Is Network Address Translation (NAT)?
NAT translates the IP address in the IP datagram header of a packet into another IP address and translates the port number to make the IP address reusable. As a transition technology that alleviates public IPv4 address exhaustion, NAT is easy to implement and therefore widely used.
What Is NAT Used for?
As the number of network applications increases, IPv4 address exhaustion has become a bottleneck hindering network development. Before IPv6 can be widely used to replace IPv4 that has been running on network devices and bearing existing applications, some IPv4-to-IPv6 transition technologies (such as CIDR and private IP addresses) can be used to alleviate IPv4 address shortage. NAT is such a kind of transition technologies.
When a packet sent by an intranet user for accessing the Internet reaches a NAT-enabled gateway, the gateway translates the IP address in the IP datagram header of the packet to another IP address and the port number to another port number, and then forwards the packet to the Internet. In this process, the gateway can translate the IP addresses of packets from different intranet users to the same public IP address and differentiate intranet users based on port numbers. In this way, the public IP address can be reused.
In early times, NAT refers to basic NAT, which is easy to implement and can translate only IP addresses but not port numbers. Therefore, basic NAT can only allow intranet users to access the Internet, but cannot address the IPv4 address shortage issue. Later, Network Address Port Translation (NAPT) came into being, which can translate both IP addresses and port numbers and allows multiple private IP addresses to be mapped to the same public IP address. As such, NAPT alleviates IP address shortage.
NAT Types
Based on whether source or destination IP addresses of packets are translated, NAT is classified into source NAT, destination NAT, and bidirectional NAT.
Source NAT
Source NAT translates only source IP addresses of packets and applies to the scenario where intranet users access the Internet. When a packet sent from an intranet user for accessing the Internet reaches a NAT device, the NAT device translates the private IPv4 address of the packet into a public IPv4 address. In this way, the intranet user can access the Internet.
Based on whether port number translation is performed during source IP address translation, source NAT is categorized into the types shown in the following figure.
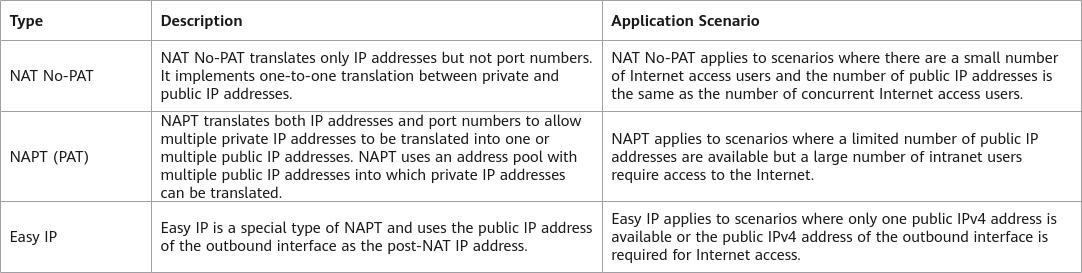
Source NAT types
Destination NAT
Destination NAT translates only the destination IP addresses and destination port numbers of packets, and applies to scenarios where Internet users require to access intranet services. When a packet sent from an Internet user for accessing intranet services reaches a NAT device, the NAT device translates the public IPv4 address of the packet into a private IPv4 address. In this way, the Internet user can access intranet services.
Destination NAT can be classified into the types shown in the following figure based on whether there are fixed mappings between pre-NAT and post-NAT IP addresses.
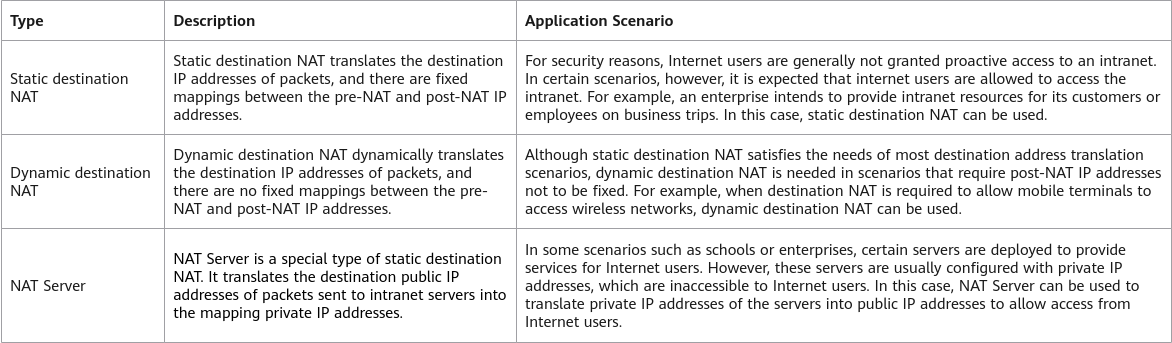
Destination NAT types
Bidirectional NAT
Bidirectional NAT translates both source and destination IP addresses of packets. Bidirectional NAT is not an independent function. Instead, it is a combination of source NAT and destination NAT. Bidirectional NAT applies to the same flow. When receiving a packet, a NAT device translates both source and destination IP addresses of the packet. Bidirectional NAT applies to scenarios where both Internet and intranet users require to access intranet servers.
NAT Types Defined in STUN
In the Session Traversal Utilities for NAT (STUN) protocol, NAT is classified into four types based on the mapping mode from private IP addresses and port numbers to the public IP addresses and numbers, as shown in the following figure.
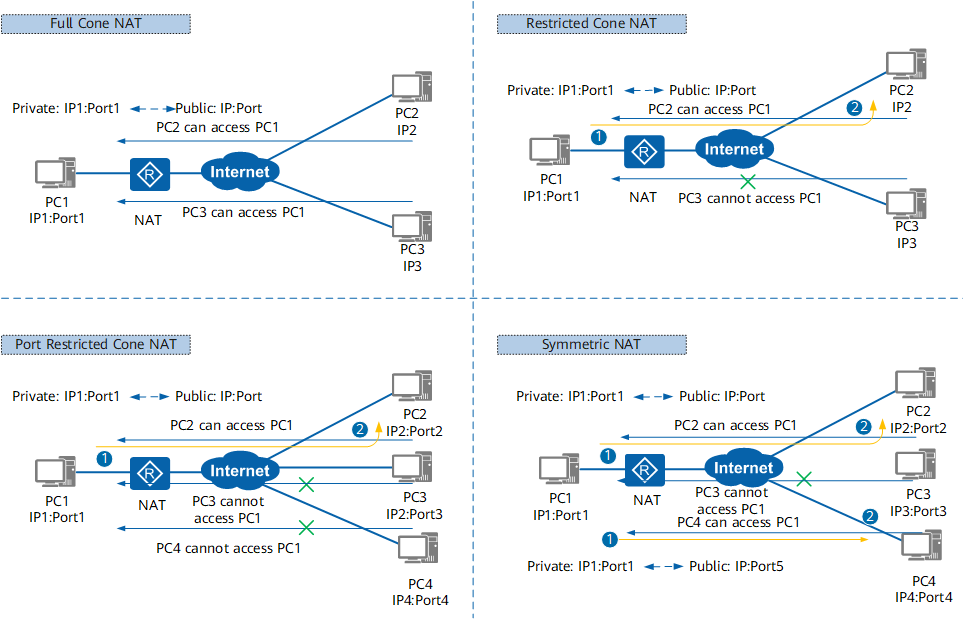
NAT types defined in STUN
- Full-cone NAT
All requests from the same private IP address and port (for example, IP1:Port1) are mapped to the same public IP address and port (for example, IP:Port). In addition, any host on the Internet can communicate with the host on the intranet by sending packets to the mapped public IP address and port.
This is a relatively loose NAT policy. As long as the mapping between the private IP address and port and the public IP address and port is established, any host on the Internet can access the host on the intranet through the NAT device.
- Restricted-cone NAT
All requests from the same private IP address and port (for example, IP1:Port1) are mapped to the same public IP address and port (for example, IP:Port). A host on the Internet can send packets to the host on the intranet only if the host on the intranet has previously sent a packet to the host on the Internet.
- Port-restricted cone NAT
Port-restricted cone NAT is similar to restricted-cone NAT, but the restriction includes port numbers. That is, a host on the Internet (for example, IP2:Port2) can send packets to a host on the intranet only if the host on the intranet has previously sent a packet to the host on the Internet.
- Symmetric NAT
All requests sent from the same private IP address and port to a specific destination IP address and port are mapped to the same IP address and port. If a host sends a packet with the same source IP address and port number to a different destination, a different NAT mapping is used. In addition, only a host on the Internet that receives a packet from a host on the intranet can send a packet back.
Unlike port-restricted cone NAT that maps all requests from the same private IP address and port to the same public IP address and port, regardless of their destinations, symmetric NAT maps requests with the same source IP address and port number but different destinations to different public IP addresses and ports.
Implementation of NAT
According to the preceding NAT classifications, we select NAPT (a type of source NAT) and NAT Server (a type of destination NAT) to describe their implementations. The implementations of other types of NAT are similar although the translated objects are slightly different; therefore, their implementation details are not provided here. Bidirectional NAT is a combination of source NAT and destination NAT, and its implementation will also not be described here.
Implementation of NAPT
NAPT translates both IP addresses and port numbers to allow multiple intranet users to access the Internet using the same public IP address. NAPT differentiates users based on port numbers, and truly implements reuse of IP addresses.
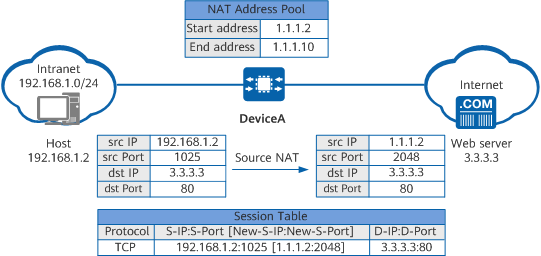
Implementation of NAPT
When a host on the intranet accesses a web server on the Internet, the NAPT process on DeviceA is as follows:
- Upon receiving a packet from the host for accessing the web server, DeviceA determines that the packet matches a NAT policy and requires IP address translation.
- DeviceA replaces the source IP address of the packet with a public IP address selected from the NAT address pool based on the hash result of the source IP address, replaces the source port number of the packet with a new one, creates a session entry accordingly, and forwards the packet to the web server on the Internet.
- The web server returns a response packet destined for the host. When receiving this response packet, DeviceA searches the session table for the entry created in step 2, translates the destination IP address of the packet into the host's private IP address and the destination port number into the host's private port number based on this entry, and then forwards the packet to the host.
Implementation of NAT Server
Before using NAT Server, you need to configure fixed mappings between public and private IP addresses on the NAT device. After the configuration is complete, the NAT device automatically generates server mapping entries for the mappings between the public and private IP addresses. The entries remain unless the NAT Server configuration is deleted.
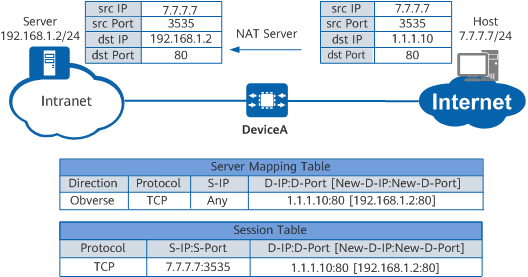
Implementation of NAT Server
The private IPv4 address of a server on the intranet is 192.168.1.2/24, the public IPv4 address is 1.1.1.10, and the port number is 80. The mapping between the public and private IP addresses has been configured on DeviceA. DeviceA performs the following when a host on the Internet accesses the server on the intranet:
- When receiving the first packet destined for 1.1.1.10 from the host, DeviceA searches for the corresponding server mapping entry and translates the destination IP address of the packet into 192.168.1.2.
- DeviceA establishes a session entry and forwards the packet to the server on the intranet.
- When receiving the response packet sent from the server, DeviceA searches the session table for the entry created in step 2, replaces the source IP address of the packet with 1.1.1.10, and forwards the packet to the host.
- Upon receipt of subsequent packets sent from the host to the server, DeviceA performs NAT for the packets based on the session entry, instead of searching for the server mapping entry.
Applications of NAT
As described in the preceding sections, different NAT types apply to different scenarios. To help you better use NAT, the following describes several typical applications of NAT.
Intranet Users Access the Internet Through NAPT
In the intranet planning of some residential communities, schools, or enterprises, private IPv4 addresses are usually assigned to intranet users because public IP addresses are limited. In this case, source NAT can be configured to allow intranet users to access the Internet. NAPT or Easy IP can be selected based on the number of available public IPv4 addresses.
If a large number of public IP addresses are available and there are still available public IP addresses after the IP address of the outbound interface on the NAT device and other applications are configured, NAPT can be used. NAPT uses IPv4 addresses in the address pool as the post-NAT public IPv4 addresses of hosts on the intranet. For example, NAPT is configured on DeviceA to allow intranet users to access the Internet, as shown in the following figure.
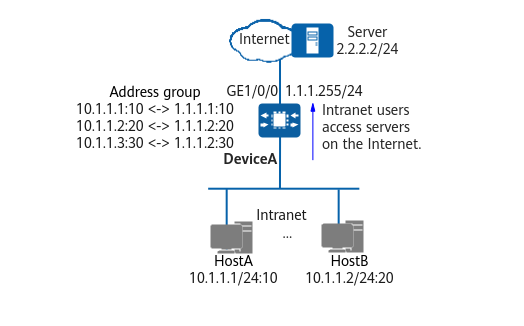
Configuring NAPT for intranet users to access the Internet
Intranet Users Access the Internet Through Easy IP
If there are only a small number of public IPv4 addresses and no public IPv4 address is available after the public IPv4 address of the outbound interface on the NAT device and other applications are configured, Easy IP can be used. Easy IP uses the public IPv4 address of the outbound interface as the post-NAT public IPv4 address of hosts on the intranet. For example, Easy IP is configured on DeviceA to allow intranet users to access the Internet, as shown in the following figure.
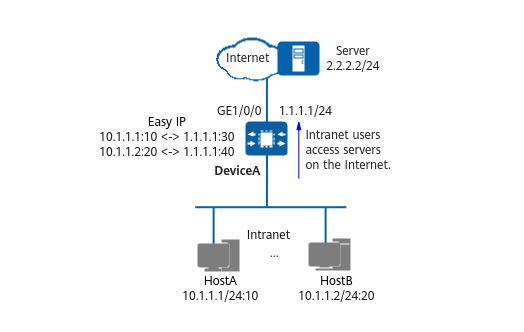
Configuring Easy IP for intranet users to access the Internet
Internet Users Access Servers on the Intranet Through NAT Server
In certain scenarios, some servers on the intranet (for example, web servers and FTP servers) need to provide services for Internet users. In this case, NAT Server can be configured to allow Internet users to access servers on the intranet. For example, in the following figure, NAT Server is configured on DeviceA to fix mappings between public IP addresses and port numbers and private IP addresses and port numbers, so that Internet users can access servers on the intranet.
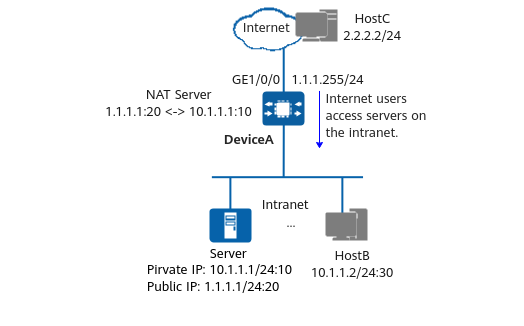
Configuring NAT Server for Internet users to access servers on the intranet
- Author: Liu Qiaoqiao
- Updated on: 2021-09-30
- Views: 37891
- Average rating:







