What Is TACACS?
Terminal Access Controller Access Control System (TACACS) is used for communication with an identity authentication server on the Unix network to determine whether users have the permission to access the network. Vendors extended TACACS. For example, Cisco developed TACACS plus, whereas Huawei developed HWTACACS. Both TACACS+ and HWTACACS are proprietary protocols. They gradually replaced TACACS and are no longer compatible with TACACS.
Background of TACACS
TACACS is an authentication, authorization, and accounting (AAA) protocol developed in the 1980s. It is used to communicate with an identity authentication server on the Unix network to determine whether users have the permission to access the network.
In 1984, a U.S. military research institute designed the earliest TACACS protocol (RFC 927) to automate identity authentication in MILNET, allowing a user who has logged in to a host to connect to another host on the same network without being re-authenticated. Later, Cisco supported TACACS on its network products and extended TACACS (RFC 1492). The extended TACACS protocol is called Extended TACACS (XTACACS). Compared with TACACS, XTACACS separates the authentication, authorization, and accounting processes and allows authentication and authorization to be performed on different servers. These advantages help the administrator perform fine-grained management and control.
With the network development, the administrator has higher requirements on the flexibility in deploying TACACS on servers and the flexibility in controlling the command rights of users. Therefore, vendors further extended TACACS and XTACACS. Typically examples include Huawei developed HWTACACS and Cisco developed TACACS+.
TACACS vs. TACACS+ vs. HWTACACS
- Authentication, authorization, and accounting are independent of each other. Authentication and authorization can be performed on different servers. This makes it more flexible to deploy HWTACACS on servers. For example, two HWTACACS servers A and B can be deployed to perform authentication and authorization, respectively. In addition, during authorization, a successfully authenticated user does not need to be authenticated again because HWTACACS server A notifies HWTACACS server B that the user has been authenticated successfully.
- Each command can be authorized by the server based on the user privilege level. A command can be executed only after being authorized. Therefore, it is easier for the administrator to manage devices.
HWTACACS and TACACS+ are not compatible with TACACS or XTACACS because TACACS and XTACACS use UDP for data transmission and HWTACACS and TACACS+ use TCP for data transmission.
The HWTACACS and TACACS+ authentication processes and implementations are the same. Therefore, the device running HWTACACS can interconnect with the TACACS+ server. HWTACACS attributes and TACACS+ attributes differ in field definitions and descriptions and may not be compatible with each other. For example, if both HWTACACS and TACACS+ support the tunnel-id attribute and the attribute is interpreted as the local user name used to establish a tunnel, the HWTACACS device can communicate with the TACACS+ server. HWTACACS supports the uppeak attribute, but TACACS+ does not. As a result, TACACS+ devices cannot parse this attribute and cannot obtain attribute information.
If you want to check which attributes have the same field definitions and descriptions, see the related documents of Huawei devices for HWTACACS attribute information. For example, if you want to obtain HWTACACS attribute information on Huawei S5700 series switches running V200R020C10, see "HWTACACS Attributes" in User Access and Authentication Configuration Guide. For TACACS+ attribute information, see "TACACS Attribute-Value Pairs" on the Cisco website.
Comparison Between HWTACACS/TACACS+ and RADIUS
RADIUS is the most commonly used AAA protocol, and HWTACACS is similar to RADIUS in many aspects. For example, both use the client/server structure, use the key mechanism to encrypt user information, and are scalable.
HWTACACS and TACACS+ are different from RADIUS in terms of data transmission, encryption mode, authentication and authorization, and event recording. The following compares HWTACACS/TACACS+ and RADIUS.
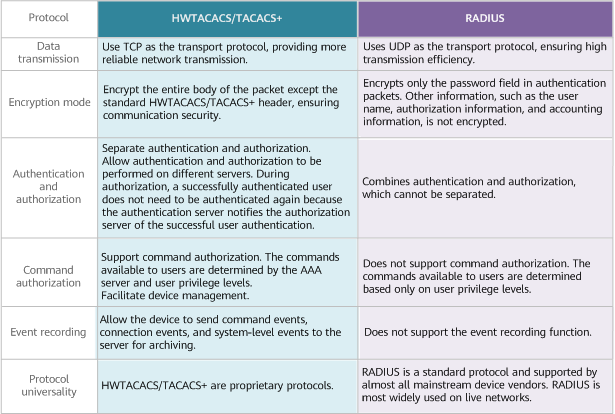
Comparison between HWTACACS/TACACS+ and RADIUS
HWTACACS Authentication, Authorization, and Accounting Process
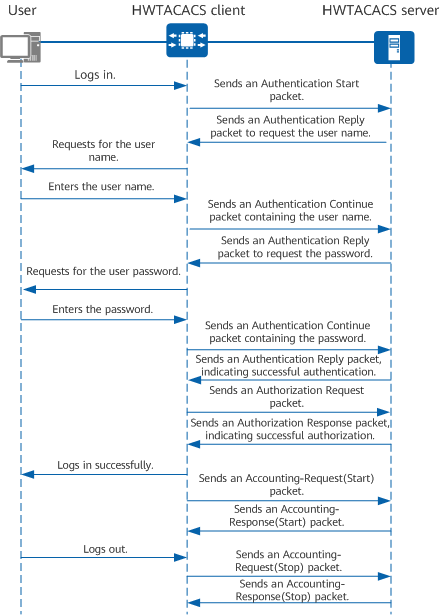
HWTACACS authentication, authorization, and accounting process
- A Telnet user sends a login request to an HWTACACS client.
- The HWTACACS client sends an Authentication Start packet to the HWTACACS server after receiving the request.
- The HWTACACS server sends an Authentication Reply packet to the HWTACACS client to request the user name.
- The HWTACACS client sends a packet to the Telnet user to query the user name after receiving the Authentication Reply packet.
- The Telnet user enters the user name.
- The HWTACACS client sends an Authentication Continue packet containing the user name to the HWTACACS server.
- The HWTACACS server sends an Authentication Reply packet to the HWTACACS client to request the password.
- The HWTACACS client sends a packet to the Telnet user to query the password after receiving the Authentication Reply packet.
- The Telnet user enters the password.
- The HWTACACS client sends an Authentication Continue packet containing the password to the HWTACACS server.
- The HWTACACS server sends an Authentication Reply packet to the HWTACACS client, indicating that the user has been authenticated.
- The HWTACACS client sends an Authorization Request packet to the HWTACACS server.
- The HWTACACS server sends an Authorization Response packet to the HWTACACS client, indicating that the user has been authorized.
- After receiving the Authorization Response packet, the HWTACACS client pushes the device login page to the Telnet user.
- The HWTACACS client sends an Accounting-Request(Start) packet to the HWTACACS server.
- The HWTACACS server sends an Accounting-Response(Start) packet to the HWTACACS client, indicating that the Accounting-Request(Start) packet has been received.
- The Telnet user requests to terminate the connection.
- The HWTACACS client sends an Accounting-Request(Stop) packet to the HWTACACS server.
- The HWTACACS server sends an Accounting-Response(Stop) packet to the HWTACACS client, indicating that the Accounting-Request(Stop) packet has been received.
- Author: Zhu Yue
- Updated on: 2021-10-28
- Views: 8870
- Average rating:







