What Is WLAN?
A WLAN is a wireless computer network that links two or more devices using wireless communication to form a LAN within a limited area such as a home, school, campus, or office building. A WLAN is a network system wherein Wi-Fi is one of the most common technologies in this system. Therefore, WLAN includes Wi-Fi.
Benefits of WLAN
WLAN technology first appeared in the United States. It was primarily used as a wireless extension of the last-mile network and was mainly applied in households. At that time, the American people had a strong demand for wireless Internet access due to the cabling difficulties (most Americans living in villas with courtyards) and the popularity of laptops and tablets. This in turn accelerated the proliferation of WLANs.
Compared with wired networks, WLANs have the following benefits:
- High mobility: It is easy to connect to WLANs that are free from cable and port location constraints. This makes WLANs ideal for scenarios where users are often moving, such as in office buildings, airport halls, resorts, hotels, stadiums, and cafes.
- Flexible deployment: WLANs provide wireless network coverage in places with difficult cabling, such as subways and roadways. Wireless network coverage eliminates or reduces complex cabling, thereby simplifying deployment, reducing costs, and facilitating scalability.
Is WLAN and Wi-Fi the Same Thing?
Wi-Fi is a trademark of the WFA, and is also a wireless network communication technology based on IEEE 802.11. The WFA has announced the use of Wi-Fi to improve the interoperability of products in compliance with IEEE 802.11 standards.
WLAN is short for wireless local area network. Quite simply, WLANs provide network communication using radio waves such as lasers and infrared signals, instead of physical connections. They provide wireless network communication using high-frequency radio waves (such as those on the 2.4 GHz and 5 GHz frequency bands) and comply with IEEE 802.11 standards. WLAN in our daily life refers to that implemented based on IEEE 802.11 standards. During the evolution and development of WLAN, various technical standards have emerged, such as Bluetooth, Wi-Fi, and HyperLAN2. Among them, Wi-Fi is now most commonly used due to its advantages such as simple implementation, reliable communication, high flexibility, and low implementation costs. Gradually, Wi-Fi becomes a synonym of WLAN.
Simply put, WLAN is a network system, while Wi-Fi is a technology in this network system. Therefore, WLAN includes Wi-Fi.
Are WLANs Secure?
WLANs are easy to deploy and expand, flexible, and cost-effective. On WLANs, service data is transmitted through radio signals. As such, service data can easily be intercepted or tampered with by attackers when being transmitted on open wireless channels.
Common WLAN security threats are as follows:
- No Wi-Fi authentication: Attackers can easily connect to WLANs and then attack the entire network.
- Unencrypted wireless data: Attackers can intercept and tamper with service data transmitted on wireless channels by obtaining packets over the air interface.
- Perimeter threats: Rogue APs advertise the same SSIDs as authorized APs. As a result, STAs connect to rogue APs, resulting in data interception by attackers.
To cope with the preceding security threats, differentiated security protection measures are required to protect against network attacks, for example:
- Link authentication and user access authentication are used to prevent unauthorized use of network services. To this end, an enterprise-class user authentication solution is deployed to authenticate and manage user identities in a centralized manner.
- Data encryption is used to improve data security. As such, WPA3 — featuring stronger encryption — is available to protect user data transmitted over the air interface from being cracked. WPA3 has a 256-bit key and is currently the most powerful encryption algorithm.
- Rogue APs can be detected and contained using wireless attack detection technology. For this reason, Wireless Intrusion Detection System (WIDS) and Wireless Intrusion Prevention System (WIPS) can be deployed to detect air interface threats and phishing APs in real time and take containment measures to protect networks against intrusions.
WLAN Roaming
On a WLAN, users require mobile communication. The signal coverage of a single AP, however, is limited. As such, users often move from the coverage area of an AP to that of another AP. To prevent network interruptions while users move between different APs, the concept of WLAN roaming is introduced.
WLAN roaming is a process wherein a station (STA) — when moving to the boundaries between two APs — associates with the new AP and disconnects from the original AP, during which connections are not interrupted. Simply put, WLAN roaming is similar to cell handover for a mobile phone. When a mobile phone moves from the coverage area of a base station to that of another base station, the mobile phone still enjoys uninterrupted and seamless call experiences.
Common WLAN roaming technologies include traditional roaming, fast roaming, smart roaming, and lossless roaming.
Basic Elements of WLAN
- STA: a terminal that complies with 802.11 standards. Examples include a PC that has a wireless network interface card (NIC) or a mobile phone that supports WLAN.
- AP: a device that provides 802.11-compliant wireless access services for STAs. APs function as a bridge between wired and wireless networks.
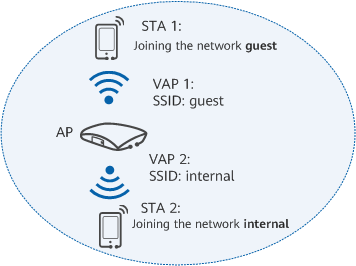
STA and AP - Virtual access point (VAP): a WLAN service entity on an AP. You can create different VAPs on an AP to provide wireless access services for different user groups.
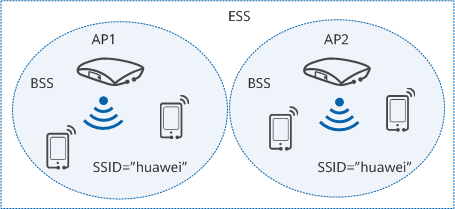
Diagram of VAPs on an AP - Basic service set (BSS): an area covered by an AP. STAs in the same BSS can communicate with each other.
- Extended service set (ESS): a group of BSSs that share the same SSID.
Relationship between BSS and ESS - Distribution system: connects two or more independent wired or wireless LANs through wireless links between APs to construct a network on which users can exchange data. Typical distribution systems are mainly built on the wireless distribution system (WDS) or mesh protocol.
WLAN Networking Modes
In enterprise scenarios, typical WLAN networking modes include the following:
- Independent Fat AP deployment
A Fat AP can provide Wi-Fi coverage independently without the need of an additional management and control device. However, because the Fat AP controls STA access independently, STAs cannot roam between Fat APs. The STAs can use the Wi-Fi network only within the coverage area of the connected Fat AP.
Therefore, Fat APs are typically deployed to provide small-scale Wi-Fi coverage in home or SOHO environments. In enterprise scenarios, the "AC + Fit AP" and "cloud management platform + cloud AP" networking modes are typically used.
- Centralized AC + Fit AP deployment
The AC + Fit AP architecture is widely used for Wi-Fi network deployment in large and midsize campuses, such as shopping malls, supermarkets, hotels, and enterprise offices. The AC manages and controls all Fit APs connected to it through CAPWAP tunnels. The AC delivers configurations to Fit APs in batches, eliminating the need to configure APs one by one. This greatly reduces WLAN management and maintenance costs. Additionally, STAs can roam between Fit APs because their access authentication is centrally managed by the AC.
In small-scale Wi-Fi coverage scenarios, only a few APs are required. If an additional AC is deployed, the WLAN cost is increased. In such a scenario, Fat APs are recommended if STA roaming is not required. If STA roaming is required, cloud APs are recommended.
- Cloud-based deployment
Cloud APs provide similar functions as Fat APs, and can be deployed to build small WLANs in home or SOHO environments. Similar to the AC + Fit AP architecture, the cloud management platform + cloud AP architecture allows cloud APs to be centrally managed and controlled by the cloud management platform. Therefore, this architecture is also applicable to large and midsize networks.
Cloud APs are plug-and-play and are easy to deploy. They can be flexibly expanded out of space restrictions. Therefore, cloud APs are widely used in multi-branch scenarios.
How Does WLAN Work?
On a WLAN, the transmit end first applies source coding to convert information into digital signals that allow for circuit calculation and processing, and then into radio waves by means of channel coding and modulation. After receiving the radio waves, the receive end demodulates and decodes the radio waves and converts them into information. The information may be an image, a text, a sound, or the like. The transmit and receive ends are connected over interfaces and channels.
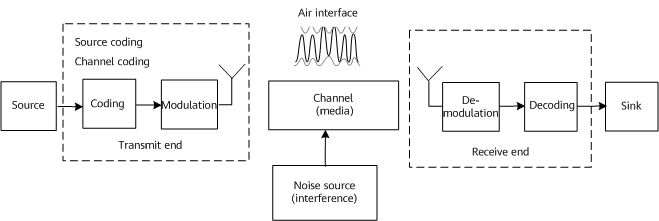
Working mechanism of WLAN
- Source coding: a process of converting raw information into digital signals by using a coding scheme. Source coding can reduce redundant information in the raw information, by compressing the information to the maximum extent without distortion. Different types of information require different coding schemes. For example, H.264 is intended for videos.
- Channel coding: a technology for detecting and correcting information errors to improve channel transmission reliability. With wireless transmission that is prone to noise interference, information arriving at the receive end may be erroneous. Channel coding is introduced to restore information to the maximum extent at the receive end, thereby reducing the bit error rate. WLAN uses two channel coding schemes: Binary Convolutional Encoding (BCC) and Low Density Parity Check (LDPC).
- Modulation: Digital signals in circuits are instantaneous changes between high and low levels. Only after being superimposed on high-frequency signals generated by high-frequency oscillation circuits, can the digital signals be converted into radio waves over antennas and then transmitted. The superimposition action is the modulation process. Having no information itself, a high-frequency signal only carries information and is therefore called a carrier. The modulation process actually encompasses symbol mapping and carrier modulation. On a WLAN, a common symbol mapping technology is Quadrature Amplitude Modulation (QAM), and a typical carrier modulation technology is Orthogonal Frequency Division Multiplexing (OFDM).
- Air interface: an interface used for wireless communication. It is easy to understand wired communication, as the interfaces on devices are visible and connect to visible cables. However, the interfaces on a WLAN are invisible and connect to invisible spaces. For this reason, air interfaces are introduced.
- Channel: refers to the pipe for transmitting information. For WLANs, 802.11 standards also define wireless channel frequency bands and specific frequency ranges available.
- Author: Zhou Xia
- Updated on: 2022-04-02
- Views: 27324
- Average rating: