What Is Antivirus?
Antivirus is a security mechanism that identifies and handles virus-infected files through the detection of virus signatures. It aims to prevent data corruption, permission modification, and system crashes caused by virus-infected files, thereby ensuring network security.
Leveraging a large and continuously updated virus signature database, the antivirus function protects intranet users and servers from being compromised by virus-infected files. An antivirus-capable device is deployed at the network egress to detect and eliminate viruses, thereby protecting the network.
Why Do We Need Antivirus?
Viruses are a type of malicious code that can spread through mail and file transfer protocols, and which are often attached to application programs and files. Viruses perform various types of harmful activities on infected hosts, posing serious threats to both hosts and the network. Some viruses may exhaust resources and maliciously occupy network bandwidth, while others control host permissions and steal user data. Certain viruses can even corrupt host hardware.
With the continuous development of network technologies, users are now transferring, downloading, and sharing files more frequently than ever before, and face unprecedented virus threats as a result.
After a network security device (such as a firewall or dedicated antivirus gateway) is deployed at the network egress and the antivirus function is configured, the device allows normal files to enter the intranet. However, once a virus-infected file is detected, the device blocks it or alerts users to its presence.
The antivirus function configured on the network security device and the antivirus software installed on user hosts are mutually complementary. As they are deployed at different locations and use different antivirus signature databases, they can be used together to secure user hosts and the network.
Antivirus function
How Does Antivirus Work?
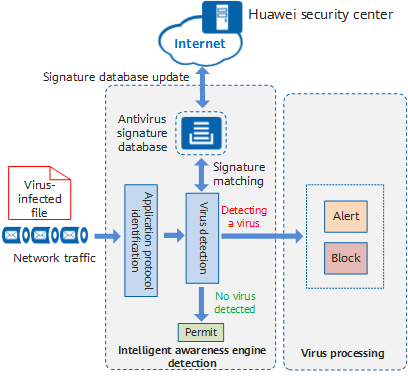
Huawei network security devices use the dedicated and efficient intelligent awareness engine and continuously updated virus signature databases to detect and handle virus-infected files. The workflow of the antivirus function involves three parts.
Antivirus processing
- Application protocol identification: As viruses spread through protocols, such as email and file transfer protocols, the identification of such protocols and the transfer directions are essential for virus detection. Common protocols include:
- File Transfer Protocol (FTP): the most common file transfer protocol, involving the FTP client and server. The FTP client can download files from and upload them to the FTP server. As such, files (viruses) are transferred in two directions: downloading and uploading.
- Hypertext Transfer Protocol (HTTP): a common web browsing protocol that can also be used to transfer files. HTTP also transfers files in two directions. The client (that is, a browser) downloads files from and uploads them to the server.
- Simple Mail Transfer Protocol (SMTP): the most common mail transfer protocol, which is used to transmit emails from a client to an email server, as well as from one email server to another. As sending emails through SMTP is a push process, there is only one file transfer direction, that is, uploading (sending emails).
- Post Office Protocol 3 (POP3): used by clients to read emails from an email server. As reading emails through POP3 is a pull process, there is only one file transfer direction — downloading (receiving emails).
- Interactive Mail Access Protocol (IMAP): used by clients to send emails to and receive them from email servers. It also enables clients to directly operate emails on the email servers. IMAP supports both downloading (receiving email) and uploading (sending email) file transfer directions.
- Network File System (NFS): a file sharing protocol used in Linux systems. The file transfer directions include uploading and downloading.
- Server Message Block (SMB): a file sharing protocol used in Windows systems. The file transfer directions include uploading and downloading.
- Virus detection: The device extracts signatures from files to be transferred and matches them against those in the virus signature database. If the signatures match, the file is considered to be a virus-infected file and sent to the antivirus module. If the signatures do not match, the file transfer is permitted.
- Response and processing: After detecting that the file to be transferred is a virus-infected file, the device performs either of the following operations:
- Alert: allows the virus-infected file to pass through and records virus logs for the network administrator to analyze the viruses and take further measures.
- Block: prevents the virus-infected file from passing through and records virus logs for the network administrator to analyze and take further measures.
- Tunnel teardown. In most cases, session aging (session disconnection) between two communication parties indicates that data exchange between the two communication parties is complete. To save system resources, the tunnel between the two communication parties is automatically torn down when the tunnel idle timeout period is reached.
What Is a Virus Signature Database?
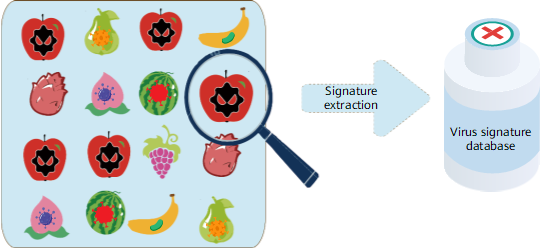
As mentioned above, the key to virus detection is virus signature identification and matching. Huawei security center (isecurity.huawei.com) analyzes massive volumes of virus samples, extracts virus signatures, and stores them in the virus signature database. New viruses are constantly emerging on the Internet, and in order to keep pace, the virus signature database is continuously updated. Ensuring that the virus signature databases on network security devices are always updated to the latest version can effectively improve the virus detection capabilities and efficiency of those devices.
Antivirus signature database
What Are Effective Antivirus Methods?
The key to effective antivirus is the construction of a complete antivirus system and improvement of the security awareness of network users.
- Antivirus software must be installed on all network terminals on an intranet, including computers, servers, and mobile phones connected to the network.
- Network security devices (such as firewalls or dedicated antivirus gateways) must be deployed at key network locations, such as Internet egresses and server area egresses, to prevent viruses from spreading at the network layer. For intranets with high security requirements, a network security device can be deployed at each LAN egress to prevent viruses from spreading between LANs.
- An NMS can centrally manage the antivirus software of terminals and network security devices on the network, and update their virus signature databases in a timely manner.
- All users should raise their security awareness, avoid clicking attachments or links in extranet emails, and steer clear of illegal websites that may contain viruses.
- Author: Xi Youyuan
- Updated on: 2023-07-04
- Views: 9643
- Average rating:







