What Is Command and Control?
With the development of malware and malicious attacks, most attackers do not use a single host to attack, but control a certain number of victim hosts to launch collective attacks, increasing attack effects and reducing the risk of being detected and blocked. C&C is one of key technologies for attackers to control victim hosts. More specifically, C&C servers control the victim hosts.
A C&C server can collect information about a victim host, such as an operating system, application software, and an open port, and instruct the victim host to perform some malicious behaviors by sending instructions. Attackers can also use the victim host as a springboard to infect more hosts on the network. Finally, the C&C server controls all of these hosts.
What Impact Will C&C Bring?
Currently, as most network border defense measures are effective, directly connecting to a target host from the extranet is difficult for an attacker. However, there are often no strict restrictions on connections initiated from the intranet, which gives attackers a chance. C&C communication can exploit this to infect a host. If a malicious program has been implanted to a victim host, the program usually establishes an outbound connection to the attacker's computer. After the attacker successfully accesses the intranet host, the attacker can perform the following operations:
- Lateral movement attack
The first compromised host is often not a very valuable target. (This is easy to understand. Important targets are carefully protected against direct attacks.) The attacker can use the victim host as a springboard to obtain information about another host on the network and move deeper into a network. Attackers repeat this process to access and control high-value targets.
- Confidential data theft
As C&C communication is bidirectional, an attacker can both send instructions to a victim and instruct the host to send confidential data to the server. The attacker usually steals confidential data and extorts a victim. If the victim does not pay for something, the attacker will spread or sell the confidential data.
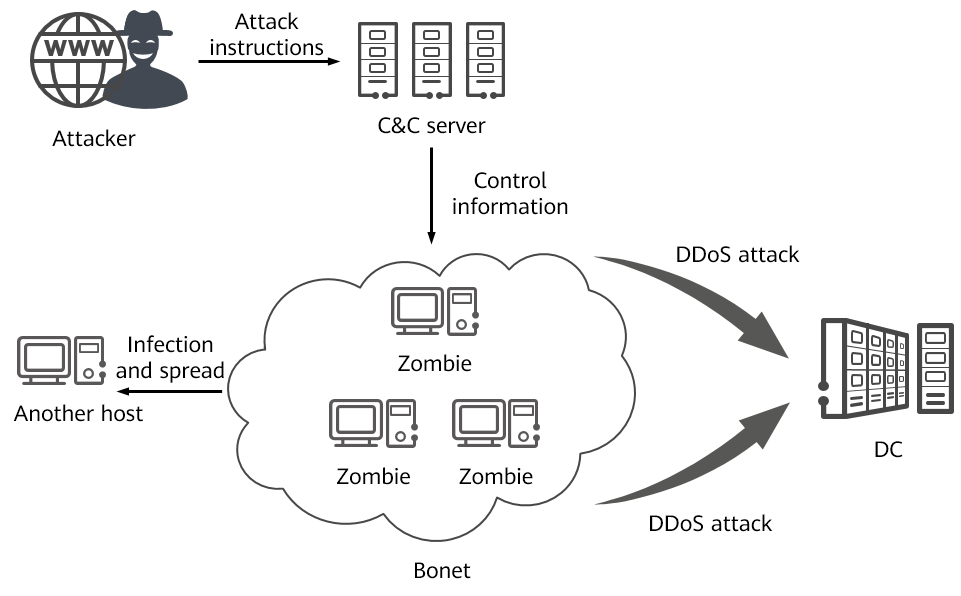
- DDoS attack
DDoS attacks are launched by botnets. A botnet is a group of hosts that have been infected by malicious programs and controlled by attackers. The infected hosts are generally called zombies. An attacker sends instructions to a zombie through a C&C server to launch a DDoS attack on a target.
- APT attack
An advanced persistent threat (APT) attack usually takes a long time and is sometimes suspended by an attacker in a certain phase on purpose. For example, after an attacker obtains control over some hosts through a C&C server, the attacker does not immediately launch an attack, and instead, may stay dormant in search of a better attack opportunity, or may seek interested buyers to sell the C&C server and victim hosts as a package.
Harmfulness of C&C
C&C Communication Modes
C&C communication involves two important roles: C&C server and client. The C&C server is a host controlled by hackers, and the C&C client is a victim host that is implanted with malicious programs. The C&C server can collect information about a victim host, such as an operating system, application software, and an open port, and instruct the victim host to perform some malicious behaviors by sending instructions. Attackers can also use C&C clients as springboards to infect more hosts on the network, increasing the number of C&C clients.

Key roles in C&C communication
Generally, malicious programs can be disguised as normal software to infect victim hosts through phishing emails and malicious websites. As the infection process is random, attackers cannot predict which hosts are infected. As such, malicious programs on the victim hosts need to proactively communicate with the C&C server. The malicious program on each victim host maintains communication with the C&C server and re-initiates a connection in case of a disconnection.
Common C&C communication methods are as follows:
- Accessing the C&C server through an IP address
This is the most common type of communication with the C&C server. An attacker hardcodes the IP address of the C&C server in a malicious program, and then the C&C client sends a communication request to the IP address. This communication mode is simple, and the server can be easily detected. To defend against such an attack, a network administrator can block the IP address. By doing this, the attacker can no longer control the C&C client.
- Accessing the C&C server through a domain name
An attacker hardcodes the domain name (instead of the IP address) of the C&C server in a malicious program, which makes the server covert. However, the server is also easy to detect. To defend against such an attack, a network administrator can block the domain name. By doing this, the attacker can no longer control the C&C client.
- Fast-flux
Fast-flux technology constantly changes the mapping between domain names and IP addresses. As such, it is difficult to discover all mappings between the IP addresses and domain names and block them in one go. To combat this technology, the mappings can be discovered. For example, a network administrator can mine all mappings of IP addresses and domain names using a short time to live (TTL) setting.
- Using a website or forum as a C&C server
Attackers send C&C control instructions in unpopular areas of some forums or on popular websites, and then allow malicious programs to obtain the instructions from the website or forum through a crawler. As such, discovery becomes difficult, but handling is relatively easy by reporting to the website administrator who will block the involved account.
- Generating random domain names using DGA
The Domain Generation Algorithm (DGA) can be used to generate a large number of random domain names that are to be accessed by C&C clients. This is a mainstream C&C communication method. As domain names are randomly generated, the attack is difficult to detect and defend against. Generally, machine learning is used to detect DGA domain names and automatically add such domain names to a blacklist or block related traffic.
How to Detect and Defend Against C&C
The key of C&C attack defense lies in whether an attacker can successfully hide the C&C service. After discovering a hidden C&C service, a network administrator can take technical measures to terminate C&C communication before processing victim hosts.
The following methods can be used to detect C&C traffic and attacks:
- Detecting traffic to external networks
Most network security defense measures focus on the presence of threats in incoming traffic but less on outgoing traffic, which can be exploited by C&C attacks. After a C&C connection is initiated by a victim host, many subsequent interaction processes and malicious program downloading are not blocked. In this case, rules can be configured on a gateway to detect intranet-to-extranet traffic to prevent the traffic from being unsupervised.
- Detecting beacons
If a malicious program infects a host, a beacon is sent to notify the attacker of successful infection. Thereafter, the malicious program can stay idle and periodically checks in to the C&C server for further instructions. Beacons can also be sent as a type of heartbeat to inform the attacker that a host is active.
- Logs
A network administrator can collect as many logs as possible and analyze them. In the past, security analysts relied on massive logs to look for abnormal information, such as HTTPS or DNS requests that might contain malicious program file data. Currently, many security products and systems support intelligent analysis of massive logs, which greatly improves analysis and processing efficiency.
- Correlation analysis
Sometimes attackers hide malicious behaviors so that it is difficult for network administrators to detect threats from individual events. In this case, massive data can be collected and analyzed on the entire network to discover the correlation of the data and hidden malicious behaviors.
C&C technology is mainly used after malicious programs infect hosts. We believe guiding users on preventive security behaviors in advance will prevent hosts from being infected. The following are some preventive suggestions:
- Try to download software from official websites instead of small websites, web disks, and forums.
- For security software installed on a host, periodically scan the system to prevent viruses and Trojan horses.
- Upgrade and update software and systems in a timely manner to prevent attacks exploiting known vulnerabilities.
- Strengthen network security construction, make attacks and intrusions more difficult, and intercept most attacks and threats.
How Does Huawei Help You Defend Against C&C?
If a C&C client stays in the latent phase, it is difficult to detect it. To the contrary, it will proactively communicate with the C&C server, which provides a breakthrough for detecting potential threats. C&C communication traces can be discovered using original data such as beacons, logs, and traffic, or leveraging correlation analysis.
HiSec Insight Advanced Threat Analysis System
The HiSec Insight Advanced Threat Analysis System uses the big data platform and intelligent detection algorithm to perform multi-dimensional correlation analysis on mass data, detect various security threat events in real time, and restore the entire APT kill chain. In addition, it displays the security situation of an entire network to provide users with an overview of the network security status. The HiSec Insight supports detection functions for multiple threats, including C&C anomaly detection, encrypted traffic detection, event correlation analysis, and covert channel detection.
USG6000E Firewall
In addition to providing NGFW capabilities, the USG6000E can interwork with other security devices to enhance border detection capabilities and effectively mitigate advanced threats. The USG6000E provides an intelligent detection engine that uses machine learning and in-depth learning to detect DGA domain name requests, malicious C&C traffic, and malicious encrypted traffic.
- Author: Yan Guanghui
- Updated on: 2021-09-30
- Views: 4764
- Average rating:







