What Is an Advanced Persistent Threat (APT)?
An advanced persistent threat (APT) is a complex, persistent cyberattack that has three characteristics: advanced, persistent, and threat. The word "advanced" indicates such APT attacks require higher customization and complexity than traditional attacks, and a lot of time and resources are required for research and identification of vulnerabilities in the system. The word "persistent" means that, in order to achieve specific purposes, an attacker continuously monitors a target and retains long-term access to it. The word "threat" emphasizes that attacks are elaborately planned and target high-value organizations. Once successful, such attacks will cause huge economic losses, political impact, or even devastating damage to the target.
Five Stages of an Advanced Persistent Threat
An APT attacker is usually an organization that adopts a multi-phase process, which starts by targeting a victim and aims to eventually achieve success. This process is called a kill chain in the security domain. Although different vendor may define a slightly different kill chain process, the overall process is essentially the same.
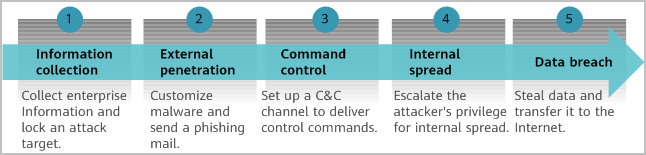
APT kill chain
Infomation Collection
Once an attacker has selected a target, the attacker then gathers as much intelligence information about the target as possible. The information may include the target organization structure, office location, products and services, employee address book, management email addresses, executive meeting agenda, portal directory structure, internal network architecture, deployed network security devices, open ports, office OSs and email systems used by enterprise employees, and the OS and version of the corporate web server.
External Penetration
- After collecting this information, the attacker researches how to infiltrate the organization, determining whether to start with phishing emails, web servers, or USB flash drives. In the case of a phishing email, the attacker researches which client software zero day vulnerability to exploit. In the case of a web server, the attacker identifies what websites target users visit most frequently.
- Once the means of penetration is determined, the next step is to create specific malware. Typically, the attackers' organization has a dedicated group of people working on zero day exploits and closely monitoring the latest notifications on key vulnerability reporting platforms. Leveraging publicly or semi-publicly disclosed vulnerability and possible POC code, the attackers further develop their own malware, such as malicious code (referred to as shellcode) embedded into PDF or Microsoft Office files. Such malware involves anti-detection measures, such as code obfuscation, shelling, and encryption. In addition, to bypass detection, the attackers usually use the latest antivirus software to scan the malware before delivering it to a target network.
- Once the malware is written, the next step is to deliver it to the target network. Common methods include email attachments, websites (with embedded Trojan horses), and USB flash drives.
- For phishing email attacks, an attacker must carefully construct an email, containing the email content, email title, and attachment name and type. This is done in an attempt to entice the recipient to click the email attachment or URL in the email body. For example, phishing emails and decoy files related to the COVID-19 pandemic became a worldwide trend for APTs in 2020.
- For websites (with embedded Trojan horses), an attacker selects a legitimate website based on the interests of the attack target. The website must contain zero day vulnerabilities that can be exploited, allowing the attacker to infiltrate and attack the website. After gaining access to the website, the attacker implants a script that can be automatically downloaded in the background. In this way, victims who visit the website unknowingly download the malware to their local computers, and the malware exploits browser vulnerabilities for installation and execution.
- For USB flash drive attacks, an attacker loads malware onto a USB flash drive in the hope that attack targets will insert the drive into their local computers. This method is typically used if attack targets do not have network connectivity but it requires close contact with the targets.
Command and Control
When a target user runs a vulnerable client program or uses a browser to open a file containing malicious code, the malicious code triggers the malware download and installation by exploiting the vulnerability. The malware is usually a small remote control tool, which is called a remote administration tool or remote access Trojan (RAT) in the industry. It is used to establish a command and control (C&C) channel to the control server. Malware typically escalates privileges or adds an administrator account, enables itself to start during device startup, and even quietly disables or modifies host firewall settings in the background to remain hidden.
Internal Spread
Office hosts in an organization typically run the same operating system in similar application environments, meaning that they generally have the same vulnerabilities. After an intranet host is exploited, malware spreads horizontally to other hosts on the subnet or vertically to internal servers of an enterprise. The RAT provides key logging and screen recording functions, making it easy to obtain the user domain password, email password, and various server passwords from the victim.
Data Breach
Attackers often use anonymous networks and encrypted communications, and cover their tracks as much as possible, in order to protect themselves at each step of an attack. They also use various technical measures to prevent from being detected by network security devices when sending confidential information. For example, attackers may fragment, encrypt, or obfuscate confidential information to avoid a data loss prevention (DLP) device from discovering data breaches through keyword scanning. They may also limit the rate at which packets are sent to prevent exceeding the detection thresholds configured on various security devices.
APT Examples
Google Aurora and Stuxnet attacks are well-known APT attacks initiated in 2010 and are typical cases of APT attacks. In recent years, supply chains, telecommuting, and mobile devices have become the attack entry points, for example, the SolarWinds supply chain incident at the end of 2020.
Google Aurora Attack
The Google Aurora attack is a targeted cyberattack orchestrated by a cybercriminal organization, in which the attack team sent Google employees a message with a malicious connection. Once a Google employee clicked on the malicious connection, the computer automatically sent an instruction to the attacker's C&C server, downloaded the remotely controlled Trojan horse, and became a zombie. The attacker obtained the administrator rights of the server by means of intranet penetration and brute force cracking. Employees' computers had been controlled remotely for months, and their data was stolen, causing immeasurable losses.
Stuxnet Attack
In 2010, the Stuxnet virus successfully attacked centrifuges in Iran. About 1000 centrifuges were scrapped within just two months. According to news reports, Stuxnet was a targeted cyberattack launched by multiple countries against facilities in Iran. A programming error allowed the worm to spread to other unsupported operating systems, finally leading to its discovery in June 2010.
Stuxnet exploited seven vulnerabilities, four of which were Zero-day attacks. Because the victim was not on the Internet and was not connected to the external network, Stuxnet was originally initiated by agents who inserted the USB flash drive into the target system or network. Stuxnet also applied a lot of stealth, camouflage, and deception tactics. For example, its vulnerability exploit targeted the system kernel level, in order to remain stealthy and avoid detection by the antivirus software. It also carefully monitored its usage of processor resources on infected computers and launched itself only if doing so would not slow down the computer, in order to avoid detection. Furthermore, it stole two companies' digital signatures, which were legal proof of programs. Companies typically had additional security protection for the digital signatures.
SolarWinds Supply Chain Incident
In December 2020, FireEye, a cyber security company, disclosed that a backdoor existed in a piece of its purchased software from SolarWinds, a network management software vendor. The backdoor communicated with third-party servers through HTTP. SolarWinds conducted an investigation into its software, which was purchased by customers around the world, and found that the software had been used as an entry point to penetrate multiple large companies. In addition, multiple government agencies might have been compromised; more than 90% of the world's top 500 companies were adversely affected. At least 300,000 large government agencies, enterprises, and institutions around the world have been adversely affected.
Characteristics of an APT Attack
- Well-organized attackers: Attacks are often carried out by organizations for military or political purposes, sometimes linked to a country, and often backed by sufficient financial resources.
- Explicit target: Attackers elaborately select targets, which are usually of high military, political, and economic value.
- Sophisticated methods: APT attacks involve multiple malicious code variants and frequent updates, and exploit zero day vulnerabilities. As such, traditional detection and defense technologies based on signature matching cannot effectively detect attacks.
- Hidden: APT attackers take significant care in hiding themselves. They do not construct a large number of packets to crush target servers like DDoS attacks do. Traffic-based defense is difficult to take effect. Throughout the entire process, advanced evasion technologies are used to avoid being detected by security devices. During an APT, there are no obvious anomalies in the system. Real-time detection at any given point of time or within a short window and frequent session detection technologies are difficult to detect abnormal packet-based attacks.
- Persistent: Attackers often are patient to carry out penetration and data breach during several months or even years.
Methods Used to Prevent an APT
APTs use customized malware, zero day vulnerabilities, or advanced evasion technologies to break through traditional defenses, such as firewalls, intrusion prevention systems, and antivirus devices. Huawei's Anti-APT and Big Data Security Solution uses a big data system to collect network-wide information, perform multi-dimensional assessments, accurately identify APT attacks, and effectively prevent attacks from compromising core information assets. The solution is comprised of the HiSec Insight Secutity Situation Awareness System.
- The NGFWs) to analyze data in the virtualized environment and detect unknown malicious files.
- Built on Huawei's mature commercial big data platform — FusionInsight — HiSec Insight Secutity Situation Awareness System (formerly CIS) performs multi-dimensional correlation analysis of massive data based on an Artificial Intelligence (AI) detection algorithm. It proactively detects a wide range of security threat events in real-time, tracing the attack behavior of the entire APT kill chain. The system also collects and stores multiple types of network information, helping users detect threats, conduct forensics, and ultimately eliminate threats.
Huawei HiSec Insight is designed for threat detection, threat blocking, forensics, source tracing, and threat response and handling, enabling full-process, closed-loop threat handling.
- Author: Jiao Cuicui
- Updated on: 2023-05-31
- Views: 5401
- Average rating:







