What Is MACsec?
Media Access Control Security (MACsec) is a secure communication method based on 802.1AE and 802.1X for local area networks (LANs). It provides identity authentication, data encryption, integrity check, and replay protection to protect Ethernet frames and prevent devices from processing attack packets.
Why Is MACsec Required?
Media Access Control Security (MACsec) is a secure communication method based on 802.1AE and 802.1X for local area networks (LANs). It provides identity authentication, data encryption, integrity check, and replay protection to protect Ethernet frames and prevent devices from processing attack packets.
Generally, most data is transmitted in plaintext on LAN links, which brings security risks. This makes the LAN prone to attacks, for example, the bank account information may be stolen or tampered with. MACsec can protect data frames transmitted over an Ethernet network, preventing information leak and malicious attacks.
- Data encryption: MACsec uses the AES-CMAC algorithm for encryption. The sender encrypts the data and transmits the data in ciphertext on the LAN link. The receiver decrypts the received encrypted data and then performs other processing.
- Integrity check: The receiver checks the integrity of received data to determine whether the data is tampered with. The sender calculates the Integrity Check Value (ICV) based on the entire data packet and encryption algorithm and adds it to the tail of the packet. After receiving the packet, the receiver calculates the ICV based on the data packet excluding the ICV field and the same encryption algorithm, and compares the obtained ICV with the ICV in the packet. If they are the same, the packet is considered complete and passes the check. Otherwise, the packet is discarded.
- Replay prevention: To prevent attackers from repeatedly sending obtained packets to attack the network, the receiver discards duplicate or out-of-order data packets by default. When data packets are transmitted on the network, the sequence of packets may be rearranged. The replay prevention mechanism allows data frames not to come in strict order. These out-of-order packets can be received if the specified window size is not exceeded. Otherwise, they are discarded. Assume that the replay prevention window size is a. If a packet whose sequence number is x is received, the next packet can be received only when its sequence number is greater than or equal to x+1-a.
What Are Application Scenarios of MACsec?
Scenario 1: Point-to-Point Data Transmission
Important data is transmitted between SwitchA and SwitchB. Point-to-point MACsec is deployed to protect data.
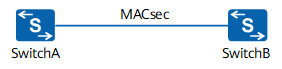
Point-to-point MACsec between switches
Scenario 2: Point-to-Point Data Transmission with Transparent Transmission Devices
SwitchC, SwitchD, and SwitchE are deployed between SwitchA and SwitchB, and point-to-point MACsec is configured between SwitchA and SwitchB to protect transmitted data. To ensure that SwitchA and SwitchB can perform MACsec session negotiation, enable Layer 2 protocol transparent transmission on SwitchC, SwitchD, and SwitchE.
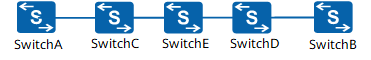
Configuring point-to-point MACsec to implement secure communication (with transparent transmission devices)
How Does MACsec Work?
The MACsec Key Agreement (MKA) protocol is responsible for establishing and managing MACsec security channels and negotiating keys used by MACsec. The following describes the basic concepts involved in the MKA protocol:
- The Secure Connectivity Association (CA) is a security association established and maintained by the key negotiation protocol. It is a set of two or more MACsec-capable members that use the same key and key algorithm suite on the LAN. The key used by CA members is called Secure Connectivity Association Key (CAK). MACsec supports only point-to-point connections. That is, a MACsec session is set up between two devices. Therefore, both ends of a MACsec session must use the same CAK. Two connected devices form a CA and use the same CAK.
- The Secure Association (SA) ensures the secure transmission of data frames between CA members. Each SA has one Secure Association Key (SAK) or a group of SAKs to encrypt frames. SAKs are generated based on CAKs using algorithms and are used to encrypt and decrypt data packets.
Operation Mechanism
The point-to-point MACsec interaction process consists of three phases: session negotiation, secure communication, and session keepalive.
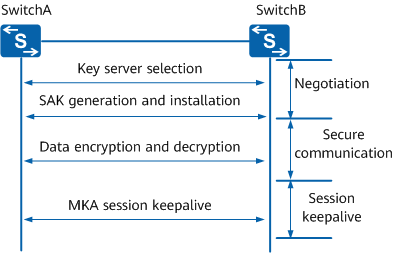
MACsec implementation
The three stages in session establishment are as follows:
Session negotiation
After MACsec is enabled on the interfaces of the two devices, a key server is selected based on the priority. You can set the priority of an interface. A smaller value indicates a higher priority. The interface with a higher priority is selected as the key server. If the two interfaces have the same priority, the Secure Channel Identifier (SCI) values of the interfaces are compared. The SCI consists of the interface MAC address and the last two bytes of the interface index. The interface with a smaller SCI value is selected as the key server.
The two devices are statically configured with the same CAK. The key server generates a SAK for encrypting data packets based on the statically configured CAK and delivers the SAK to the remote device.
Secure communication
The sender uses the SAK to encrypt data packets, and the receiver uses the SAK to decrypt data packets. Both devices can function as the sender or receiver, and their communication is protected by MACsec.
The SAK supports timeout interval setting. When a certain number of packets have been encrypted using one SAK or an SAK has been used for a certain period, the SAK needs to be replaced to improve key security.
Session keepalive
The MKA protocol defines an MKA session keepalive timer that specifies the timeout period of an MKA session. After MKA session negotiation is successful, the two devices exchange MKA protocol packets to ensure that the session is alive. The local device starts the timer after receiving MKA protocol packets from the remote device.- If the local device receives subsequent MKA protocol packets within the timeout period, it restarts the timer.
- If the local device does not receive MKA protocol packets within the timeout period, the local device considers the session insecure, disconnects from the remote device, and performs MKA session negotiation again.
- Author: Fu Li
- Updated on: 2022-11-10
- Views: 15858
- Average rating:







