What Is sFlow?
Sampled Flow (sFlow) is a traffic monitoring technology that collects traffic statistics by sampling packets and analyzes the traffic statistics. sFlow analyzes traffic on a per-interface basis to monitor traffic in real time, detect abnormal traffic, and locate the source of attack traffic in a timely manner, greatly facilitating routine inspection and maintenance for enterprises.
Why Do We Need sFlow?
Enterprise networks differ from carrier networks in that they are smaller, more flexible, and more likely to be attacked. To prevent and limit service interruptions, enterprises require a traffic monitoring technique to locate unexpected traffic as well as the source of an attack in a timely manner. This is where sFlow comes in. It provides interface-based traffic analysis, facilitating preventive maintenance on enterprise networks.
Differences Between sFlow and NetStream
NetStream can also collect and analyze network traffic statistics, but it is a network flow statistics collection technique. A NetStream-enabled network device needs to perform statistics collection and preliminary analysis on network flows and store the statistics in its buffer. The device exports flow statistics when its buffer is full or the flow statistics are aged out. Different from NetStream, sFlow does not require a buffer. In sFlow, network devices only sample packets, and a remote sFlow collector collects and analyzes traffic statistics.
sFlow has the following advantages over NetStream:
- Fewer resources and lower costs: sFlow does not need to create flow tables, so it uses only a small number of resources on network devices, lowering costs.
- Flexible collector deployment: The collector can be deployed flexibly, enabling traffic statistics to be collected and analyzed based on various traffic characteristics.
Application Scenarios of sFlow
Enterprises often have explicit requirements for traffic on device interfaces and the overall running status of devices. Enterprises require a traffic monitoring technique that samples packets on device interfaces to promptly discover abnormal traffic and the source of attack traffic, so that they can quickly rectify faults to ensure properly running of their networks. sFlow focuses on traffic on interfaces, traffic forwarding, and the overall device status, so it can be used to monitor and locate network exceptions, especially on enterprise networks.
As shown in the following figure, an sFlow agent is connected to a remote sFlow collector, so that traffic statistics can be collected and analyzed based on interfaces.
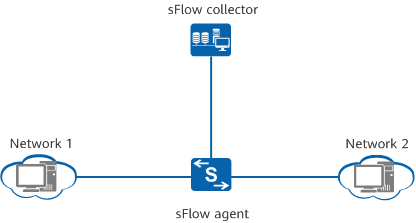
Typical sFlow networking
How Does sFlow Work?
Architecture of an sFlow System
As shown in the following figure, an sFlow system consists of an sFlow agent embedded in a Huawei device and a remote sFlow collector. The sFlow agent collects traffic statistics from an interface by sampling packets, and encapsulates the statistics into sFlow packets. When the sFlow packet cache overflows or sFlow packets are aged out (aging period: 1 second), the sFlow agent sends the sFlow packets to the sFlow collector. The sFlow collector analyzes the sFlow packets and displays the analysis results.
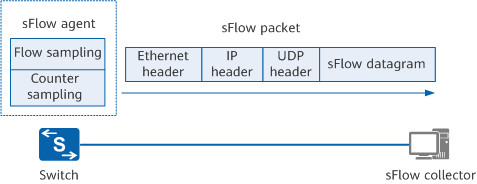
sFlow system
sFlow Packet
sFlow packets are encapsulated using UDP. By default, the destination port number of sFlow packets is the well-known port 6343. sFlow packets use the following header formats: Flow sample, Expanded Flow sample, Counter sample, and Expanded Counter sample. Expanded Flow sample and Expanded Counter sample are additions in sFlow version 5 and are extensions to Flow sample and Counter sample, respectively, but they are not compatible with earlier versions. All extended sampling content must be encapsulated with a header in Expanded Flow sample or Expanded Counter sample format.
sFlow Sampling
An sFlow agent provides flow sampling and counter sampling.
Flow sampling
With flow sampling, an sFlow agent samples packets in the specified direction on a specific interface based on a sampling rate, and parses the packets to obtain information about packet data content. Flow sampling focuses on traffic details, facilitating monitoring and analysis of traffic behaviors on the network.
Field |
Description |
|---|---|
Raw packet |
Records the entire packet header or part of the packet header, depending on the configuration. |
Ethernet Frame Data |
Records Ethernet headers in Ethernet frames. |
IPv4 Data |
Records IPv4 headers in IPv4 packets that are forwarded at Layer 3. |
IPv6 Data |
Records IPv6 headers in IPv6 packets that are forwarded at Layer 3. |
Extended Switch Data |
Records VLAN translation and 802.1Q priority mapping information in Ethernet frames. VLAN ID 0 indicates an invalid VLAN. |
Extended Router Data |
Records routing information of packets. |
Counter sampling
With counter sampling, an sFlow agent periodically collects traffic statistics on an interface. The following table describes the main fields in counter sampling packets. In contrast to flow sampling, counter sampling focuses on traffic statistics on an interface instead of traffic details.
Field |
Description |
|---|---|
Generic Interface Counters |
Records basic interface information and traffic statistics on interfaces. |
Ethernet Interface Counters |
Records traffic statistics on an Ethernet interface. |
Processor Information |
Records CPU usage and memory usage of a device. |
Optical SFP/QSFP metrics |
Records indicator data of SFP/QSFP optical modules. |
- Author: Li Jiyuan
- Updated on: 2022-11-09
- Views: 4658
- Average rating:







