What Is Application Identification?
As the Internet quickly develops, Internet applications have undergone tremendous changes, from web browsing, email, and FTP download to P2P applications, games, videos, and mobile interconnections. Diversified applications have become widespread on the Internet.
The biggest obstacle for network administrators is to accurately identify various applications and control their traffic effectively. Traditional application identification technologies use protocols and port numbers to identify applications. However, as applications become more complex, these technologies cannot meet refined control requirements. To address this issue, service awareness (SA) application identification is introduced.
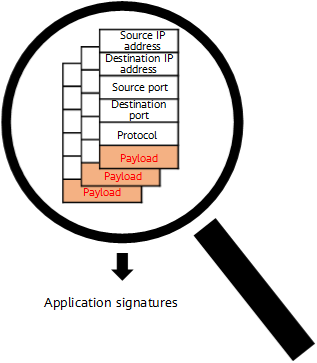
SA application identification is an application signature extraction and matching technology. It extracts certain fields or behavior signatures of packets and matches them with the SA signature database to identify applications.
Protocol Identification vs Application Identification
The traditional protocol identification technology checks only the quintuple information in packets and identifies applications based on the port number and protocol contained in the packets. Although this technology has high detection efficiency, its application scope becomes smaller and smaller.
On the one hand, different applications that use the same protocol and port number cannot be distinguished in a more refined manner. For example, web games and videos use HTTP and port 8080 for data transmission, meaning that these two application types cannot be effectively distinguished based on the port number and protocol.
On the other hand, one protocol can be used by multiple applications, and one application may also use multiple protocols. An example of this is P2P, which is a standard protocol that can be used by multiple applications, such as Thunder, eMule, and FlashGet. If protocol identification is used for application control, it is very likely to cause mistakes.
P2P applications
For another example, Thunder uses multiple protocols, such as HTTP, P2P, and FTP, to transfer files. If protocol identification is used for application control, it is inevitable that some applications are not identified.
Protocols used by Thunder
SA application identification can resolve these problems. In addition to quintuple information, SA detects packets' application-layer information. It accurately identifies various applications in packets by extracting the packets' application-layer signatures.
Three Mainstream Technologies of Application Identification
- Signature identification: This is the most basic technology for SA application identification. It identifies applications by parsing the application signatures carried in packets.
Different applications typically use different protocols, and each protocol has its own signatures. These signatures may be specific ports, character strings, or bit sequences. In addition to parsing the traditional quintuple information of packets, signature identification also parses the application-layer information of packets to obtain more signatures for application identification.
Some application protocol signatures are spread over multiple packets rather than only a single packet. In such cases, you need to collect and analyze the signatures of multiple packets to identify applications.
Signature identification - Correlation identification: This is mainly used to identify applications based on multi-channel protocols.
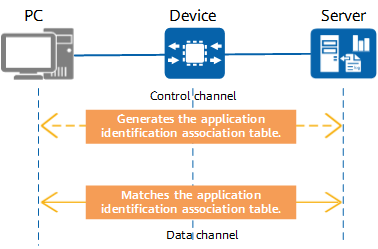
More and more applications use multi-channel protocols to transmit voice, video, and files. These protocols, such as FTP, SIP, and H.323, use separate control and data channels. Specifically, they use control channels to negotiate communication parameters (such as port information) for establishing data channels, and use data channels to transmit service data. Signature identification technology can identify applications of control channels instead of data channels, as the latter are dynamically negotiated and have no identifiable signatures.
Correlation identification is dependent on signature identification, which is used to identify the applications carried by control channel packets. In addition, the data channel information is extracted from control channel packets and recorded in an application identification association table. Subsequently, data channel packets are identified according to the association table and marked as the corresponding applications. In this way, applications can be identified from multi-channel protocol packets.
Correlation identification - Behavior identification: This is more complex than the preceding two technologies.
Some complex applications on the Internet are difficult to identify by signature keywords. Furthermore, many encrypted applications cannot be identified because the signatures are obfuscated due to data encryption. The existing signature identification technologies cannot identify some complex applications based on conventional signatures. Behavior identification can identify the applications carried in packets by extracting the packets' behavior signatures, which may vary with different applications. To accurately identify an application, you must obtain and analyze a large number of traffic samples and extract unique behavior signatures.
Usually, behavior signatures include the proportion between the upstream traffic and downstream traffic, packet sending interval, and packet length change patterns. Behavior identification technology accurately identifies applications by thoroughly investigating and choosing multiple behavior signatures.
Different identification technologies apply to different types of protocols and are not interchangeable. Typically, multiple technologies need to be used to achieve optimal identification.
What Is the SA Signature Database?
Signature identification is critical to application identification. Huawei security center analyzes and extracts the signatures of more than 6000 common applications from a large number of Internet applications and stores them in the SA signature database. As more and more Internet applications appear, the SA signature database is constantly updated. You can log in to Huawei security center (isecurity.huawei.com) to download the SA signature database and load it onto Huawei network devices.
After the latest SA signature database is loaded onto Huawei network devices, the devices can identify and control various applications in traffic.
Currently, Huawei SA signature database classifies Internet applications into five categories based on application attributes. Each category contains multiple sub-categories. Network administrators can control a category of applications in a unified manner, or control one or several applications separately.
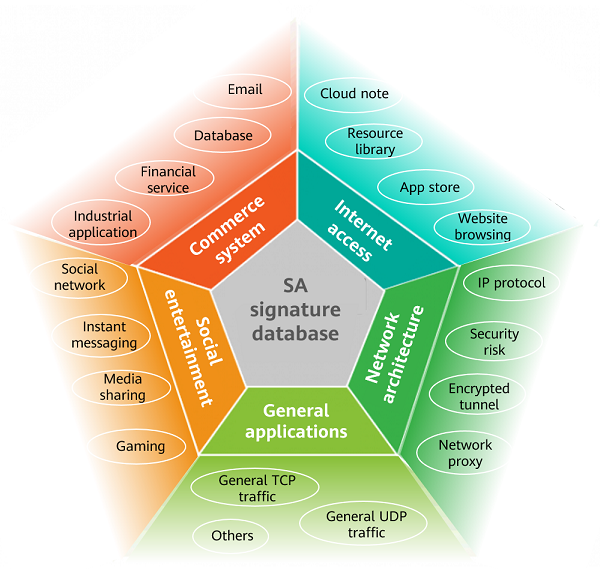
SA signature database
What Are the Application Control Methods Based on Application Identification?
- Application-based access control: Allows or forbids users to access certain applications. For example, allows users to access office-related applications and forbids users to access video or game applications that affect work efficiency.
- Application-based bandwidth management: Limits the bandwidth for users to access certain applications. For example, it limits the bandwidth for video or game applications to 100 Mbit/s, and ensures that the bandwidth for office-related applications is 200 Mbit/s.
- Application-based intelligent link selection: Users access some applications through specified links. For example, users access office-related applications through high-speed links, and video or game applications through low-speed links.
- Author: Xi Youyuan
- Updated on: 2024-01-10
- Views: 9737
- Average rating: