What Is CVE?
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed cyber security vulnerabilities. IT personnel and security researchers can use this list to obtain vulnerability details and determine the priorities of vulnerabilities to be fixed based on vulnerability scores.
In the CVE, each vulnerability is numbered in a specific format, for example, CVE-1999-0067, CVE-2014-10001, and CVE-2014-100001. A CVE ID uniquely identifies a vulnerability. CVE IDs are assigned by a CVE Numbering Authority (CNA), which is mainly comprised of IT vendors, security vendors, and security research organizations.
How Is CVE Formed?
CVE vulnerability information is hosted on the website of the CVE organization (https://cve.mitre.org/), a nonprofit organization originally founded by the Massachusetts Institute of Technology in 1999. The CVE information on the website is public and can be free to use if permitted by law.
Each vulnerability is assigned a CVE ID in the format of CVE-year-number. For example, CVE-2019-0708 indicates the Remote Desktop Services Remote Code Execution Vulnerability.
CVE is published by CNAs. Currently, there are about 100 CNAs, consisting of IT vendors, security companies, and security research organizations around the world. Any agency or individual can submit a vulnerability report to a CNA, and the CNA-based organization also encourages users to look for vulnerabilities to enhance the security of their products.
Not all vulnerabilities can be recorded in the CVE. The CNA determines whether to assign a CVE ID to a vulnerability based on the following rules:
- A vulnerability can be fixed independently, and is not coupled with other vulnerabilities.
- A software or hardware vendor acknowledges the existence of this vulnerability or releases an official notice.
- A vulnerability affects only one code database. If a vulnerability affects multiple products, a CVE ID is assigned to each product.
According to the preceding rules, an ID is assigned to a vulnerability, a description added for it, and the vulnerability is published on the CVE website. Each CVE entry contains the following information:
- Description: a brief description of the vulnerability source and attack method.
- Reference: a summary of reference information about a vulnerability, such as vulnerability bulletins and emergency response suggestions.
- Published CNA: a CNA that issued this CVE entry.
- Release date: when the CVE was released.
To sum up, CVE organizations work with CNAs to identify, define, and publicly release cyber security vulnerabilities to form an industry standard for vulnerability information.
What Are CVE Functions?
Without CVEs, each IT vendor or security organization has to maintain its own vulnerability database. The disadvantage of this is that the vulnerability information is inconsistent and therefore is difficult to be shared across the industry. The CVE assigns unique IDs to identify vulnerabilities and standardizes their descriptions, providing the following three advantages:
- IT personnel and security researchers can access the same vulnerability information, helping them effectively prioritize and rectify vulnerabilities.
- Information can be exchanged across different systems easier based on CVE IDs.
- Developers of security products or tools can use the CVE as a reference to evaluate products' vulnerability detection.
Some may have concerns that publicly disclosing vulnerabilities helps hackers exploit them to launch attacks. However, the advantages of CVEs outweigh the disadvantage. First, CVEs disclose only known vulnerabilities, which hackers can obtain from other sources. Second, only IDs are assigned to vulnerabilities, and their details and rectification suggestions can be temporarily hidden until the IT vendor releases fixes, such as patches. Finally, sharing vulnerability information across the industry can speed up the release of rectification suggestions.
You are advised to include the CVE IDs in the security event report of a security product or tool. In this way, users of the security product or tool can quickly obtain information about vulnerabilities on the network and takes suitable measures based on vulnerability rectification suggestions.
The CVE website provides limited information, and the CVE is mainly used to assign unique IDs. For more vulnerability information, such as rectification suggestions, impacts, and scores, you need to consult other resources such as IT vendors' websites and other vulnerability databases. You need to obtain more information (such as rectification suggestions, impacts, and scores) from IT vendors' websites and other vulnerability databases. However, it is undeniable that CVE IDs link the preceding pieces of information, enabling vulnerability information to be quickly retrieved based on the CVE IDs.
Relationship Between the CVE and CVSS
The Common Vulnerability Scoring System (CVSS) is a widely used standard to score vulnerabilities. A CVSS score, ranging from 0.0 to 10.0, indicates vulnerability severity from least to most severe. CVSS scores are key information for vulnerability scanning tools and security analysis tools.
A CVE is merely a dictionary of vulnerabilities. A CVE list does not contain CVSS scores. To view CVSS scores, use another vulnerability management system (for example, https://www.cvedetails.com/). IT personnel prioritize vulnerabilities to be fixed based on CVE information and CVSS.
Application of CVE on Security Products
CVE vulnerability information must be updated effectively during development of security products to help the products detect as many CVE vulnerabilities as possible and ensure user network security.
Quickly update signature databases based on CVE information.
The IPS function detects intrusion behaviors based on a related signature database, the main source of which is vulnerability signatures. Security teams use the CVE to track the latest vulnerabilities, quickly release new signatures, and block attacks to protect users' networks even before IT vendors release fixes.
Incorporate CVE information into log reports.
In the intrusion event log report, attack details contain the CVE IDs and links to vulnerability reference information. You can learn about vulnerability details and formulate security measures accordingly.
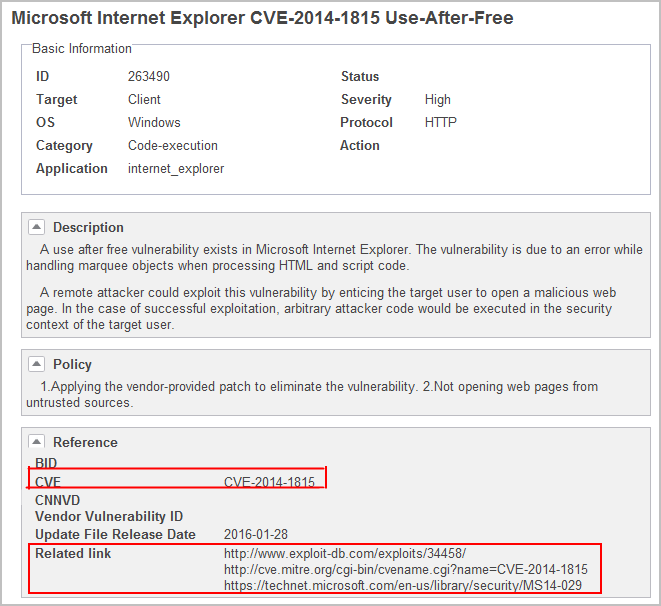
CVE information in log reports
IPS threat knowledge database released by the security center
The security center releases a more detailed IPS threat knowledge database, containing vulnerability levels and rectification suggestions, based on CVE information and CVSS scores.
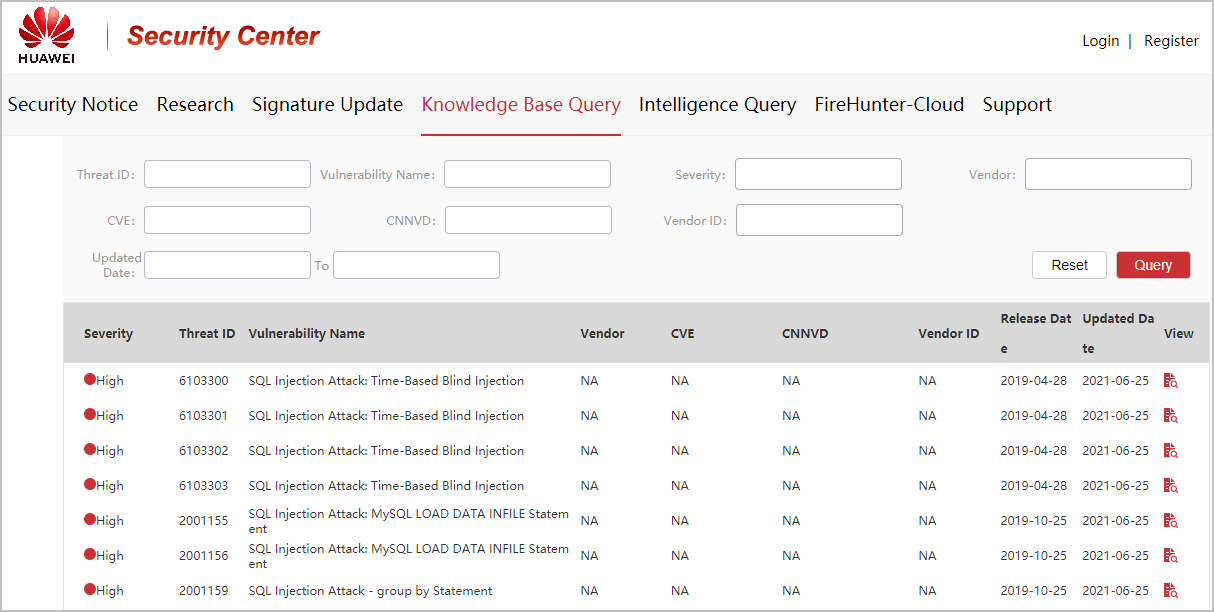
IPS threat knowledge database
- Author: Liu Shui
- Updated on: 2023-11-16
- Views: 5205
- Average rating:







