What Is Free Mobility?
Free mobility allows users on a campus network to have consistent permissions regardless of their locations and IP addresses. With these permissions, users can access specific resources or other user groups.
Why Do We Need Free Mobility?
In an enterprise network, users want to have consistent access experience regardless of their locations and IP addresses used, which cannot be met by traditional policy management. The figure below shows the four typical applications that drive free mobility.
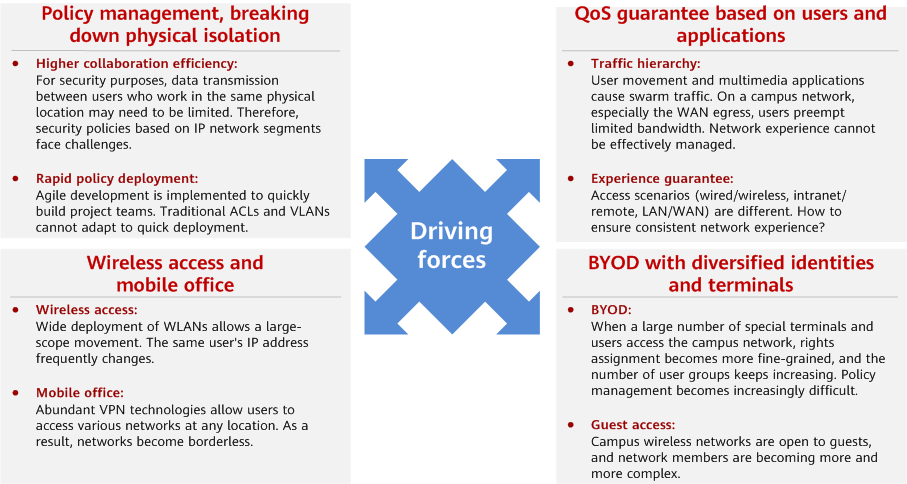
Driving forces for free mobility
Policy Management, Breaking down Physical Isolation
In an enterprise's traditional campus network, to construct a wired network, the network administrator needs to plan the office cubicles of each department, assign VLANs based on access ports of access switches, allocate specific IP network segments to hosts in different VLANs, and formulate service policies based on IP addresses of switches, routers, and firewalls. However, the new office mode brings the following requirements:
- Higher collaboration efficiency
Nowadays, users from different departments or even different companies may participate in the same project. These users need to work in the same physical location to improve collaboration efficiency. However, for the purpose of enterprise information asset security, data transmission between these users may need to be limited. Campus network construction based on office cubicle planning is inapplicable to such a scenario.
- Rapid policy deployment
With enterprise service expansion, networks are upgraded and users move more frequently. This requires the network administrator to deploy policies more quickly.
QoS Guarantee Based on Users and Applications
Network Admission Control (NAC), a traditional network security technology, controls users' network access rights based on user identifies but does not guarantee their network experience.
As service types become increasingly complex, enterprise employees have increasingly high requirements on network bandwidth and delay. Actually, the bandwidth on an enterprise network, especially the bandwidth at the enterprise network egress, cannot be increased continuously. A higher bandwidth means a higher cost.
To find a balance between the cost and experience, important and common users and services need to be differentiated and experience needs to be ensured for them accordingly. However, traditional Quality of Service (QoS) is based only on IP addresses and ports but not users and applications. Therefore, it cannot adapt to new campus networks.
Network border devices must be capable of identifying both users and applications to implement QoS based on them. In addition, QoS policies must be quickly deployed based on users and applications.
Wireless Access and Mobile Office
Traditional campus networks take access control measures for wireless and VPN remote access users similar to those on wired networks. Different types of users can be distinguished based on IP addresses allocated to them, and service policies are formulated on network devices based on these IP addresses.
Wireless and remote access technologies bring convenience in the office environment but pose security risks.
To prevent unauthorized users from accessing the campus network through malicious attacks and rogue APs, users must be authenticated before they are allowed to access wireless networks.
A user may use multiple IP addresses in different ranges to access the campus network. As such, service policy configuration on the network becomes more complex and difficult to manage.
BYOD with Diversified Identities and Terminals
Wireless access and VPN remote access extend the geographic scope of the campus network, while BYOD extends the types of users and terminals that can access the campus network.
On a campus network with a limited number of user types, the traditional dynamic VLAN and dynamic ACL technologies can be used to control users' access rights. However, after BYOD is introduced, terminal types, terminal homing relationships, and access locations can also be used to classify users. As a result, an enterprise may have dozens or even hundreds of user types.
If traditional dynamic VLAN and dynamic ACL technologies are used, dozens of times more VLANs needs to be pre-configured and IP network segments need to be reserved on network devices for such a large number of user types. This complicates network deployment and maintenance.
Network Architecture of Free Mobility
The following figure shows the overall network architecture of free mobility. User terminals initiate authentication. The access layer transparently forwards user traffic at Layer 2. Authentication devices authenticate users, and policy enforcement devices control user access rights. An authentication device and a policy enforcement device can be the same physical device or different physical devices. Border devices ensure the forwarding priority of specific users at the egress. Static resources are server resources that users can access. These resources can be managed as security groups by a controller.
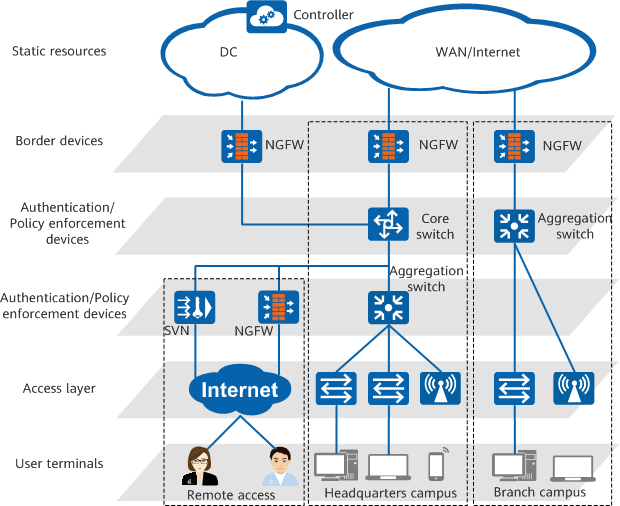
Network architecture of free mobility
The free mobility solution involves the following key roles:
- Controllers: work with network devices to authenticate users and deliver policies, decoupling service policies from IP addresses. Huawei iMaster NCE-Campus can function as a controller to deliver policies.
- Access devices: authenticate terminals to determine whether to allow the terminals to access the network and control their network access rights. The access devices include switches and firewalls. This document focuses only on switches.
- Terminals: provide human-machine interfaces for user authentication and resource access. The terminals include PCs, laptops, smartphones, tablets, and dumb terminals.
How Does Free Mobility Work?
Security Group
A security group, also called a user control list (UCL) group, is an important concept in free mobility.
It is an abstracted and logical set of communication objects on the network. Security group members can be network terminals such as PCs and smartphones. They can be statically added by an administrator or dynamically added after authentication.
An administrator can add the users requiring the same access control policy to the same security group, and configure an access control policy for the group to meet the network access requirements of all users in the group. Network objects are added to the same security group based on their similarities in network access, and obtain the same rights based on the policy configured for the security group. For example, an R&D group is a set of individual hosts, a printer group is a set of all printers on the network, and a database server group is a set of server IP addresses and ports. Compared with the solution in which access control policies are deployed for each user, the security group-based access control solution greatly reduces the administrator's workload.
Implementation
The following figure shows the implementation of free mobility, which consists of six steps.
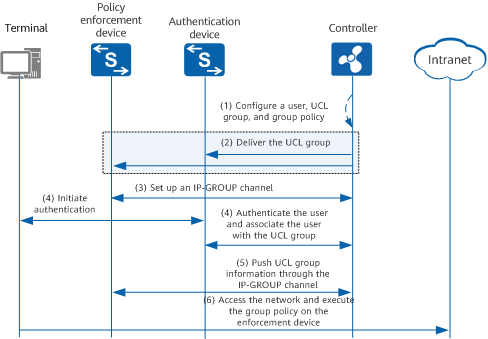
Implementation of free mobility
- On the web UI of a controller, an administrator creates a user account and UCL group, and adds the user account to the UCL group. All users can access the network only after being authenticated. Then, the administrator defines the network access policy (that is, group policy) for the user based on the UCL group.
- The controller delivers the UCL group configured by the administrator to all associated switches (policy enforcement device and authentication device), enabling the switches to identify the UCL group to which the user belongs.
- The policy enforcement device requests to set up an IP-GROUP channel with the controller.
- The user initiates authentication. During the authentication, the controller associates the user with the UCL group based on the user login information. After the authentication succeeds, the controller collects IP addresses of all online users.
- The controller pushes UCL group entry information (the group to which the user belongs is delivered as the authorization result) to the policy enforcement device through the IP-GROUP channel, and records the mapping between UCL groups and the source and destination IP addresses.
- The user accesses the network. After receiving user packets, the policy enforcement device attempts to identify security groups to which the source and destination IP addresses of the packets correspond, and enforces UCL group-based policies for the packets.
Free Mobility vs. NAC vs. Policy Association
Free mobility, NAC, and policy association are all technologies for user access control.
Free mobility manages users based on security groups and ensures that users in a security group can access the same resource at different locations and at different times.
NAC is an end-to-end security control technology that authenticates access clients and users to ensure network security.
Policy association centrally manages user access policies on gateway devices and enforces these user policies on gateway and authentication access devices, simplifying configuration on large campus networks.
- Author: Gu Suqin
- Updated on: 2023-03-28
- Views: 4164
- Average rating:







