What Is Microsegmentation?
Microsegmentation is a security isolation technology that groups data center (DC) services based on certain rules and deploys policies between groups to implement traffic control. Traditionally, subnets are created for DCs based on coarse-grained granularities such as VLAN IDs or VXLAN Network Identifiers (VNIs). Microsegmentation supports more fine-grained and flexible grouping modes, for example, grouping based on IP addresses, MAC addresses, and VM names. This can further narrow down security zones to implement fine-grained service isolation and enhance network security.
Why Microsegmentation?
On traditional data center networks, internal traffic is considered secure and external traffic is considered insecure. Therefore, firewalls need to be deployed at the border of the data center network to analyze and process traffic entering and leaving data center networks (north-south traffic). Security analysis technology for traffic on border devices is also known as border security technology.
With the proliferation of data storage and applications, the major traffic on data center networks changes from north-south traffic to east-west traffic. As such, security control is crucial to internal traffic. When attacks traverse the border, the data center network faces severe security risks, and attackers can randomly attack services on the data center network. Therefore, cloud-based DCs require comprehensive protection for internal and external traffic. If all traffic between VMs in a DC is diverted to the centralized firewall, requirements for flexible distributed and scalable deployment of the DC cannot be met and performance and capacity expansion bottlenecks may occur.
Microsegmentation implements more fine-grained granularities than subnets. It divides the internal network of a DC, and applies security policies to traffic between all groups. In this way, refined service policy control can be implemented to restrict the lateral movement of attacks on the network and enhance security. This can be compared to dividing a ship into water-tight compartments to reduce floodability of the ship, and thereby prevent sinking.
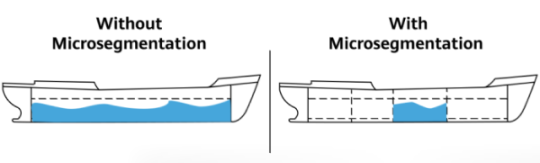
Security protection without and with microsegmentation
Microsegmentation vs. VLAN, ACL, and Firewall
Network segmentation is not a new technology. Traditional networks use firewalls, VLANs, and access control lists (ACLs) to isolate service traffic. However, these technologies have some limitations:
- VLANs are configured to isolate services based on subnets and cannot isolate servers in the same subnet.
- ACLs can be configured to isolate servers. However, a data center network has a large number of servers. If services on servers need to be isolated, a large number of ACL rules need to be configured, resulting in complex configuration and maintenance. In addition, network devices have limited ACL resources and cannot meet requirements for deploying a large number of ACL rules.
- Typically, firewalls are deployed only on the border connecting the DC to external networks. Of course, a firewall can be deployed on each interconnection node in a DC for internal isolation. This requires a large number of firewalls, meaning a large amount of hardware investment and heavy configuration and maintenance workloads.
This is where microsegmentation comes in.
- Microsegmentation enables more fine-grained segmentation, for example, segmentation based on IP addresses, IP network segments, MAC addresses, and VM names.
- It divides a network into several segments based on grouping rules and applies policies to control traffic between these segments. In this way, data packets can only be transmitted between specific nodes.
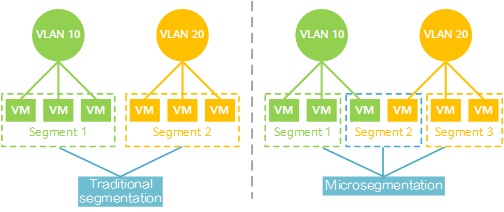
Comparison between traditional network segmentation and microsegmentation
Benefits of Microsegmentation
- More refined and flexible security isolation: Microsegmentation can define groups based on discrete IP addresses, MAC addresses, and VM names, enabling more refined and flexible definition of security zones.
- Smaller attack surface: Microsegmentation manages service resources by segment and strictly controls access between services based on the minimum permission principle to implement the zero-trust security model. This minimizes the attack surface and prevents attackers and abnormal east-west traffic, ensuring internal security.
- Distributed security: The microsegmentation solution implements distributed security control. The nearby access switch filters service traffic. In this way, east-west traffic does not need to be centrally forwarded to the firewall for security isolation. This reduces network bandwidth consumption and prevents the centralized control point from becoming a traffic bottleneck.
How Does Microsegmentation Work?
Based on the concept of security zones, microsegmentation groups DC services based on certain rules and implements traffic control through inter-group policies. It implements fine-grained isolation between groups based on the following elements:
- End point group (EPG): A group of entities that carry services, such as servers and VMs. EPGs can be defined based on IP addresses, MAC addresses, VM names, and applications.
- Group-based policy (GBP): policy for traffic control within an EPG and between EPGs.
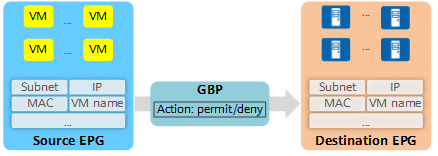
EPG/GBP implementation
In the Huawei CloudFabric Solution, microsegmentation delivers EPG information and GBPs to leaf nodes of the VXLAN network through APIs between the cloud platform, iMaster NCE-Fabric (Huawei's automated and intelligent platform integrating management, control, and analysis functions), and switches, so that service traffic can be securely filtered on nearby access nodes.
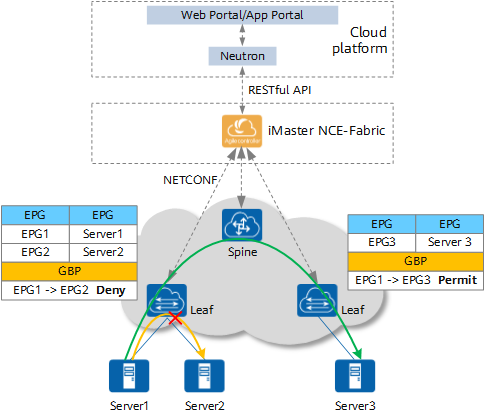
Microsegmentation architecture
- Author: Gao Yangyang
- Updated on: 2021-10-22
- Views: 8730
- Average rating:







