What Is a Traffic Policy?
Traffic policy technology is a network traffic management mechanism. A traffic policy classifies packets with the same characteristics into a class and provides the same service for these packets. By configuring traffic policies, you can define traffic classification rules to separately process the traffic matching the rules, reducing the loss caused by network congestion.
Why Do We Need Traffic Policies?
In daily life, traffic rules are used to classify vehicles and specify the behavior that each type of vehicle needs to comply with to relieve traffic congestion and improve vehicle passing efficiency. For example, a vehicle that turns right must drive on the right, and a vehicle that is on duty can pass first and quickly. These are typical traffic rules. In telecommunications, traffic policy technology is a network traffic management mechanism and belongs to modular quality of service (QoS) command line interface (MQC) in QoS technologies. Traffic policies can be regarded as traffic rules for network traffic. Traffic policies can maintain the traffic transmission order without increasing network bandwidth consumption, effectively relieve network congestion, and safeguard real-time network services.
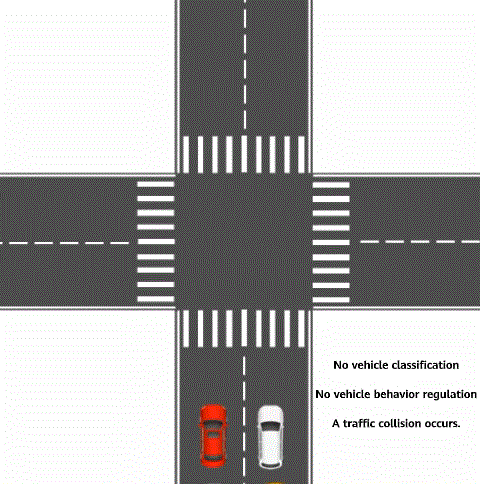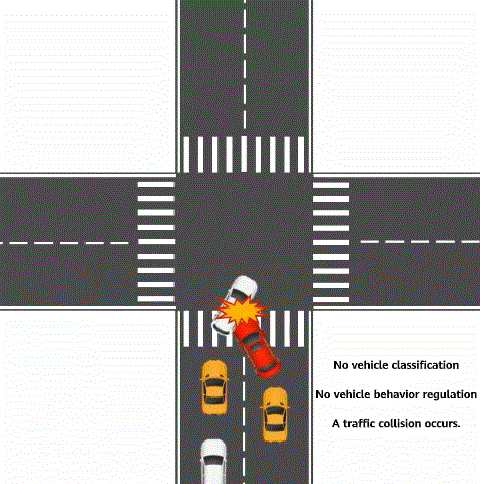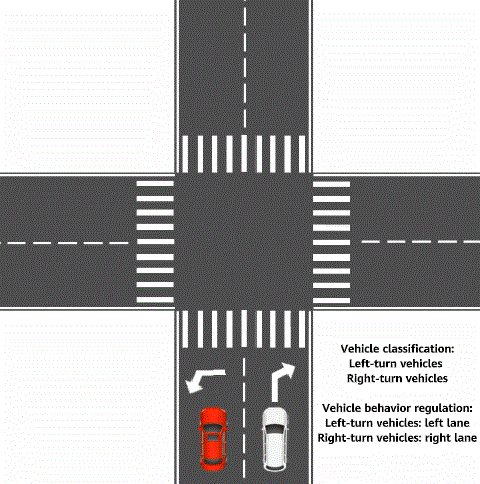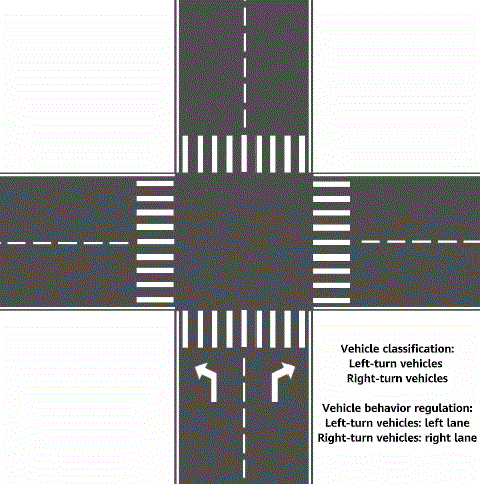
Traffic rule for vehicle classification and vehicle behavior regulation
The implementation of a traffic policy for network traffic is similar to that of a traffic rule for vehicles. The traffic classification function is used to classify traffic, and then the traffic behavior function is used to customize the behavior to be complied with for each type of traffic. For example, traffic can be classified based on service priority. Traffic of a high-priority service is transmitted first, and traffic of a low-priority service is transmitted later. In this way, the traffic transmission efficiency on the network is maximized.
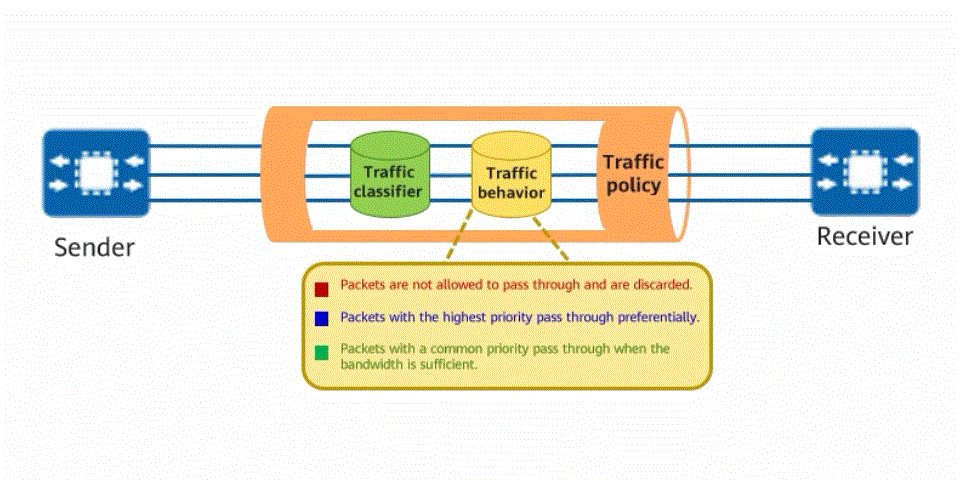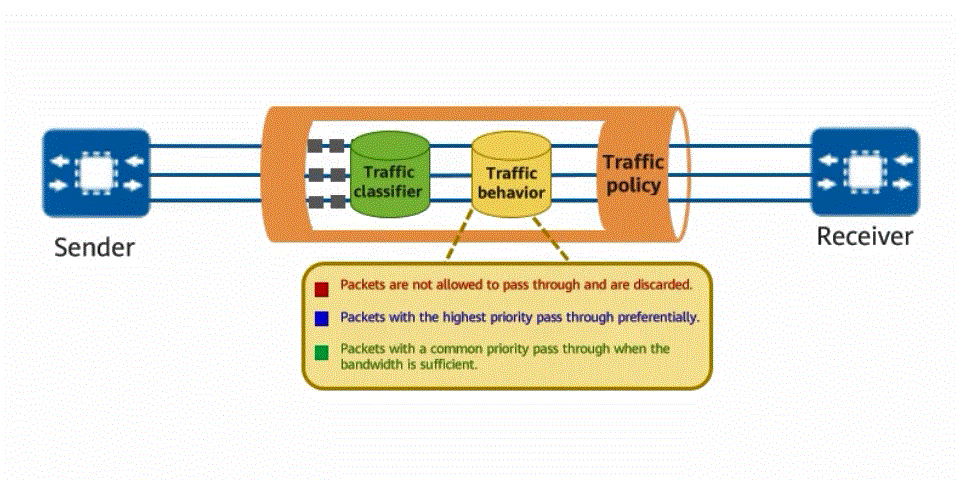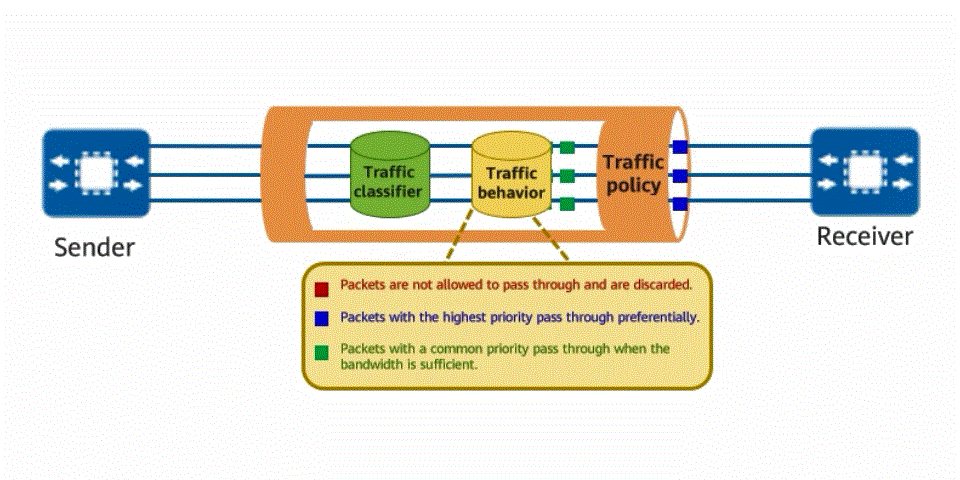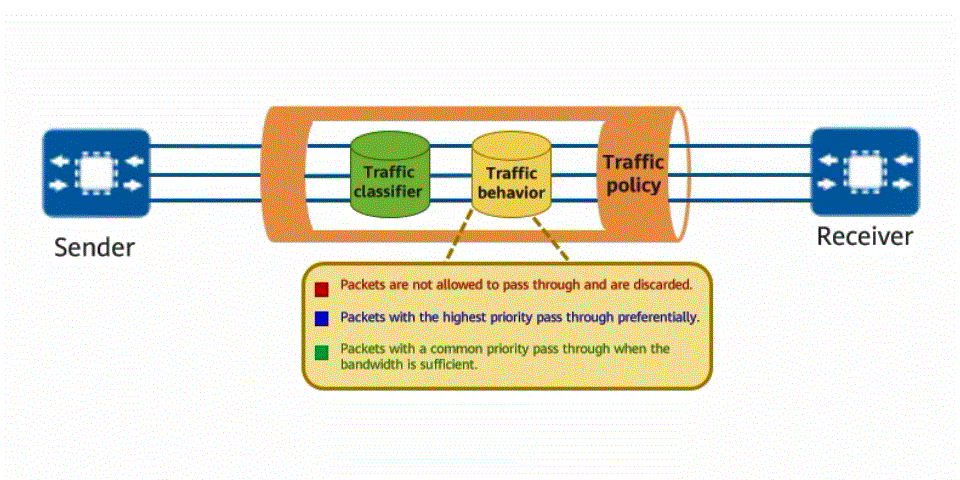
Traffic policy for traffic classifier and traffic behavior defining
How Is a Traffic Policy Implemented?
To implement a traffic policy, perform the following steps:
- Configure a traffic classifier. The prerequisite for effective traffic management is to identify traffic. You can define a group of traffic matching rules to sort out the traffic to be managed. This process is called traffic classification.
- Configure a traffic behavior to provide different services for traffic. A service can be defined in the traffic behavior. For example, to provide the VIP service for a certain type of important traffic, you can re-mark the priority of the corresponding packets and assign the highest priority to the packets in the traffic behavior.
- Configure a traffic policy, and bind the traffic classifier and traffic behavior to the traffic policy.
- Apply the traffic policy in the corresponding view as required.
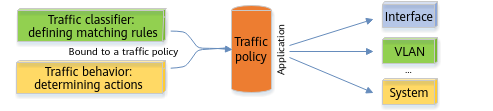
Implementing a traffic policy
Traffic Classifier
- Name of the traffic classifier, which is bound to a traffic behavior. You can run the traffic classifier command to create a traffic classifier.
- Traffic classification rules in the traffic classifier. You can run the if-match command to create a traffic classification rule. The device supports various traffic classification rules, including link-layer rules (Layer 2 rules), network-layer rules (Layer 3 rules), and ACL rules. The following table describes common traffic classification rules.
Table 1-1 Common traffic classification rules
Traffic Classification Rule
Matching Rule
Link-layer rule (Layer 2 rule)
MAC address, VLAN ID, and 802.1p priority
Network-layer rule (Layer 3 rule)
DSCP priority and IP precedence
ACL rule
ACL
Multiple matching rules can be defined in a traffic classifier, and the logical relationships between them can be AND or OR.
- OR: A packet matches a traffic classifier as long as it matches any rule in the traffic classifier.
- AND: If a traffic classifier contains ACL rules, a packet matches the traffic classifier only when it matches one ACL rule and all the non-ACL rules. If a traffic classifier does not contain any ACL rules, a packet matches the traffic classifier only when it matches all the rules in the traffic classifier.
For example, to create a traffic classification rule for identifying packets with VLAN ID 120, run the following commands:
Step 1 traffic classifier c1 // Create a traffic classifier named c1. Step 2 if-match vlan-id 120 // Create a rule for identifying packets with VLAN ID 120 in traffic classifier c1.
Traffic Behavior
To create a traffic behavior, specify the following:
- Name of the traffic behavior, which is bound to a traffic classifier. You can run the traffic behavior command to create a traffic behavior.
- Actions in the traffic behavior. The purpose of classifying packets through traffic classifiers is to provide different services for different types of packets. Different services need to be defined through traffic behaviors. One or more actions can be defined in a traffic behavior. The following table describes common actions in traffic behaviors.
Table 1-2 Common actions in traffic behaviors
Action in a Traffic Behavior
Description
Packet filtering
The device determines whether to discard or forward packets based on traffic classification results.
Packet re-marking
The device re-marks the priority of packets matching traffic classification rules. Packets of services that are sensitive to delay and service quality can be re-marked with a high priority so that they can be preferentially scheduled or forwarded.
Packet redirection or policy-based routing
The device redirects packets matching traffic classification rules to the specified location for processing.
Traffic statistics collection
The device collects statistics on the number of packets and bytes in packets matching traffic classification rules, which facilitates fault diagnosis and troubleshooting.
Traffic policing
The device controls the traffic rate within a bandwidth limit and discards excess traffic when the traffic rate exceeds the limit.
Step 1 traffic behavior b1 // Create a traffic behavior named b1. Step 2 car cir 4096 // Configure a traffic policing rule in traffic behavior b1. Step 3 statistics enable // Enable traffic statistics collection in traffic behavior b1.
Traffic Policy
The previously configured traffic classifier and traffic behavior are independent and must be associated with each other. A traffic policy binds them and the actions defined in the traffic behavior are taken on packets of specific types. Multiple pairs of traffic classifiers and traffic behaviors can be bound to a traffic policy.
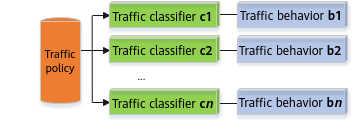
Binding multiple pairs of traffic classifiers and traffic behaviors to a traffic policy
Step 1 traffic policy p1 // Create a traffic policy named p1. Step 2 classifier c1 behavior b1 // Bind traffic classifier c1 to traffic behavior b1.
Applying a Traffic Policy
After a traffic policy is configured, determine whether the service traffic to be controlled by the traffic policy passes through a physical interface, a VLAN, a VLANIF interface, the system, or a card, and then apply the traffic policy in the corresponding view.
Step 1 vlan 10 // Enter the view of VLAN 10. Step 2 traffic-policy p1 inbound // Apply the traffic policy to the inbound direction of VLAN 10.
Typical Application of a Traffic Policy
As shown in the figure, voice, video, and data services are transmitted on a network. When a large amount of service traffic enters the network, congestion may occur due to insufficient bandwidth. Different bandwidth guarantees must be provided for the voice, video, and data services in descending order of priority. Voice, video, and data services are transmitted in VLAN 120, VLAN 110, and VLAN 100, respectively. A traffic policy can be configured to implement traffic policing and packet re-marking. Voice packets are provided with the maximum bandwidth and highest priority to ensure that voice packets are preferentially forwarded, video packets are provided with the medium bandwidth and medium priority, and data packets are provided with the minimum bandwidth and lowest priority. In addition, Device2 connected to the uplink interface of Device1 processes packets based on their priorities, ensuring the quality of various services.
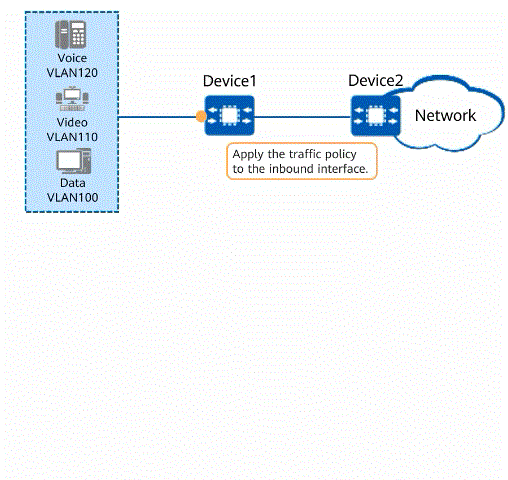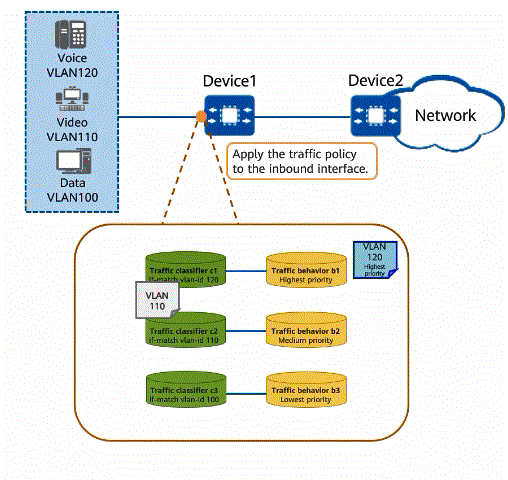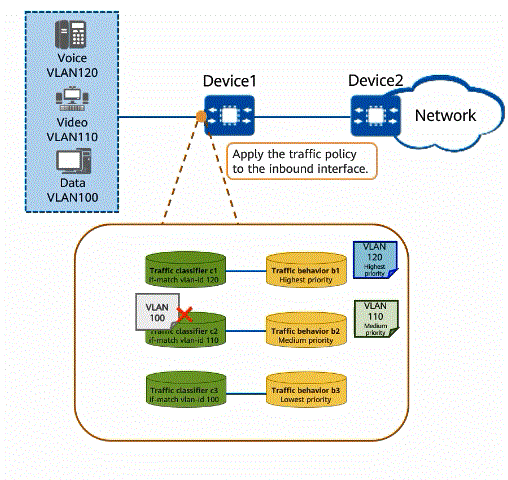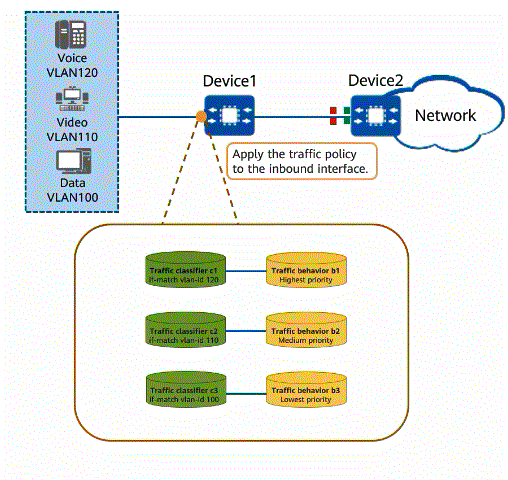
Using a traffic policy to process different service traffic
The configuration roadmap is as follows:
- Configure traffic classifiers on Device1 to classify voice, video, and data packets based on VLAN IDs.
- Configure traffic behaviors on Device1 to perform traffic policing and re-mark priorities of different service flows.
- Bind the configured traffic behaviors and traffic classifiers to a traffic policy and apply the traffic policy to the inbound direction of Device1.
- Author: Zou Chun
- Updated on: 2024-02-27
- Views: 7777
- Average rating:







