What Is CSRF?
Cross-Site Request Forgery (CSRF) is a type of attack that forces users to execute unintended actions on a web application that they are currently logged in to. On websites where they have been authenticated, users are lured into performing activities, such as sending emails/SMS messages, purchasing products, or transferring funds. The websites then execute the corresponding action.
How Does CSRF Work?
A CSRF attack involves the following process:
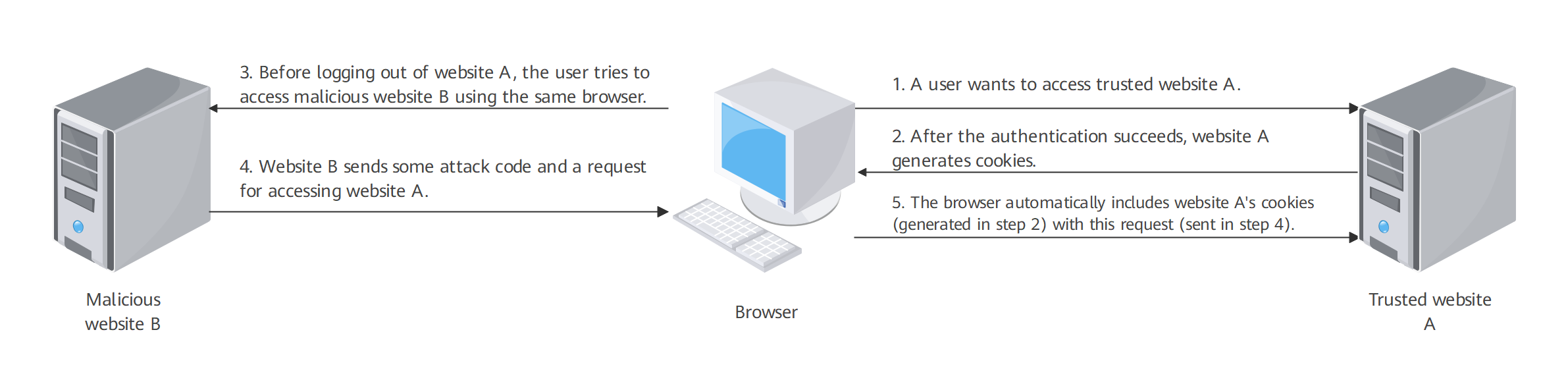
CSRF attack process
- A user wants to access trusted website A with CSRF vulnerabilities, and enters authentication information.
- After the authentication succeeds, website A generates cookies and sends them to the browser. The user then logs in successfully.
- Before logging out of website A, the user tries to access malicious website B using the same browser.
- After receiving the access request, website B sends some attack code and a request for accessing website A.
- Upon receiving the attack code, the browser will automatically include website A's cookies with this request. Without identifying that the request is initiated by the attacker from website B, website A processes the request with the user's permission based on the cookies. As a result, malicious code from website B is executed.
In conclusion, CSRF occurs when the attacker from a malicious website (website B) exploits the user's permissions to perform unauthorized operations on a target website (website A).
Defense Policies for CSRF
CSRF attacks are usually initiated from third-party websites, making it almost impossible for the target website to prevent them. However, measures should be taken to improve the security of websites vulnerable to CSRF attacks.
- Verifying the Referer field in the HTTP header
The Referer field in the HTTP header identifies the address of the web page from which the resource has been requested. When a sensitive data request is processed, the Referer field and the address of the web page from which the resource has been requested must be in the same domain name.
While this verification method is easy to implement and ensures the security of sensitive data requests, it has limitations. Its effectiveness depends entirely on whether the browser can send a correct Referer field compliant with the regulations specified by the HTTP protocol. More specifically, the correctness of the Referer field content cannot be guaranteed, and may be compromised by potential security vulnerabilities in the browser. A further risk is that the Referer field may be tampered with after the browser is attacked.
- Appending a token to the request address and verifying the token later
The essence of a CSRF attack is that the attacker tricks users into accessing a malicious site. To prevent such attacks, this defense policy requires the browser to follow a verification mechanism when the user wants to access sensitive data in the browser. This mechanism involves a token, which is typically a data item in a form that is not stored in cookies and cannot be forged by attackers. The server generates a pseudorandom number as the token and attaches it to the form. Each request submitted by the client through the form includes a token, which is then verified by the server for authenticity. During normal access, the client browser can correctly obtain and return the token. However, during CSRF attacks, as the token value cannot be obtained in advance, the token cannot be returned or obtained correctly. The request is then considered suspicious, and is rejected by the server.
- Using verification codes
CSRF attacks initiate network requests without the user's knowledge or consent. In the verification code mechanism, the user is required to interact with the application. The server uses the verification code to identify whether the request is intentionally sent by the user.
- Author: Zheng Haiyan
- Updated on: 2023-08-01
- Views: 897
- Average rating:






