What Is Keychain?
A key in a keychain is not an algorithm or a key string; rather, it is a set of encryption and authentication rules. A keychain centrally controls and flexibly manages a series of its own keys to provide dynamic security authentication services for applications. This document describes why keychain is required, its components, how it works, and typical applications.
Why Is Keychain Required?
Before an application establishes a session with the peer end using a routing protocol (for example, RIP, IS-IS, OSPF, or BGP), it needs to set up a connection at the transport layer.
To ensure the security of an application's session connections and exchanged data, MD5 can be used to authenticate packets; however, this has the following disadvantages:
- The MD5 algorithm is relatively basic and cannot meet high security requirements of networks.
- Keys must be frequently changed to ensure key security. The MD5 authentication algorithm and key are configured on applications and have static one-to-one mappings to applications. Therefore, you need to manually update the keys configured on the applications of the devices at both ends one by one.
To overcome these disadvantages, a keychain for application authentication is introduced:
- In each key of a keychain, an algorithm more secure than MD5 can be selected. In the future, even more secure algorithms will be available.
- Each key in a keychain has an independent algorithm, key string, and lifetime. Applications on devices at both ends use keychain authentication, and an application will match multiple keys. The authentication algorithms and key strings of multiple applications can be periodically updated on both ends based on the lifetimes of the keys.
- When keys in a keychain are dynamically updated, the transport-layer connections in use do not need to be disconnected and reconnected, maintaining the stability of session connections and service continuity.
What Are the Components of a Keychain?
A keychain is a set of encryption rules, called keys. Each key has an algorithm, a key string, and a lifetime. The algorithm and key string are used to encrypt and decrypt packets. The lifetime indicates the period during which packets are sent and received using the algorithm and key string.
- Supported algorithms: MD5, SHA-1, HMAC-MD5, HMAC-SHA1-12, HMAC-SHA1-20, HMAC-SHA-256, SHA-256, SM3, HMAC-SHA-384, and HMAC-SHA-512.
- Key string: a character string used for encryption. The same cleartext can be encrypted using different key strings to obtain different ciphertexts. The same ciphertext can be obtained only when the same key string is used for encryption.
- Lifetime: indicates the period of time during which a key is valid. If the lifetime of a key expires, the key is replaced by another active key.
How Does Keychain Work?
The keychain can be applied to non-TCP applications and TCP applications based on processing procedures.
Keychain Fundamentals (for Non-TCP Applications)
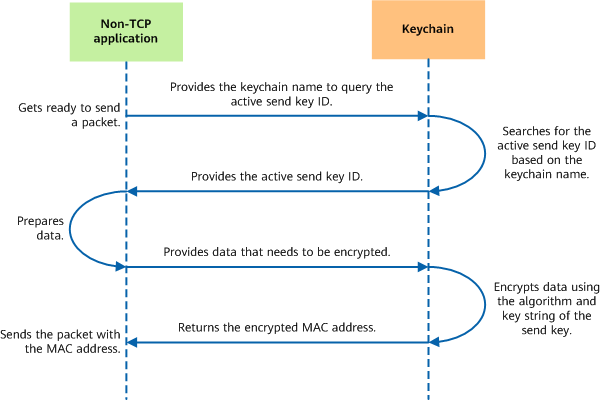
A keychain itself manages just the encryption and authentication keys, and only takes effect when used in applications.
An application needs to have a keychain bound before using keychain authentication. For example, if an application has KeychainA bound, the application can use the keys in KeychainA for encryption and decryption.
- Encryption process
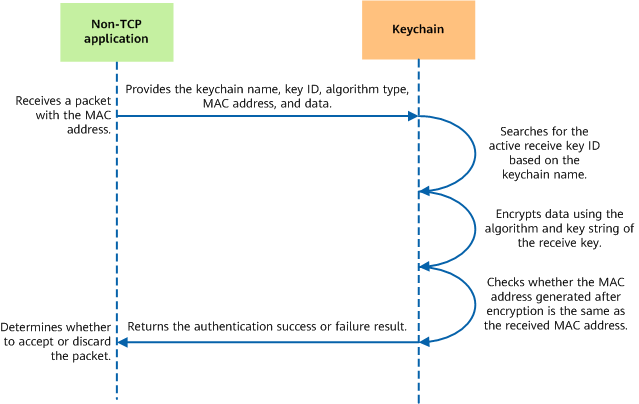
Encryption process for a non-TCP application using keychain authentication - Decryption process
Decryption process for a non-TCP application using keychain authentication
Keychain Fundamentals (for TCP Applications)
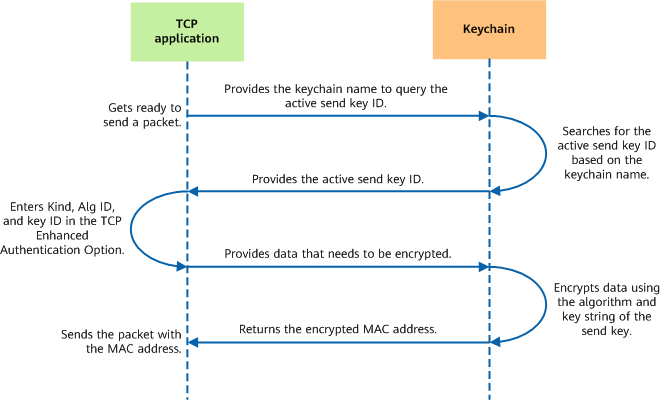
The fundamentals of keychain authentication for TCP applications are similar to those for non-TCP applications. The only difference is that the TCP Enhanced Authentication Option is added for TCP applications.
- TCP Enhanced Authentication Option
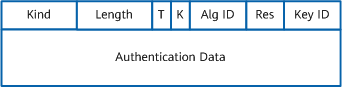
The following figure depicts the format of the TCP Enhanced Authentication Option. The TCP packet header carries this option to provide authentication protection specifically for TCP connections.
Format of the TCP Enhanced Authentication Option- Kind: 8 bits, identifies the TCP Enhanced Authentication Option. This value is assigned by IANA.
- Length: 8 bits, specifies the length of the TCP Enhanced Authentication Option, in octets.
- T: 1 bit, specifies whether the TCP Enhanced Authentication Option is included in the TCP header for the purpose of TCP enhanced authentication calculation. A value of 0 indicates that the TCP Enhanced Authentication Option is included. The default value is 0.
- K: 1 bit, reserved for future enhancement. The current value is 0.
- Alg ID: 6 bits, identifies the TCP enhanced authentication algorithm.
- Res: 2 bits, reserved for future use. The current value is 0.
- Key ID: 6 bits, identifies the key for keychain authentication.
- Authentication Data: The length is variable. It contains at least the result of TCP enhanced authentication calculation.
IANA does not define the values of the Kind and Alg ID fields in a unified manner. This results in different vendors using different values. To enable devices of different vendors to communicate, the keychain supports configuration of the TCP Kind and TCP Alg ID fields.
- Encryption process
Encryption process for a TCP application using keychain authentication - Decryption process
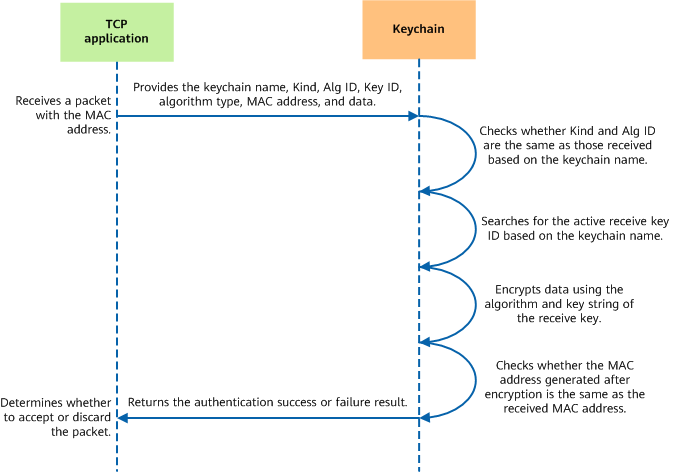
Decryption process for a TCP application using keychain authentication
Typical Applications of Keychain
Packets of routing protocols, such as RIP, IS-IS, OSPF, and BGP, must be encrypted to ensure network integrity. Keychain improves the security of these protocol packets by dynamically changing the algorithm and key string. The following uses the application of keychain to IS-IS as an example.
IS-IS is a commonly used routing protocol, and as such requires a high level of security. One way to ensure this is to configure a fixed algorithm and key string to authenticate IS-IS packets. However, fixed authentication algorithms and key strings are easy to crack. To enhance IS-IS security, you can use keychain to authenticate IS-IS packets.
For the devices in the following figure, you need to establish a keychain on each device, configure domain and area authentication in the IS-IS process, and configure interface authentication on interfaces so that all devices can communicate with each other using IS-IS.
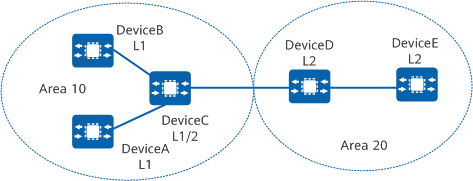
IS-IS using keychain for authentication
- Author: Meng Xianhai
- Updated on: 2024-02-27
- Views: 2876
- Average rating: