What Is Deception Technology?
Deception technology lures the attackers into attacking virtual networks or assets, thus protecting the real assets of enterprises effectively. Different from traditional techniques focusing on preventing attacks or fixing vulnerabilities, deception technology lures attackers into interacting with fake information (as a bait) and keeps them away from the real assets, thereby consuming the attackers' resources. During the interaction between the attacker and the bait, the attacker's behavior and data is collected. After the detection and in-depth analysis, corresponding defense measures are formulated to prevent threat activities, thereby protecting the security of real assets.
Why Is Deception Technology Important?
Traditional defense techniques are mainly used to detect and defend against attacks. As network attacks become increasingly sophisticated and powerful, more proactive and effective defense methods are required. Deception technology is a unique and highly effective tactic which is widely used to detect, defend, and analyze network threats. It enables defenders to deeply understand the attackers' behavior, methods, and targets and construct effective policies to defend against attacks.
- Reduce false positives through proactive defense
The deception technology provides advanced threat detection. The deception device seems an attractive attack target. Once an attacker attempts to access or interact with the device, an alert is triggered immediately. Compared with other traditional defense techniques, deception technology can reduce false positives because alerts are generated only when attackers proactively interact with specified deception targets.
- Collect attacker information and analyze network threats
The deception technology provides important information for network threat analysis. By observing how attackers interact with deception targets, the system records and monitors key information such as attack behavior, tools, and policies of attackers. This helps defenders understand common attack vectors and new threats for better network protection.
- Hide real asset information through effective defense
The deception technology provides an effective defense policy. By luring attackers away from real network resources and into attacking fake network assets, deception technology can be used as defense measures to prevent real assets from key system damage and data corruption. In addition, the deception technology uses the attacker's behavior and strategy to trap attackers by consuming their time and resources. This lures attackers into believing that they are attacking the real assets. Therefore, the defense system has enough time to detect and prevent attacks on the real assets.
- Optimize security investment and reduce defense costs
The deception technology helps enterprises optimize their security investments. With deception methods, enterprises can identify and defend against real threats more effectively. In this way, there is no need to deploy defense for all potential threats, saving costs and resources.
What Are the Features of Deception Technology?
The deception technology provides low deployment, maintenance costs, and reliable defense effect.
- Easy to deploy: The deception technology can be deployed anywhere on a network, for example, at the edge of the network, at the core network, or in a specific place where threats frequently occur. Virtual resources, such as network services, applications, and data, are simulated to attract attackers and lure them to preset traps.
- Easy to expand: The deception technology is easy to expand, which requires relatively less costs. The bait server can be reused to generate fake data. In addition, current deception technology contains functions such as intelligent learning, so that the virtual environment can automatically adapt to and imitate the actually changing network environment to better lure and confuse attackers.
- Effective to network attacks: Traditional passive deception techniques are effective to specific attacks, but need to be re-deployed to defend against new attacks. However, the proactive deception technology has replaced the traditional passive defense mindset, for example, releasing fake information to lure attackers, and collecting all attack information for analysis. In this way, the deception technology can prevent all network attacks.
Common Types of Deception Technology?
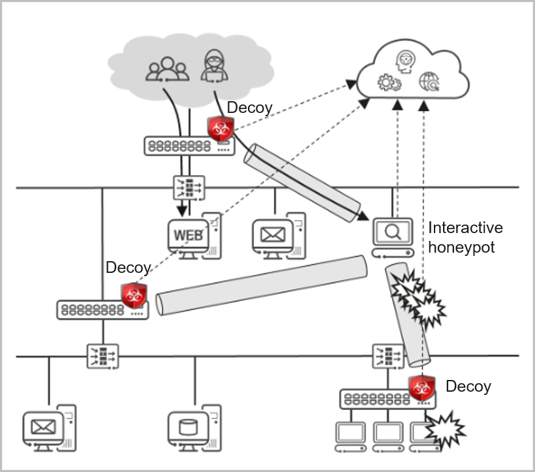
The deception system is generally composed of a honeypot and decoys. Decoys can be widely deployed on security gateways, border routers, and intranet switches to lure network-wide attacks and redirect attack traffic to the honeypot.
Honeypot is the precursor to today's deception technology in the network security. With the development of technology, the deception technology has been transformed from the initial single-point deception to the establishment of defense concept and defense system. The selection and implementation of deception technology depends on many factors, including the organization's network environment, current security policies, budgets, regulatory requirements, and effectiveness requirements of deception methods. For large-scale network, mixed deception policies may be required, including honeypot, honeytoken, and honeynet. In some environments with high security requirements, simplified policies may be adopted, for example, honeytoken. Common deception technology includes:
- Honeypot
Honeypot is disguised as real network devices or services to lure and monitor attackers. As the attackers' target, the honeypot attracts their attention and collects data about attack behavior and strategies. A honeypot is a virtual system that runs in an isolated environment. Users and services of real assets do not interact with honeypots. Therefore, any activity against honeypots can be considered as malicious attacks.
- Honeytoken
Honeytoken is not a host node, but a piece of tagged data which is implanted into the system to lure attackers. The honeytokens seem valuable to attackers but have no actual functionality. Alerts are triggered when attackers try to use these honeytokens. For example, once a special password is used, it indicates that someone is trying to attack the system because it is impossible for a real user to use the password.
- Honeynet
A honeynet is a virtual network consisting of several honeypots. It simulates a large-scale application network containing devices such as servers, workstations, and switches. In this virtual environment, attackers are lured into performing a variety of and more sophisticated attacks. In addition, a large amount of attacker information, such as attacker tools, behavior, and policies, is obtained to provide data assurance for threat analysis.
- Decoy
Decoys attract the attackers' attention by imitating a real service or device, which can be virtual network services, sealed data files, any other resources that seem valuable to attackers, or accounts that can be used to log in to the system and attempt to obtain permissions.
Solutions Related to Huawei Deception Technology
Huawei products and solutions help you cope with network attacks. The deception system detects scanning behavior on the network and lures suspicious traffic to decoys for in-depth interactive detection, protecting the existing service network.
- HiSec Security Solution
Huawei provides professional security solutions for various scenarios, such as cloud data centers, campus networks, branch networks, APT defense, and big data security. Huawei's network deception technology responds to scanning requests for nonexistent IP addresses and unopened ports to lure attackers into attacking a fake target (decoy). Then, the decoy interacts with the attackers to obtain their attack behavior, extract attack tools, and analyze suspicious traffic by means of traffic diversion. Therefore, defense policies are created to block the spread of attack.
- HiSecEngine USG6000E Series AI Firewalls
USG6000E firewalls provide the network deception function to detect scanning behavior and lure suspicious traffic to decoys for in-depth interactive detection. The deception technology can detect threats in a timely manner. It lures a hacker into accessing decoys for deep interaction by responding to the scanning requests of a hacker for offline IP addresses and unopened ports, protecting the service network.
- HiSec Insight Advanced Threat Analytics System
HiSec Insight uses big data platform technologies and intelligent detection algorithms to perform multi-dimensional correlation analysis on massive data. Decoys record various application-layer attack methods and report logs to the HiSec Insight collector. Then HiSec Insight performs in-depth analysis, determines attack behavior, and generates alerts or handling suggestions. In addition, HiSec Insight provides a comprehensive display of the network security situation.
- Author: Fang Min
- Updated on: 2024-01-10
- Views: 429
- Average rating: