What Is SSO?
Single Sign-On (SSO) is an authentication mechanism that allows users to access multiple applications or systems with just one login, improving user experience and work efficiency. Typically, SSO leverages an identity provider (IdP) to manage user authentication information and securely transfer it to applications or systems that require authentication. With SSO, users can access protected resources without needing to re-enter their credentials, streamlining the authentication process.
SSO Implementation
The following figure illustrates how SSO is implemented.
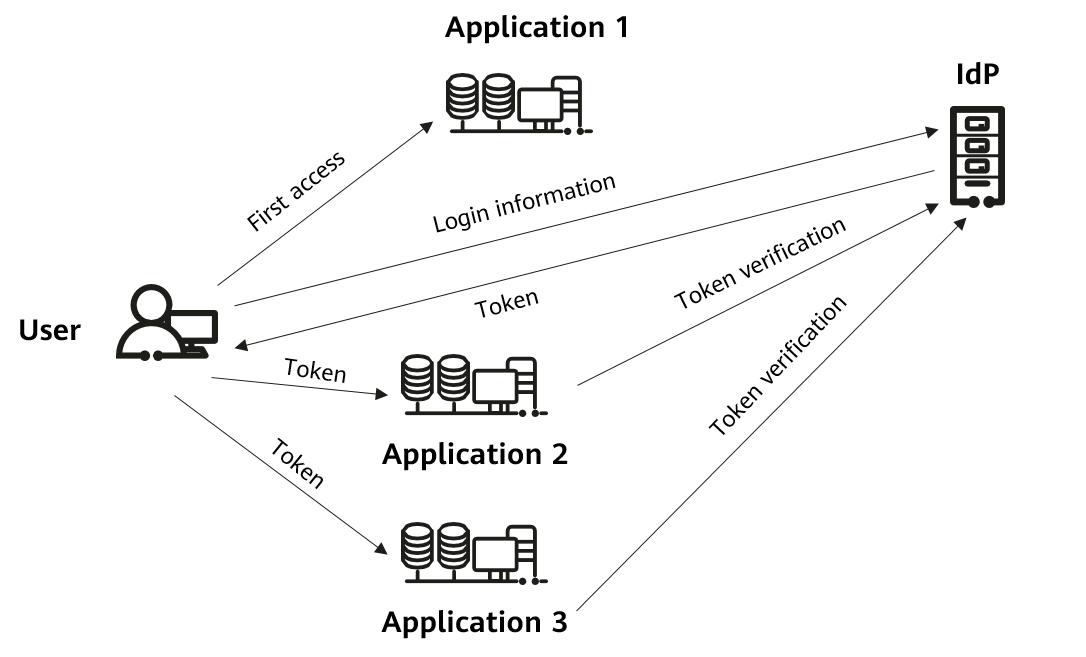
- A user accesses an application or system that requires authentication for the first time.
- The application or system redirects the user to the IdP. The user is authenticated on the IdP, typically by entering the username and password.
- The IdP issues a token to the user, which contains user authentication information.
- The user is redirected back to the original application or system and passes the token to it. The application or system then uses the token to verify the user identity and grant access to the user.
- If the user accesses another application or system that requires authentication, the application or system uses the same token to authenticate the user on the IdP.
SSO implementation
Protocols and Technologies Used by SSO
SSO can be implemented through multiple authentication protocols and technologies.
- Security Assertion Markup Language (SAML): It is an XML-based standard for transferring authentication and authorization data between different security domains. It allows users to authenticate in one application and then use SAML tokens to access other applications.
- Open Authorization (OAuth): It is an authorization framework used to authorize third-party applications to access user resources. It allows users to log in to an application using their credentials and then access other applications using OAuth tokens.
- OpenID Connect (OIDC): It is an authentication protocol built on OAuth 2.0 and mainly used to implement social login of third-party applications. As a lightweight implementation, OIDC/OAuth is usually used in conjunction with SAML.
- Kerberos: It is a network authentication protocol used to securely verify user identities on a computer network. It allows users to log in to an application using their credentials and then access other applications using Kerberos tickets.
- Lightweight Directory Access Protocol (LDAP): It is a vendor-neutral application protocol used to access and maintain distributed directory information services. LDAP defines the directory for storing and updating user credentials and the process of authenticating users based on the directory. It enables users to log in to an application using their credentials and then use the LDAP directory to access other applications.
- Active Directory (AD): It is a directory service that runs on Microsoft Windows Server. It can be used to store and manage users, computers, and other resources in an organization.
Advantages and Disadvantages of SSO
- Improved user experience: With a single login to the system, users can access multiple applications or systems, eliminating the need for repetitive logins while improving overall user experience.
- Enhanced security: User authentication and authorization are centrally managed, mitigating the risk of using identical credentials across multiple applications or systems and minimizing the likelihood of password leaks.
- Better work efficiency: Authentication time for users across multiple applications or systems is reduced, improving work efficiency.
- Single point of failure (SPOF): If the SSO system is faulty, no application or system that depends on it can be used, potentially causing service interruptions.
- Security risks: If the SSO system is attacked or infiltrated by hackers, all applications and systems that rely on it become vulnerable to security threats.
- High implementation cost: The SSO system requires complex configuration and integration, requiring large amounts of time and resources. Therefore, the implementation cost is high.
In summary, SSO improves user experience, security, and work efficiency, but also has disadvantages such as SPOF, security risks, and high implementation costs. Therefore, before implementing SSO, you need to carefully evaluate its advantages and disadvantages and make decisions accordingly.
Applications of SSO
SSO enables users to access all related applications with just one login, resulting in improved user experience, reduced management costs, and enhanced security. As a result, SSO is widely adopted across various application scenarios.
- Internal applications: An enterprise typically has multiple internal applications, such as email and ERP. With SSO, employees can access all these applications after logging in to the system just once.
- Cross-organizational cooperation: In such scenarios, the applications and systems of different organizations may vary. SSO allows users to seamlessly switch between organizations.
- Cloud applications: With the increasing popularity of cloud computing, ever-growing numbers of applications are being deployed on the cloud. Among these, many enterprises use cloud-based applications, including Office 365. With SSO, users are able to access all cloud applications after logging in just once.
- Mobile applications: SSO allows a user to sign in once and access all mobile applications.
Huawei's HiSecEngine USG6000E and USG6000F series AI firewalls can function as authentication points or synchronize user authentication results from other authentication points to dynamically control network access rights based on users. After being authenticated by the SSO server, users can directly access network resources without being authenticated by the device.
- Author: Zhao Jie
- Updated on: 2023-09-04
- Views: 1130
- Average rating:






