What Is a Trojan Horse?
The term "Trojan horse" has its origins in the famous Trojan War from Greek mythology, where a Trojan Horse was a wooden horse said to have been used by the Greeks to enter the city of Troy in disguise and win the war. In computing, Trojan horses adopt a similar approach by masquerading as legitimate software that is downloaded onto the user's host. Once the software is installed, hackers can exploit the Trojan horse to gain control of the user's host and steal user information. Trojan horses are highly covert, often exhibiting no abnormal behavior on the infected computer, which makes them difficult to detect.
The difference between Trojan horses and computer viruses is that the latter is a kind of malicious code that can replicate itself, while the former does not replicate itself.
How Do Trojan Horses Attack?
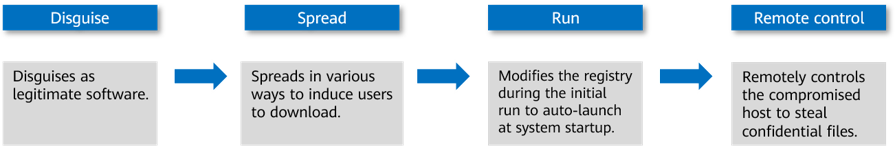
Trojan horses usually attack user computers in the following ways:
Attack process
- Disguise
Attackers disguise Trojan horses as legitimate software commonly by:
- Changing the icon: Attackers change the icon of Trojan horses to a common file icon. For example, the icon of a text, image, or HTML file.
- Changing the name: Attackers usually change the name of a Trojan horse to the name of a system file, because users are typically wary of deleting system files.
- Changing the file name extension: Generally, attackers change the file name extension of a Trojan horse from .exe (executable file) to that of a common file type.
- Binding files: Attackers often bundle Trojan horses with a file. For example, a Trojan horse is bundled with a damaged ZIP package (self-made).
- Spread
Attackers often spread Trojan horses through email attachments and website downloads. The specific tactics are as follows:
- Email phishing: Pretending to be a user's email contact or a reputable organization, an attacker sends an email with a Trojan attachment to the user. Once the user clicks the attachment, the Trojan horse is automatically downloaded and installed on the user's computer.
- Website phishing: An attacker uploads a Trojan horse to a phishing website, sets the website to automatically download the Trojan horse upon user access, and tricks users into accessing the website through social engineering techniques.
- Dangerous site implantation: Attackers may breach software download sites, bundle frequently downloaded software with Trojan horses, or hide Trojan horse download links in pop-up ads on the sites.
- Run
After being downloaded, the Trojan horse is automatically installed and run. During its initial run, it automatically modifies registry information and inserts itself into the startup configuration file or registry. For example, the Trojan horse adds its own path to a file such as system.ini or a registry startup item, so that it can be automatically loaded when the target host boots.
- Remote control
After the user's computer is infected, it is continuously monitored by the Trojan horse. Without the user knowing, the attacker can remotely control the user's computer by delivering commands, and in doing so complete the attack instructions. For example, the attacker may steal user information, launch DDoS attacks, or even use the user's computer as a stepping-stone to infect other devices on the same network.
Common Types of Trojan Horse
Remote Access Trojan
Modern Trojan horses commonly utilize remote control as a fundamental feature, allowing them to establish connections with user computers and remotely deliver commands to implement functions such as remote capture, file transfer, and screen capture.
Typical examples: Huigezi and Glacier Trojan.
Password-Stealing Trojan
This type of Trojan horse is designed to stealthily extract all hidden passwords, such as those for social media accounts and online games, and transmits the information without the victim's knowing.
Typical example: Wirenet.
Keylogger Trojan
Keylogger Trojan horses record every keystroke the user types and are automatically loaded during the operating system startup. They are classified into online and offline Trojan horse programs, which record the user's keystroke in online and offline states respectively. Such Trojan horses also can send recorded information to the controller through emails.
Typical examples: Magic Lantern and Trojan.Spy.Win32.KeyLogger.eom.
DDoS Trojan
Attackers use Trojan horses to control infected hosts, called zombies. A large number of these zombies are then used to launch DDoS attacks. For example, an attacker launches a DDoS attack on a website, consuming a large amount of website server resources and thereby preventing the website from serving users.
Typical examples: Satan DDoS and TROJ_ELKNOT.A.
Banking Trojan
Banking Trojan horses mainly target online transaction systems of banks. They aim to steal users' bank account information, including bank accounts and passwords, greatly harming personal property security.
Typical examples: Tiny Banker Trojan and Xenomorph.
Characteristics of Trojan Horse
The Trojan horse and computer virus differ significantly in that the latter has the ability to self-replicate and launch attacks on their own, while the former does not. Trojan horses have the following characteristics:
- Covertness
Covertness is the most important characteristic of Trojan horses, as it allows them to evade detection on users' computers for prolonged periods. Although the Trojan horse automatically runs when the system is started, it hides itself in a legitimate program. When the Trojan horse is in the running state, it does not generate an icon in the taskbar, and as such cannot be easily detected in the task manager. This makes it difficult for users and some security software to detect Trojan horses.
- Deceptiveness
Deceptiveness refers to how Trojan horses typically deceive users and evade the detection of security software by disguising themselves as common software. There are many ways in which Trojan horses achieve this, for example, changing the icon of a Trojan horse program or changing the file name to disguise itself as a system service.
- Harm
After a Trojan horse is implanted on a target host, the attacker gains remote control over the client to perform a series of illegal behaviors that can cause serious consequences, such as stealing confidential files, manipulating system operations, and infecting other hosts by using the compromised host as a stepping-stone.
How Do I Defend Against Trojan Horses?
It is crucial to prioritize prevention measures to effectively defend against Trojan horses. This involves proactively intercepting attacks before they can infiltrate devices and cause significant damage. Users can try to improve network security awareness and enhance defense measures on computer systems. The following are recommended measures:
- Install authorized operating systems and applications. Do not download applications from unofficial websites.
- Use dedicated Trojan horse scanning software and regularly upgrade the software.
- Do not open emails from unknown sources. Even emails from familiar people must be treated with caution, because Trojan horses may have infected their computers to spread.
- Enhance the security awareness of personal account information. For example, passwords should have a combination of characters, uppercase letters, lowercase letters, and digits.
- Back up important data and files regularly. In that way, even if Trojan horses modify or delete the data files, they can be restored, thereby reducing loss.
- Do not click pop-up ads on websites. Generally, such ads are enticing, influencing users to click. As such, it is important to improve your ability to identify such ads.
- Use firewalls to protect personal computers.
How Does Huawei Help Defend Against Trojan Horses?
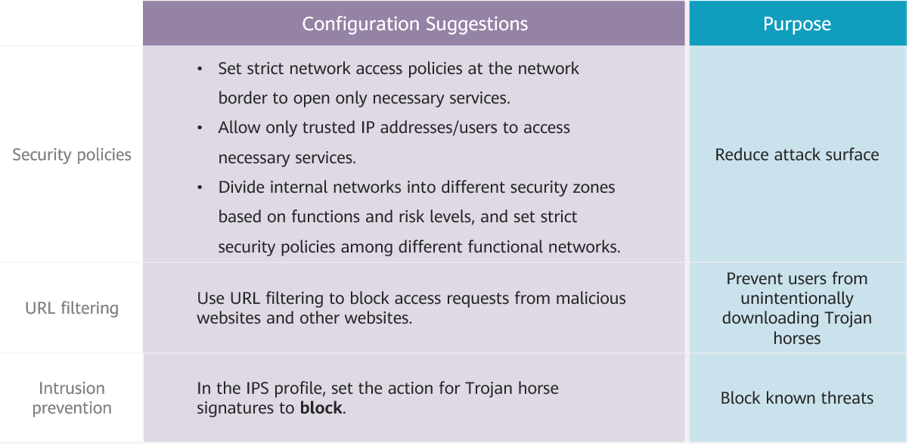
Trojan horses are covert, often disguised as legitimate applications. Huawei HisecEngine USG6000E and USG6000F series AI firewalls build a multi-layered security defense to safeguard against Trojan horses. This is achieved through the configuration of robust security policies, effective URL filtering, and comprehensive intrusion prevention measures.
- Author: Fang Wei
- Updated on: 2023-09-04
- Views: 1970
- Average rating: