What Is APN6?
Application-aware IPv6 Networking (APN6) conveys APN attributes (including APN IDs and parameters for identifying applications and for identifying network performance requirements, respectively) to a network by leveraging the extension header space in IPv6 packets, enabling service providers to provide fine-grained network services and achieve precise network operations and maintenance (O&M). Paired with other technologies, such as Segment Routing over IPv6 (SRv6), network slicing, and Deterministic Networking (DetNet), APN6 enables a network to provide increasingly diversified network services in order to meet the differentiated requirements of applications.
Why Do We Need APN6?
Limitations of Traditional Technologies That Enable a Network to Perceive Applications
The advent of the 5G and cloud era has given rise to the continuous emergence of various applications, for example, enhanced Mobile Broadband (eMBB) and massive Machine-Type Communications (mMTC) applications. The applications have diversified network requirements. In adopting the end-to-end (E2E) layered design principle and concept of the Internet, it became clear that applications and networks have long been decoupled. However, as applications and networks continue to develop, the decoupling is no longer feasible — networks have increasingly strong requirements for being aware of applications. Such new requirements inspired people to consider whether networks and applications should continue to be decoupled and whether there are new ways for networks to be aware of applications.
Traditional technologies that enable a network to perceive applications integrate an identification technology and a marking technology, as detailed in the following table. An identification technology is used to identify the application to which a packet belongs, and a marking technology is used to mark the service requirements of the application. Used together, they help carriers provide differentiated services for different applications. However, such technologies currently available have certain limitations.
Category |
Technology |
Principle |
Advantage |
Limitation |
|---|---|---|---|---|
Application identification technology |
5-tuple-based |
This application identification technology is based on traffic behaviors. It provides parameters such as the network layer information, transport layer information, service flow duration, and byte length distribution information, based on which the network can collect and analyze traffic statistics. |
Applications can be perceived in a general manner. |
|
Deep flow inspection (DPI) |
This technology enables a network to determine the application to which a packet belongs based on packet header information and the characteristics of an application protocol. |
Applications can be accurately identified based on packet characteristics. |
|
|
Application marking technology |
QoS Precedence field-based |
This technology enables a network to classify traffic based on the QoS Precedence field in packets. |
Simple differentiated services can be provided. |
|
Overcoming the limitations of traditional application perceiving technologies has become a concern in the industry. To address this concern, APN6 was proposed. APN6 uses the extension header space in IPv6 packets to carry APN IDs and APN parameters, enabling the entire network to be aware of applications through received packets.
What Are the Core Values of APN6?
APN6 enables a network to effectively perceive key applications/users and their network performance requirements. By working with technologies such as SRv6, network slicing, DetNet, service function chain (SFC), software-defined networking in a wide area network (SD-WAN), and In-situ Flow Information Telemetry (IFIT), APN6 substantially enriches cloud-network services, expands the value-added space of cloud-network business, and enables fine-grained cloud-network operations for service providers. The technical values of APN6 include:
- Refined application visualization
Network visualization is required so that traffic passing through a network can be intuitively and comprehensively learned. Network visualization — comparable to magnetic resonance imaging for people — is used to trace network performance and to analyze and locate network faults. The network can use APN6, AI, and big data analytics to profile traffic characteristics of key applications or users and present traffic paths, characteristics, and change patterns and trends, implementing visualized monitoring of application traffic.
- Refined application traffic steering
APN IDs are used to identify key applications or users precisely, so that traffic can be steered into corresponding SRv6 paths, network slices, DetNet paths, or SFCs. This makes it possible to achieve application traffic division and flexible path selection.
- Refined application measurement
IFIT inserts an IFIT header into a service packet to measure the actual forwarding path of the service flow. In this way, IFIT visually presents network performance and service quality, making network O&M more real-time and effective. After the network identifies key applications or users based on APN IDs, it can use IFIT (hop-by-hop or E2E) to monitor its performance for key services in real time.
- Refined application optimization
APN6 perceives applications while IFIT perceives quality and experience. Together, they perceive the entire application experience. The network can use APN IDs to precisely identify key applications or users, and use IFIT to detect key services with deteriorated performance. In this way, the network can perform fine-grained optimization for the key services based on APN IDs.
How Does APN6 Work?
APN6 conveys APN attributes to a network through the extension header space in IPv6 packets, enabling the network to not only differentiate traffic of different types or groups of applications, but also implement fine-grained resource scheduling. APN IDs are used to differentiate application flows and users. For example, APN IDs of different game accounts are different.
As shown in the following figure, APN6 extends the IPv6 data plane and adds APN attributes in the IPv6 Destination Options Header (DOH).

APN attribute position
What APN attributes can be carried? How are APN attributes differentiated? As shown in the following figure, an APN6 packet header contains an APN ID, consisting of the APP-Group-ID, USER-GROUP-ID, and Reserved fields. These fields are used to differentiate applications and users. APN-Para-Type specifies the type of requirement that an application has. Currently, the requirements for bandwidth, delay, jitter, and packet loss rate are supported.
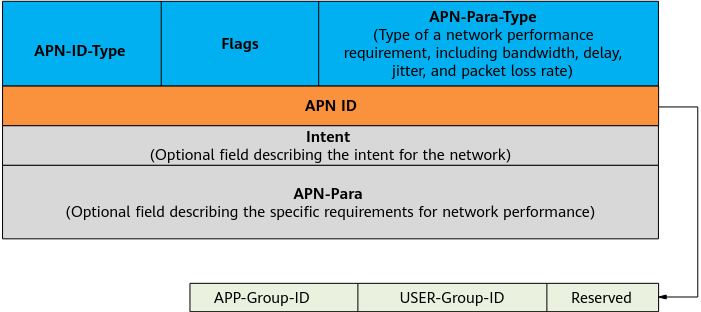
Structure of an APN6 packet header
Simply put, APN6 can be used to identify the application to which specific traffic belongs and identify the network requirements of the application's traffic, enabling the network to provide fine-grained services for the application.
Before APN6 is applied, a network can learn only brief information about a packet — such as information on how to route the packet — but cannot perceive the information inside the packet. To better understand APN6, let's compare an APN6-capable network to a logistics network, and compare application packets to goods. After APN6 is applied, it is like attaching more labels goods cartons so that couriers can better learn the attributes of goods and handle them more accurately. For example, couriers can recognize fragile goods and urgent goods, allowing them to learn which ones need to be handed more gently and which ones need to be delivered more preferentially.
How Is APN6 Implemented?
The following describes how the APN attributes added by APN6 are used on a network.
The following figure shows the APN6 network architecture, which mainly consists of application terminal/cloud devices, network edge devices, network policy enforcement devices (headend, midpoint, and endpoint), and controllers.
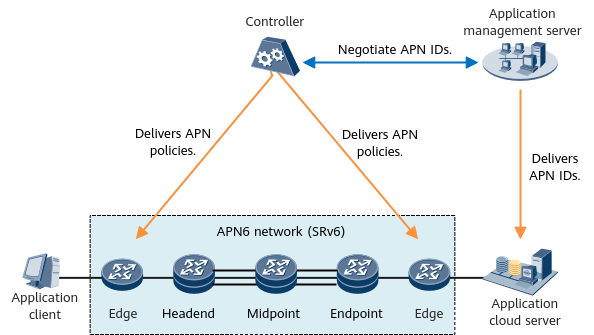
APN6 network architecture
Currently, there are two APN6 implementation solutions: application-side solution and network-side solution.
- Application-side solution
In this type of solution, APN IDs are generated and encapsulated into packets by application terminal/cloud devices. Application terminal/cloud devices encapsulate APN attributes into extension headers of IPv6 data packets. In APN attributes, APN IDs are mandatory, but requirement information is optional. The nodes (including the headend) in an APN6 domain can then provide fine-grained application-aware network services based on the APN attributes carried in the packets. For example, the nodes can steer the packets of an application to the matched SRv6 Policy and trigger real-time IFIT-based performance measurement for the application. For the application-side solution to work, both the application and its terminal operating system (OS) must be able to encapsulate APN attributes into data packets. As such, this solution is suitable when the network and application are owned and managed by the same organization.
- Network-side solution
In this type of solution, APN IDs are generated and encapsulated in packets by network edge devices. The headend and edge device on the network perceive applications, and then add application tags to user traffic. A network edge device (such as a CPE), rather than an application terminal/cloud device, parses out application-aware information carried in packets (5-tuple information, Layer 2 interface information, or both), and encapsulates APN IDs according to a predefined policy. This allows the APN6 network to provide fine-grained services based on the APN attributes carried in the packets.
The following table compares the two solutions. The network-side solution does not require ecosystem support from the application side and is easy to deploy on carrier and industry networks. As such, the network-side solution is the mainstream of APN6. The application-side solution requires ecosystem support, but it has great development potential. This means it is also the future of APN6.
Solution |
Similarity |
Scope |
APN ID Allocation |
Security |
|---|---|---|---|---|
Application-side solution |
The network side implements refined network services based on APN attributes. |
Internet |
Global |
The network does not trust the information. |
Network-side solution |
Restricted domain |
Within a restricted domain |
User access is controlled. |
APN6 Application in a KEA Video Conference Scenario
Digitalization increases the requirements for video conferences between provincial and municipal governments. Due to the important role they play in government work, video conferences require not only good connectivity but also high quality. Take the key event assurance (KEA) video conference of the e-Government extranet as an example. The multipoint control unit (MCU) for videos marks services with APN IDs. The e-Government network can then identify service flows based on APN IDs and steer key service flows to dedicated video slices.
After APN6 is deployed in the scenario shown in the following figure, the network can automatically reserve resources based on APN IDs, implementing automatic resource planning before a conference is conducted. During the conference, the network uses the conference ID carried in APN6 packet headers to identify high-priority service flows and steer them into an SLA-compliant SRv6 path, guaranteeing low delay and high reliability for the important video conference. After the conference, backtracking the entire conference process is supported. APN6 breaks the boundary between videos and networks, implements system-level resource scheduling, and reduces the planning period. It also enables the network to detect faults and facilitates post-conference quality analysis. Such functions are difficult, or even impossible, to implement before the introduction of APN6 due to factors such as a lack of orchestration.
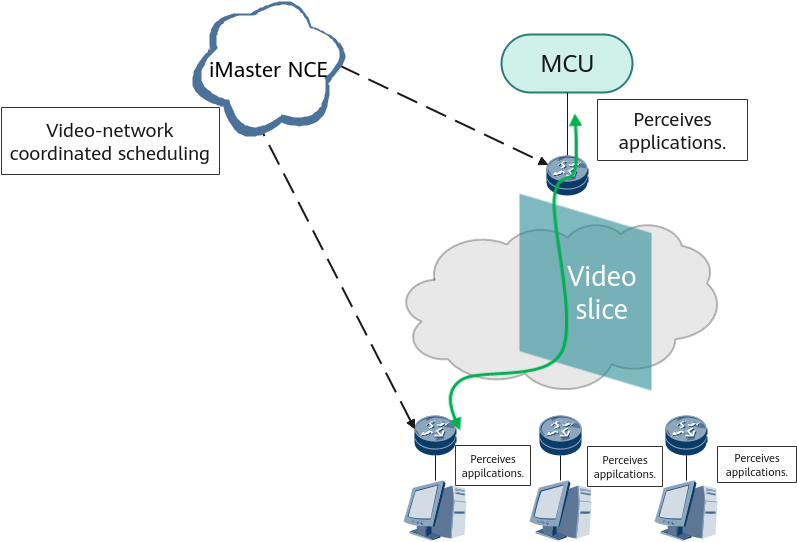
APN6 application in a KEA video conference scenario
APN6 Application in a Financial Application Acceleration Scenario
Banking services come in a variety of flavors. Large financial institutions, such as banks, spend a large amount of money on leasing bandwidth every year. Efficiently utilizing bandwidth and ensuring the stability of key services have become major concerns for them. APN6 addresses these concerns by identifying applications at the ingress of the financial cloud network in order to guarantee bandwidth resources for key services and reduce the bandwidth consumption by non-key services. This way, APN6 can help guarantee the network quality for key services.
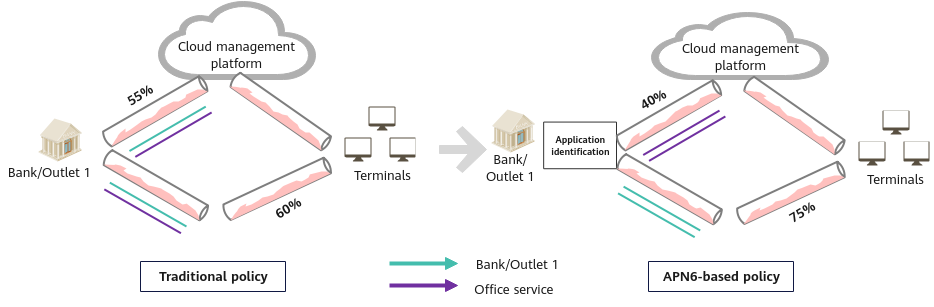
APN6 application in a financial application acceleration scenario
APN6 not only improves network stability in terms of scheduling optimization, but also improves file management efficiency. The latter is because APN6 can identify old ACL files, helping maintenance personnel quickly determine whether to delete old ones that are no longer needed. Many zombie policies may exist on a network that has been running for a long time. It is difficult to determine whether such a policy can be used or deleted, resulting in many redundant configurations and impeding optimization. For example, when a large financial company moves from one building to another before a comprehensive plan is formulated for the move, original ACLs still exist on the network, even if the IP addresses and port numbers are changed. Because it is difficult to determine the usage of such ACLs, maintenance personnel will not delete them in most cases. As a result, a large number of unneeded ACLs exist on the network, wasting memory resources. APN6 addresses this issue by matching information such as destination addresses and port numbers based on the assurance policy of each service, helping maintenance personnel identify unmatched ACL files. They can then delete such files in a timely manner, thereby preventing excessive expansion of policies and configurations and accelerating bandwidth. Because APN6 can identify services, the network can identify the SLA requirements of different services based on APN IDs, thereby providing required assurance for services. As a result, there is no need to configure a large number of ACLs, simplifying O&M and reducing maintenance costs.
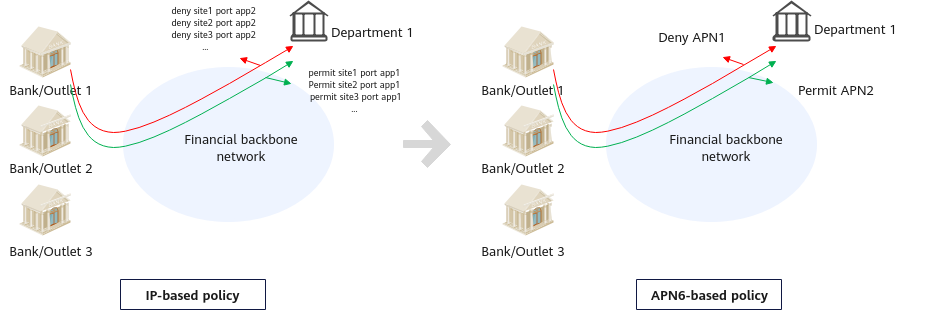
APN6 application in a financial application acceleration scenario
- Author: Guo Yuhan
- Updated on: 2023-05-23
- Views: 3573
- Average rating:






