What Is SSL?
Secure Sockets Layer (SSL) is a cryptographic protocol that protects communications over insecure networks, such as the Internet. SSL establishes a session between a client and a server through a handshake to authenticate the identities of the communicating parties and negotiate keys and cipher suites. This prevents the interception of communication between the client and server and secures data transmission on the network. SSL certificates are used to authenticate and establish a secure connection between a client and a server.
Why Is SSL Needed?
Transmitting sensitive data (such as bank data, transaction information, and passwords) in non-ciphertext over the network is very insecure. SSL was developed especially for the secure transfer of data via websites on the Internet. HTTP does not provide a security mechanism, but rather transmits data in cleartext and without authenticating the identities of communicating parties. As a result, transmitted data is vulnerable to tampering, posing security risks. Against this backdrop, Netscape developed SSL, which provides data encryption, identity authentication, and message integrity verification mechanisms, improving data transmission security. Specifically, SSL provides secure connections for HTTP to prevent man-in-the-middle (MITM) attacks and network interception, significantly improving the security of data sent over the Internet.
HTTPS uses SSL over HTTP to secure communications. Currently, mainstream websites such as Facebook, Google, and Taobao use SSL-encrypted communications to improve data security. SSL is also widely used in e-commerce and e-government activities, such as banking and financial services, online payment, online contract signing, and government platforms.
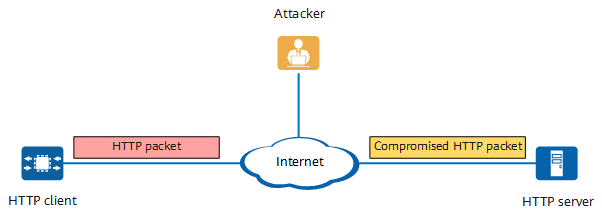
HTTP packet transmission
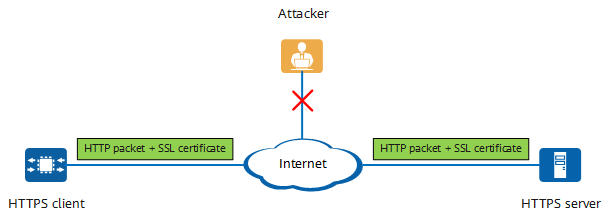
HTTPS packet transmission
In addition, functioning between the application and transport layers, SSL can secure data transmission for any application layer protocol based on TCP connections. SSL can be configured for the dynamic routing protocol BGP as well as communications protocols OpenFlow and gRPC. This ensures that a secure SSL connection can be established between the server and client to improve device security.
What Is an SSL Certificate?
The security mechanisms of the SSL protocol can be implemented only when certificates are used together. To ensure security, SSL uses certificates to authenticate both ends of a connection and negotiate encrypted communication channels. Certificates used during SSL-based communications are called SSL certificates.
An SSL certificate is an SSL-compliant digital certificate. It contains a public key and information about the identity of its owner (called the subject), and is issued by a trusted digital certificate authority (CA). SSL certificates use the SSL protocol for communication and provide server identity authentication and data transmission encryption functions. They are used to ensure the security of communication between services in the device and between the device and external devices, prevent communication data from being tampered with during transmission, and improve system security. A digital certificate, which is similar to an electronic copy of a passport or an ID card, is typically used for identity verification on the network.
CA
A CA is an authoritative and impartial third-party organization responsible for issuing, authenticating, and managing certificates. It validates the identities of digital certificate holders, issues digital certificates (by signing digital certificates to prevent certificates from being forged or tampered with), and manages certificates and cryptographic keys. CAs are classified into the root CA and subordinate CAs. The globally trusted CA is called a root CA, and can authorize other CAs as subordinate CAs.
The role of a CA is similar to that of a notary organization. Certificate management is the primary function of CAs, and includes issuing, revoking, querying, and archiving certificates, as well as publishing Certificate Revocation Lists (CRLs).
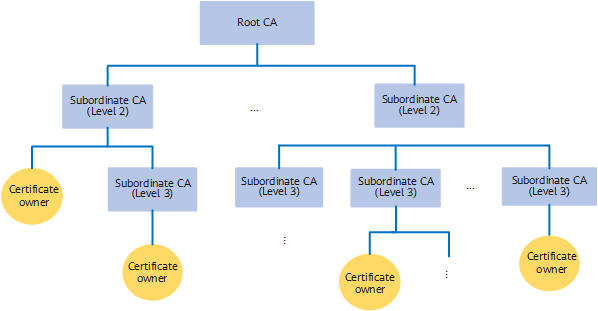
Hierarchical CA
- The root CA is the first CA (trustpoint) in the PKI system. The root CA can issue certificates to other CAs, computers, users, and services. (Most root CAs do not directly issue certificates to users.) In most certificate-based applications, the root CA can be traced through the certificate chain. Because there is no upper-level organization for digital signing, the root certificate is generally self-signed.
- A subordinate CA can only obtain a certificate from its upper-level CA. The upper-level CA can be the root CA or another subordinate CA authorized by the root CA to issue certificates. The upper-level CA issues and manages certificates of lower-level CAs.
How Do I Obtain an SSL Certificate?
You need to purchase and apply for an SSL certificate. To obtain such a certificate, you can place an order online from the official website of a CA. Currently, mainstream trusted SSL certificate CAs include DigiCert, Symantec, GeoTrust, Comodo, GlobalSign, Thawte, RapidSSL, AlphaSSL, and Sectigo. Most of these CAs are outside China. In China, you can place an order on the website of a certificate agent, such as Huawei Cloud, Alibaba Cloud, Tencent Cloud, and TrustAsia.
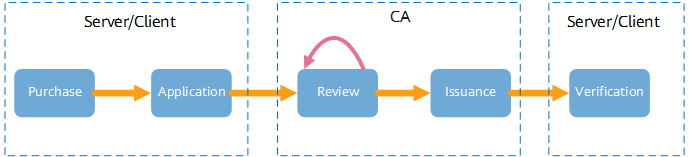
SSL certificate purchase process
How Does SSL Work?
SSL provides identification and authentication for communicating parties to ensure data integrity and confidentiality. By performing a handshake, SSL enables the server and the client to communicate in several successive rounds to implement message exchange and identity authentication, and determine the cryptographic algorithm and session key to be used in the subsequent communication process. Then, in the subsequent communication process, the session key is used for encryption and decryption, and only the ciphertext is transmitted in subsequent information transmission.
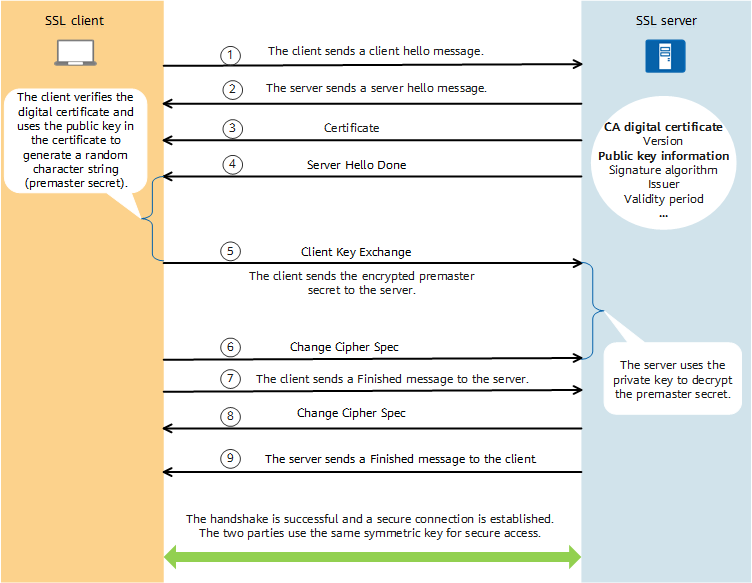
SSL handshake process
The SSL handshake process consists of the following steps:
- The SSL client sends a message to the SSL server to start a handshake. The message carries information such as the SSL version the client supports, cipher suites supported, and a string of random bytes known as the "client random".
- The SSL server responds to the SSL client with information such as the selected version, cipher suites, and a string of random bytes known as the "server random".
- The SSL server sends a digital certificate carrying its public key to the SSL client so that the client can authenticate the server.
- The server sends a Server Hello Done message, which means the SSL version and cipher suite negotiation has finished, and key information exchange can begin.
- The SSL client verifies the authenticity of the SSL server certificate, encrypts the randomly generated key using the public key in the certificate, and sends the encrypted key to the SSL server.
The randomly generated key (premaster secret) cannot be directly used to encrypt data or compute MACs. It is used to compute the symmetric key for encryption and decryption and MACs for data integrity verification. The SSL client and server use the client random, server random, and premaster secret to generate the same master secret using the same algorithm. Then, based on the master secret, they use a symmetric key algorithm to compute the symmetric key and MACs.
- The SSL client notifies the SSL server that subsequent packets will be encrypted and MACs will be computed using the negotiated key (generated based on the master secret) and cipher suite.
- The client instructs the server to verify that the SSL negotiation has been successful.
- The SSL server notifies the SSL client that subsequent packets will be encrypted and MACs will be computed using the negotiated key (generated based on the master secret) and cipher suite.
- The server instructs the client to verify that the SSL negotiation has been successful.
If the server needs to verify the identity of the SSL client, during the handshake, the server sends a Certificate Request message to request a certificate from the client, who then sends its own certificate and a Certificate Verify message to the server.
Relationship Between SSL and TLS
Both SSL and TLS are encryption protocols. TLS is actually the successor protocol to SSL. TLS is an SSL-based security protocol that ensures data integrity and confidentiality. It prevents eavesdropping on the communication between the client and server. SSL was first developed by Netscape and has three versions: SSL 1.0, SSL 2.0, and SSL 3.0. TLS 1.0 is a new protocol developed by the Internet Engineering Task Force (IETF). It is based on SSL 3.0 and is a successor of SSL 3.0. TLS 1.0 and SSL 3.0 are almost the same. In TLS 1.0, only some security vulnerabilities in earlier SSL protocols are fixed. Actually, all SSL certificates are SSL/TLS certificates.
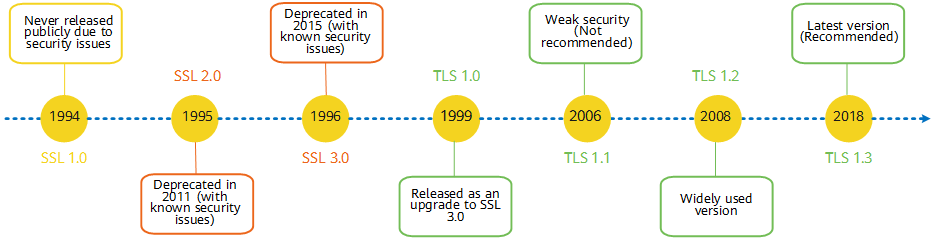
History of SSL and TLS versions
- Author: Gao Tingting
- Updated on: 2024-02-27
- Views: 3594
- Average rating:






