What Is Policy Association?
Policy association separates control points and enforcement points of authentication policies to implement centralized policy control and distributed policy enforcement, which simplifies user access policy deployment on large and midsize campus networks.
Why Do We Need Policy Association?
To ensure campus intranet security, IT administrators usually need to deploy Network Access Control (NAC) authentication policies on access devices to control users' network access rights.
However, large and midsize campus networks have a large number of access devices and complex user access policies, which brings the following problems:
- NAC deployment workload is heavy, and NAC management and maintenance are difficult.
- Servers connected to access devices face heavy pressures.
- A user can access the network only at a fixed location. Once the access location changes, the user cannot access the network, as the access device does not have the authentication policy for the user.
To solve the preceding problems and simplify NAC deployment on large and midsize networks, authentication points are moved upwards from the access layer to the aggregation layer, and access switches transparently transmit 802.1X packets. That said, it results in another set of issues:
- Access between users connected to the same access switch in the same VLAN is not controlled.
- The authentication device cannot detect the access locations of users connected to the same access switch, causing difficult fault locating.
- If a user goes offline unexpectedly (for example, due to a power failure), the authentication device cannot detect the logout immediately, which may cause the following problems:
- The AAA server still performs accounting for the user, causing incorrect accounting.
- An unauthorized user can use this user's IP address and MAC address to access the network.
- If there are many offline users, these users are still counted as online users of the device. As a result, other users may fail to access the network.
To address the disadvantages of the preceding two solutions, the policy association solution is proposed.
The core idea of policy association is to separate control points and enforcement points for authentication policies to implement centralized policy control and distributed policy enforcement.
- Policy control point: Deployed at the aggregation layer or higher, policy control points are responsible for interconnection with the controller and have user authentication and access rights configured. Policy control points deliver user policies to policy enforcement points through Control And Provisioning of Wireless Access Points (CAPWAP) tunnels for policy enforcement.
- Policy enforcement point: Deployed at the access layer, policy enforcement points enforce user policies configured on policy control points, and report user terminal status to the policy control points through CAPWAP tunnels.
As such, policy association simplifies NAC deployment on large and midsize networks and prevents problems caused by moving authentication points upwards.
What Is the Network Architecture of Policy Association?
The following figure shows the network architecture of policy association, which consists of three parts: terminal, authentication access device, and authentication control device.
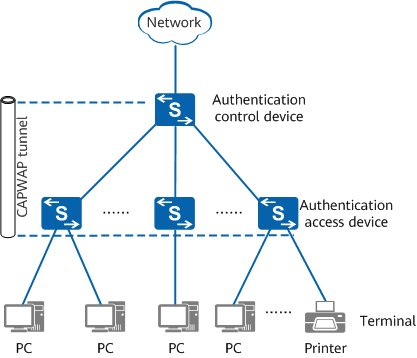
Network architecture of policy association
- Terminal: provides a human-machine interface for user authentication and resource access. Terminals include PCs, laptops, smartphones, tablets, and dumb terminals.
- Authentication access device: functions as a policy enforcement point to implement network access policies for users.
- Authentication control device: functions as a policy control point to authenticate users and control user access policies.
The authentication control and access devices use the CAPWAP channel to establish a connection. Through this CAPWAP channel, the authentication control and access devices associate users, communicate messages, deliver user authorization policies, and synchronize user information.
How Does Policy Association Work?
The following figure shows the policy association process.
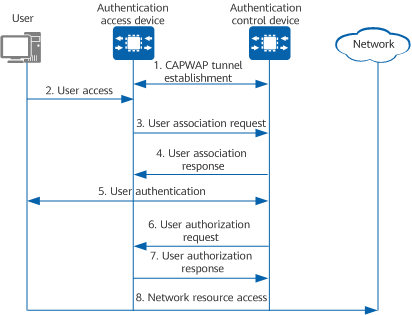
Policy association process
- An authentication control device establishes a CAPWAP tunnel with an authentication access device.
- The authentication access device detects the access of a new user, creates a user association entry, and saves basic information such as the user and access port.
- The authentication access device sends a user association request to the authentication control device.
- The authentication control device creates a user association entry, saves the mapping between the user and authentication access device, and sends a user association response to notify the authentication access device of successful association.
- The user initiates an authentication request to the authentication control device. The authentication access device forwards the authentication packet between the user and authentication control device.
- The authentication control device deletes the user association entry. When the authentication succeeds, it generates a complete user entry, sends a user authorization request to the authentication access device, and delivers the network access policy for the user.
- The authentication access device saves the user association entry, enables the specified network access rights for the user, and sends an authorization response to the authentication control device.
- The user accesses the specified network resources.
(The detailed CAPWAP tunnel establishment process is not mentioned above.)
- Author: Zhang Qimin
- Updated on: 2023-09-01
- Views: 886
- Average rating:






