What Is a Security Operations Center (SOC)?
A security operations center (SOC) is a centralized function within an enterprise that uses people, processes, and technology to improve the enterprise's security situation while preventing, analyzing, and responding to cyber security events. SOC teams detect endpoints, servers, databases, network applications, websites, and other systems to uncover potential threats in real time. The SOC can also collect the latest threat information, track the status of infrastructure and cyber-crime gangs, and deploy security solutions in advance to identify and fix system or process vulnerabilities before they are exploited by attackers.
What Are the Functions of a SOC?
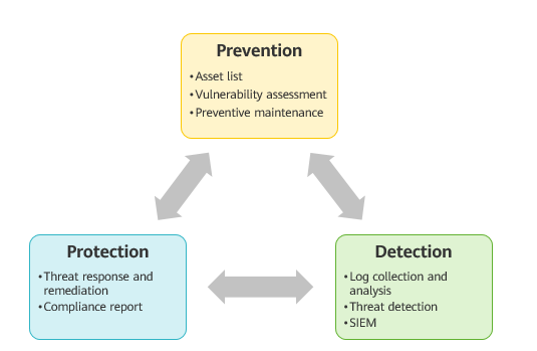
Three main SOC functions
- Prevention
- Asset list: In an enterprise, the SOC can use the asset discovery tool to check the systems, applications, databases, and servers to be protected, and identify security protection tools for vulnerability detection.
- Vulnerability assessment: The SOC team performs assessments on the vulnerability of software and hardware resources and the associate costs. It also conducts penetration tests and, based on the test results, updates security policies or threat event response plans.
- Preventive maintenance: To fully utilize existing security tools and measures, the SOC installs and upgrades patches, and updates firewalls, whitelists/blacklists, and security policies and procedures. The SOC also creates system backups to ensure business continuity in the event of a data breach, ransomware attack, or other cyber security event.
- Detection
- Log collection and analysis: The SOC uses devices such as firewalls or detection systems to collect and analyze log data, and identify abnormal activities.
- Threat detection: The SOC generates alarms based on identified suspicious activities from log data and indicators of compromise (IOCs). IOCs can indicate information such as malware types, suspicious DNS requests, and metadata, and in doing so help to identify attackers and attack motives.
- Security Information and Event Management (SIEM): The SIEM tool is often built in the SOC to automatically handle threats. SIEM can summarize log data, monitor alarms, and analyze security events.
- Protection
- Threat response and remediation: The SOC helps develop the enterprise's event response plan, responding to threats by isolating infected devices, deleting malicious files, and running antivirus software. It then investigates and analyzes root causes, and improves existing security policies based on the investigation results.
- Compliance report: The SOC reports the amount and type of damaged data to relevant authorities to ensure that the attacked enterprise complies with data privacy laws and regulations.
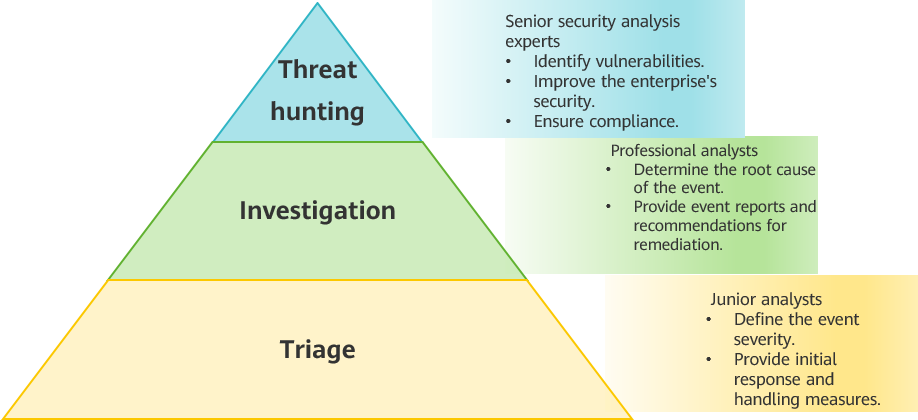
Three-tier SOC team structure
- Triage
Triage is the first tier of the SOC. Tier 1 personnel, consisting of junior analysts, are least experienced. They are responsible for triaging security events and determining the event severity. This includes identifying the source of the event, determining the event scope, and assessing related impacts. They are also responsible for providing initial response and handling measures, and finally escalating events to higher tiers if necessary.
- Investigation
Investigation is the second tier of the SOC. Tier 2 personnel, consisting of professional analysts, have greater expertise. They are responsible for investigating security events and determining the root cause. This includes analyzing logs, network traffic, and other data sources to identify the source of the event. They are also responsible for providing detailed event reports and recommendations for remediation.
- Threat hunting
Threat hunting is the third tier of the SOC. Tier 3 personnel, consisting of senior security analysis experts, are responsible for proactively hunting for threats in an enterprise's environment, using advanced detection tools to identify vulnerabilities, and providing suggestions on improving the overall security of the enterprise. They are also responsible for ensuring that enterprises' threat handling methods comply with industry and government laws and regulations.
By using the right tools and hiring appropriate analysts to monitor and manage enterprise networks, the SOC can detect and prevent threats and improve enterprise network security.
Common SOC Tools and Technologies
- Security information and event management (SIEM)
SIEM is one of the most important tools in the SOC. SIEM can aggregate data from multiple security tools and log files. It uses threat information analysis and artificial intelligence (AI) technologies to help the SOC detect ever-changing threats, thereby ensuring that events can be responded to faster than attacks are launched.
- Security Orchestration, Automation and Response (SOAR)
SOAR automates repetitive and predictable threat event response and remediation tasks, freeing up time and resources for more in-depth investigation and search.
- Extended Detection and Response (XDR)
XDR integrates security tools into the entire hybrid infrastructure of an enterprise, combines prevention, detection, investigation, and response, and provides capabilities such as threat visualization, threat analysis, event alarm, and automatic response to improve data security and defend against threats.
- Firewall
Firewalls can monitor incoming and outgoing network traffic, and allow or block traffic based on security rules defined by the SOC.
- Log management
As a part of the SIEM, log management records all logs of enterprise software, hardware, and endpoints. From these logs, users can obtain information about network activities.
- Vulnerability management
The vulnerability management tool scans the network to identify vulnerabilities that may be exploited by attackers.
- User and entity behavior analytics (UEBA)
UEBA is built into many security tools, and uses AI technologies to analyze data collected from devices and establish a baseline of normal activities for each user and entity. Once an activity deviates from the baseline, it is marked for further analysis.
Benefits of SOCs
- All-weather monitoring: Network threats are everywhere. To minimize network security risks, enterprises' infrastructure and data must be monitored around the clock. This can be achieved by SOCs, which respond to threat events immediately.
- Threat visualization: As enterprise networks grow in complexity, visualizing and ensuring security of the entire network is more challenging than ever. SOCs provide an intuitive view of enterprise network infrastructure and potential attacks.
- Better preventive measures and security policies: By unifying and coordinating enterprises' security tools, security practices, and responses to security events, SOCs can improve enterprises' preventive measures and security policies.
- Faster threat detection and response: By improving enterprises' threat detection, response, and prevention capabilities, SOCs can detect and respond to security threats more quickly, effectively, and cost-effectively, mitigating the impact of threats on enterprise services.
- Increased customer confidence: SOCs can increase customers' confidence in enterprises' data protection capabilities.
- Compliance assurance: SOCs ensure that enterprises comply with privacy regulations in the industrial, national, and even global level.
Huawei SOC-related Solutions
HiSec@Security Operations Center Solution consists of the cyber security collaborative management system, HiSec Insight, log audit, and SecoManager. This solution uses big data technologies to aggregate network-wide security data and build a SOC that integrates multi-dimensional data collection, situational awareness, response handling, and operations management. This implements unified operations management, policy control, threat monitoring, and O&M for security.
- Operations management: offers a unified O&M and operations system that implements security lifecycle management, such as security event source tracing, service ticket dispatching, and event handling.
- Data collection: collects, manages, and retrieves various security log data, and performs correlation analysis on the data. The data includes but is not limited to all logs of security devices, network devices, middleware, operating systems, databases, application layers, and more.
- Policy control: aggregates information such as security alarms, risks, and security situation, performs correlation analysis, intelligent inference, research and analysis, and decision-making to form security protection control policies and service security control policies. It also orchestrates, schedules, and configures services based on the decision-making results.
- Situational awareness: is a specific application of security big data, including security situation, security audit, and security risk assessment and warning.
HiSec@Security Operations Center Solution consists of the operations layer, analysis layer, management and control layer, and execution layer. It uniformly schedules and manages network, security, and cloud platform components and security capabilities, and provides customers with integrated, visualized, and global experience. This ensures unified security operations and collaborative protection and improves efficiency.
- Author: Zeng Yueqing
- Updated on: 2023-08-24
- Views: 1260
- Average rating:






