What Is Spyware?
Spyware is a kind of malware that enters a user's computer without their knowledge or permission, gathers personal data, and covertly sends it to third parties. Spyware usually spies on a user's computer—with access to applications, browsers, documents, cameras, or microphones—and collects personal information, including Internet usage, credit card, and bank account details. The information is then sent to advertisers, data collection firms, or malicious actors for a profit. As one of the most commonly used cyberattack methods, spyware may lead to data breaches and data misuse. Some spyware types may even make modifications to the user's system, resulting in slow network connection, application freezing, startup failure, or system breakdown.
Common Types of Spyware
Based on the degree of damage, spyware can be classified as follows:
- Adware and tracking cookies: spyware of the less dangerous forms which only monitor users' data.
- Trojan and system monitor: spyware of the advanced and dangerous forms which make modifications to a user's system in addition to data collection.
- Adware: The adware covertly sits on a computer or mobile device. It tracks users' browsing history or downloading activities to push targeted ads to users or conducted user analysis by inferring their preferences on products or services.
- Tacking cookies: Tracking cookies are saved on a device by a website that a user has visited and then used to follow the user's subsequent activity on the website. This is a typical technique for some advertisers to provide personalized ads or services.
- Trojan: A Trojan is a type of malware disguised as a legitimate program to trick users into installing it. The name of the Trojan stems from a well-known Greek myth. In the story, Greeks constructed a Trojan horse, a huge hollow wooden horse, to gain entrance into Troy during the Trojan War. A Trojan virus, similarly, appears as a genuine program in order to trick users into installing it. Trojans may be hidden in games, apps, software patches, or attachments included in phishing emails. Once downloaded, the Trojan can take control of the victim's operating system and carry out malicious actions.
- System monitor: The system monitor is usually disguised as freeware, which can capture almost all the operations on the user's computer. For example, the system monitor can record user activities such as keystrokes, online chats, e-mails, browsing records, or running programs.
Mechanism of Spyware Attacks
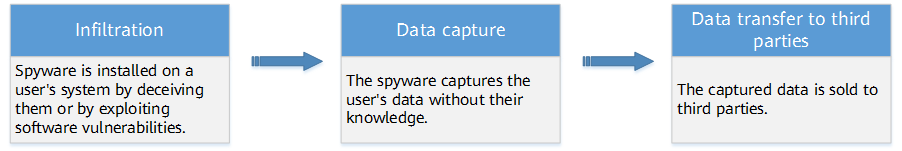
Once entering a user's computer or mobile device, spyware begins recording the data secretly. The spyware attack follows a three-step process.
- Infiltration: Most spyware is covertly installed on a user's system by deceiving them or by exploiting software vulnerabilities. Some typical causes of spyware infiltrating a device include:
- Security vulnerabilities: Attackers often exploit code and hardware vulnerabilities to gain unauthorized access to devices and systems and plant their spyware.
- Software bundling: Spyware is bundled with or incorporated into legitimate software so that users may unknowingly install the spyware that is believed to be harmless.
- Phishing: Phishing is a type of spyware attack that uses disguised emails, malicious links, or files to trick the target into installing.
- Data capture: Once successfully infiltrating a user's computer or mobile device, the spyware performs a series of operations to capture the user's data, including:
- Records all that is entered on the keyboard, including the user name, password, and bank information.
- Records the audio, video, and screenshots.
- Records data in users' emails or applications.
- Records users' browsing history.
- Remotely controls user devices.
- Data transfer to third parties: The captured data is sold to third parties for malicious purposes.
How to Tell If You have Spyware
As its name suggests, spyware is malware designed to be deceptive and almost undetected. There are several signs that could indicate spyware infiltration, which requires in-time consideration, including:
- Negative hardware performance, such as:
- Devices running slower than usual
- Devices suffering frequent crashes and freezes
- Devices lacking sufficient space or memory suddenly
- Applications or browsers with deteriorating performance, such as:
- Pop-up ads repeatedly appearing in browsers
- Browser searches redirecting to new pages
- New toolbars, search engines, or programs automatically appearing on the device
- Antivirus and other security software not running
How to Defend Against Spyware?
Spyware Protection for Mobile Devices
- Improve security awareness and avoid accessing unknown websites or clicking suspicious links.
- Uninstall unknown applications.
- Only download trusted apps from the official store.
- Update the operating system periodically. Regular operating system updates help reduce the risk of being infected by malware, such as updating patches that fix known vulnerabilities.
- Restrict application permissions. Be careful about giving permissions to apps that trace location data and take control of cameras or microphones.
Spyware Protection for Computers
- Improve security awareness and avoid opening unknown email links or attachments.
- Enable or download the pop-up blocker and avoid clicking pop-up ads.
- Only download trusted apps from the official store.
- Update the software, operating system, or browser periodically.
- Use antivirus software. Antivirus software automatically deletes spyware from devices, ensuring security.
- Keep the firewall on to guard against spyware.
Spyware Protection With Huawei
Huawei HiSecEngine USG6000E/6000F series AI firewalls provide you with the IPS function to protect your network against various attacks. When an extranet user accesses the intranet, the firewall can detect the access traffic. If the traffic is abnormal, the IPS blocks the intrusion attempt immediately. Otherwise, the traffic is allowed. Similarly, when an intranet user accesses an external network, if the accessed web page or server contains malicious code, the device blocks the access. Otherwise, the traffic is permitted.
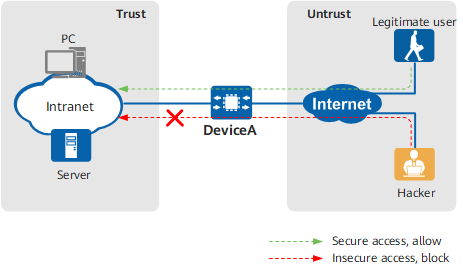
Networking diagram of the IPS
An IPS has the following advantages:
- Comprehensive protection: An IPS can provide a comprehensive network protection, preventing all types of attacks, including spyware, worms, viruses, Trojans, botnets, common gateway interface (CGI) attacks, cross-site scripting (XSS) attack, injection attacks, directory traversal, information leaks, remote file inclusion (RFI) attacks, overflow attacks, code execution, denial-of-service (DDoS) attacks, and scanning tool attacks.
- Internal and external protection: The IPS can protect enterprises from both external and internal attacks. IPS devices can detect the traffic passing through and protect servers and clients.
- Precise protection: The IPS signature database is continuously updated so that devices can stay up to date with the constantly evolving threats. You can periodically update the IPS signature database of devices from the Huawei security center to ensure the IPS is always effective.
- Author: Zheng Kaili
- Updated on: 2024-01-10
- Views: 584
- Average rating: