What Is Virtual Private Cloud (VPC)?
A VPC provides a logically isolated, configurable, and manageable virtual network environment for cloud resources including cloud servers, cloud containers, and cloud databases, improving cloud service security and simplifying network deployment.
Why Is VPC Needed?
With continuous development of cloud computing, requirements for a virtualized network are increasingly high: A network with scalability, security, reliability, and privacy is preferred. The traditional two-layer network model has many problems, among which the biggest problem is security. By default, all devices on the Layer 2 network can communicate with each other. As a result, cloud hosts are vulnerable to malicious attacks from other users on the same network. A VPC can isolate a dedicated network for each user based on public network resources, ensuring user security and privacy. In addition, users can flexibly define IP addresses and routing policies for hosts in a VPC.
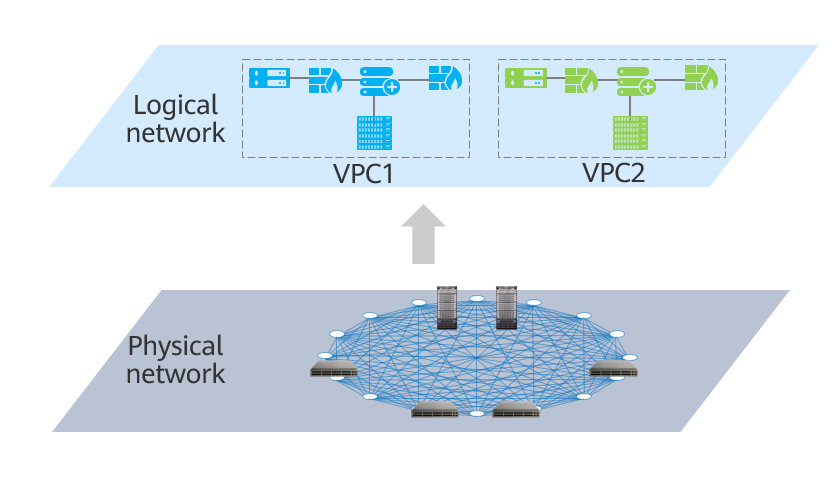
VPC network model
Main Components of a VPC
Each VPC is a virtual network environment. You can create a VPC to divide a physical network into logical networks, including logical units such as subnets, vRouters, and vFWs.
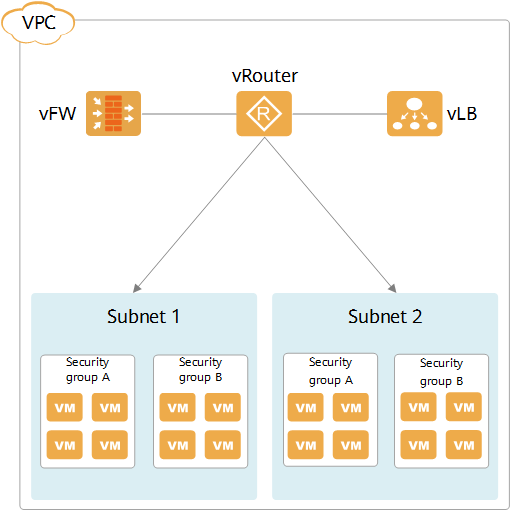
VPC structure
Subnet: A subnet is a network segment in a VPC and belongs to a Layer 2 network. One or more internal subnets can be created for a VPC to manage cloud hosts with different service requirements. Cloud hosts in different VPC internal subnets can communicate with each other.
vRouter: A vRouter is a virtual router that functions as the network hub of a VPC and connects subnets. It also functions as the gateway of each subnet to implement communications between subnets.
vFW: A vFW is a virtual firewall that controls traffic entering and leaving subnets or VPCs to ensure VPC network security.
Security group: Similar to a virtual firewall, a security group is used to ensure the network security of a VPC. The difference is that a virtual firewall controls access based on subnets or VPCs, whereas a security group controls access based on hosts. A security group is a collection of access control rules for cloud hosts that have the same security protection requirements and are mutually trusted.
Principles of VPC
Based on the network overlay technology, a VPC is implemented by constructing a large Layer 2 network over a Layer 3 network. An overlay network is a software-defined virtual logical network built on an underlay network. The overlay technology is essentially an L2 over IP tunnel encapsulation technology, including VXLAN and NVGRE. With this technology, original Layer 2 packets from a host are encapsulated and transparently transmitted over the network. When reaching the destination device, the encapsulated packets are decapsulated into the original packets, which are then sent to the target host. In this way, hosts can communicate at Layer 2.
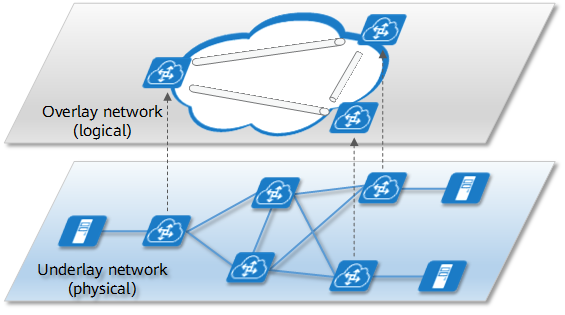
Overlay network
- Author: Gao Yangyang
- Updated on: 2023-06-21
- Views: 1530
- Average rating:






