What Is an XSS Attack?
Cross-site scripting (XSS) attacks are a a type of injection attack that exploits vulnerabilities on web programs. In XSS attacks, attackers inject executable malicious scripts into websites or web applications that do not properly validate user input. When users access the websites or web applications, the malicious scripts can then be executed to steal personal data, display advertisements, or even tamper with web page content. XSS attacks typically target sharing platforms such as online forums, blogs, and message boards.
Different from other types of web attacks, XSS is a client-side code injection attack, in which malicious scripts are executed on the client side such as the front-end browser or web application rather than the back-end server or database. Therefore, in an XSS attack, the final victim is the access user.
How Do XSS Attacks Work?
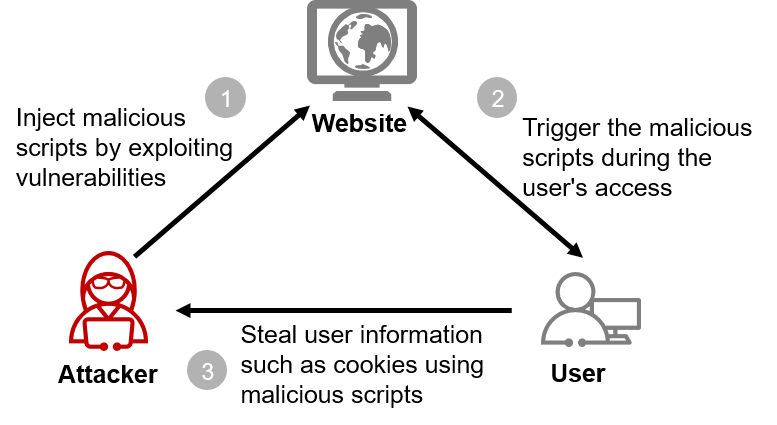
XSS attacks work by manipulating vulnerable websites so that they return malicious scripts to users. The main process is as follows:
- Attackers discover vulnerable websites, and exploit vulnerabilities to inject malicious scripts into web pages.
Script injection may occur on websites that do not properly validate user input. Malicious scripts are usually written in JavaScript, Java, VBScript, ActiveX, or Flash.
- When a user accesses a website, the malicious script is loaded to the browser and executed.
There are many ways to trigger malicious scripts, for example, luring a user into clicking on a link, or automatically triggering the script when a web page is loaded or a user's mouse hovers on a specific element of the web page.
- Malicious scripts can access cookies, session tokens, and other sensitive information stored in the browser, and even rewrite page content.
By stealing user cookies, attackers can impersonate users and perform authorized operations to obtain user identity information and user files. In addition, attackers can use XSS to spread malware, corrupt web page content, and perform phishing to launch more destructive attacks.
XSS attack process
Common Types of XSS Attacks
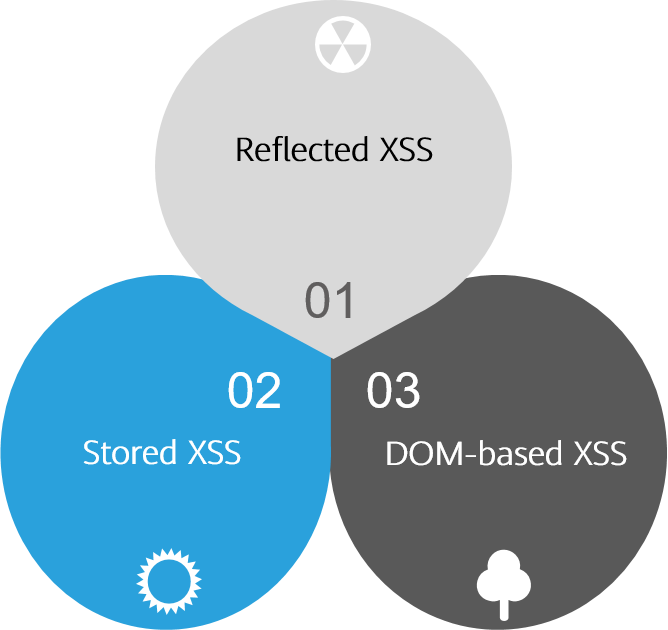
Figure 1 shows the common types of XSS attacks.
Reflected XSS
Reflected XSS is the simplest variety of XSS. This type of attacks occurs when the malicious script is included in the request sent to the vulnerable web server, which then reflects the request to the browser for execution. In other words, the malicious script is submitted to the web server as a client request. After parsing the request, the server returns the script in the response message for the browser to execute. As such, attackers want to lure users into clicking on links to send requests to the web server by using phishing emails, pop-up links, and other social engineering techniques.
Attackers usually add malicious code to the end of a valid URL to construct a link. For example:
https://example.com/index.php?user=<script>malicious code</script>
After the user clicks on this link, the malicious script will be executed as the browser trusts the website.
As seen above, the web server directly sends HTTP GET or POST requests to complete the attack instead of storing malicious scripts. This makes reflected XSS easy to implement. This type of attack is also called non-persistent XSS because it needs to be triggered by each victim.
Stored XSS
Stored XSS, also known as persistent XSS, is the most damaging type of XSS. In a stored XSS attack, the injected script is permanently stored on the target web server, such as a database, memory, or file system. As long as the injected script is not cleared, it is loaded as a user accesses a web page.
Stored XSS attacks usually occur on websites that permit content sharing, such as forums, blogs, and message boards. If a website has vulnerabilities and fails to validate user input thoroughly, it becomes vulnerable to exploitation by attackers. Attackers use functions such as posting, commenting, and modifying personal information to submit malicious scripts to the web server for storage. In this case, all users who access the compromised web page will have the malicious script read without knowing it.
Compared with reflected XSS, stored XSS has a larger impact and endangers all visitors. However, this type of attack is more difficult to execute because attackers need to find vulnerabilities that can be exploited.
DOM-based XSS
Document Object Model (DOM)-based XSS is a more advanced type of XSS whereby the attacker injects malicious scripts into websites by tampering with the DOM. The DOM provides structured description of documents and associates HTML pages with scripts and programming languages. When a web page is loaded, the browser creates the DOM of the page. JavaScript on the client side of the web program can edit the DOM to dynamically modify the web page content. That is, JavaScript obtains data from the DOM and executes it locally. During this process, if data is not properly processed, attackers can inject malicious scripts into the DOM and trigger attacks when reading the DOM data. Commonly exploited DOM includes document.URL, location.hash, and document.referrer.
DOM-based XSS attacks are greatly different from reflected and stored XSS attacks. In a DOM-based attack, the entire attack process occurs within the user's browser, without the web server parse or response to the access request. This makes it difficult to locate, as Web Application Firewall (WAF) devices cannot obtain communication traffic.
How Do I Prevent XSS Attacks?
From the perspective of web program development, developers must comply with security development principles and take the following measures to prevent XSS attacks:
- Verify and filter the user input to check whether the input meets the expected format. Some special characters and tags (such as <script>) are filtered out to prevent malicious script injection.
- Escape the user input. Specifically, user input is escaped before the delivery to users. For example, escape ">" to ">". This prevents some characters in the received input from being interpreted as executable code and invalidates malicious scripts.
- Take security measures for cookies. For example, set the HttpOnly Cookie attribute to prevent JavaScript from reading cookies, thus preventing user identity authentication tokens and sensitive information from being stolen.
- Use the HTTP response header Concent-Security-Policy (CSP) to restrict the resources that can be loaded and executed, for example, restrict the source of JavaScript to prevent malicious script injection.
- Comply with OWASP's Cross Site Scripting Prevention Cheat Sheet when developing web programs.
- Perform penetration tests on web programs for security hardening.
From the perspective of website users, it is important to be aware of the risks associated with XSS attacks in order to prevent them.
- Disable JavaScript in the browser.
- Avoid clicking on unknown links in emails and forums.
- Update software and operating system patches in a timely manner.
- Install antivirus software.
Huawei Security Products Help You Defend Against XSS Attacks
WAF can help effectively defend against XSS attacks, which typically works by detecting attack signatures. Huawei AI firewalls integrate WAF functionality to detect XSS vulnerabilities and mitigate various web attacks, including XSS attacks, thereby meeting the one-stop security protection requirements.
- Author: Liu Shui
- Updated on: 2023-11-22
- Views: 667
- Average rating: