What Is Local Attack Defense?
How Does Local Attack Defense Work?
Local attack defense uses a multi-level security mechanism to provide hierarchical protection for a device. It provides the following functions: CPU attack defense, user-level rate limiting, attack source tracing, and attack defense.
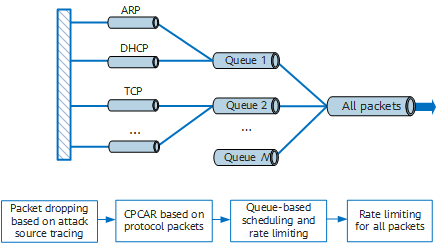
Hierarchical protection of local attack defense
Level 1: The device discards malicious packets sent to the CPU through a filter or the punishment function of attack source tracing.
Level 2: The device rate-limits protocol packets based on the Control Plane Committed Access Rate (CPCAR). That is, the device rate-limits packets sent to the CPU based on protocol types, such as ARP and DHCP, and each protocol can have a certain bandwidth, preventing excess packets of a protocol from being sent to the CPU. As such, protocol-based rate-limiting ensures that different protocols do not affect each other.
CPCAR control is the core of CPU attack defense and rate-limits the protocol packets on a per device basis. User-level rate limiting rate-limits protocol packets based on the MAC address of the user who initiates an attack.
Level 3: Queue-based scheduling and rate limiting. After rate-limiting protocol packets based on CPCAR, the device can allocate a queue to a type of protocols. For example, the device allocates a queue to management protocols such as Telnet and SSH and a queue to routing protocols. These queues are scheduled based on weights or priorities. When a conflict occurs, the device preferentially processes high-priority queues. The device can also limit the maximum rate of packets in each queue sent to the CPU and discards the protocol packets that exceed the rate limit in a queue.
Level 4: Rate limiting for all packets. At this level, the total number of packets processed by the CPU is limited to ensure that the CPU can process as many packets as possible within its processing capability. Before rate-limiting all packets, the device analyzes the contents and behaviors of the packets sent to the CPU to determine whether these packets are attack packets. If so, the device takes defense approaches such as discarding or rate-limiting the packets.
What Functions Does Local Attack Defense Provide?
Basic functions of local attack defense include CPU attack defense, user-level rate limiting, attack source tracing, and attack defense. These functions prevent service interruptions caused by excess packets sent to the CPU. CPU attack defense, user-level rate limiting, and attack source tracing are used for flow control, ensuring no excess normal service packets are sent to the CPU. Attack defense identifies and processes attack packets, preventing excess attack packets from being sent to the CPU.
CPU Attack Defense
The core of CPU attack defense is CPCAR, that is, rate limiting based on protocol packets. A network administrator can run commands to configure the CPCAR values for each type of protocol packets, CPCAR value of all packets sent to the CPU, and application layer association. In addition, when the default CPCAR cannot meet service requirements, adaptive adjustment of the default CPCAR value for protocol packets is supported.
Application layer association
Application layer association protects data transmitted over sessions of a specific protocol, such as OSPF, BGP, and FTP. After such a session is established, the protocol-based default CPCAR value no longer takes effect. Instead, the device uses the CPCAR value configured for the protocol in application layer association to rate-limit the transmitted packets. Typically, the CPCAR value configured for each protocol in application layer association is much greater than the protocol-based default CPCAR value, ensuring the reliability and stability of service operations.
Adaptive adjustment of the default CPCAR value for protocol packets
Adaptive adjustment of the default CPCAR value for protocol packets applies to protocol packets related to user access, such as ARP packets, covering scenarios where a fixed default CPCAR value cannot meet rate requirements. After this function is enabled, the device dynamically adjusts the protocol-based default CPCAR value based on the packet loss rate and CPU usage of protocol packets.
User-Level Rate Limiting
When user-side hosts are infected with viruses, they send a large number of protocol packets, overloading device CPUs and deteriorating their performance, which ultimately impacting services. To address this issue, a network administrator can configure user-level rate limiting, which identifies users based on MAC addresses and rate-limits only the user who initiates an attack, ensuring other normal users are unaffected. User-level rate limiting (based on users) is more precise and has less of an impact on normal users than CPCAR (based on devices). The processing flow is as follows:
- When receiving users' protocol packets, the device performs a hash calculation on the source MAC addresses and places packets from different source MAC addresses into different buckets.
- When the number of packets placed in a bucket within the unit time exceeds the rate limit, the bucket discards the excess packets. The device counts the number of packets discarded by a bucket at a specified interval. If the number exceeds the rate limit, the device reports a packet loss log for the bucket.
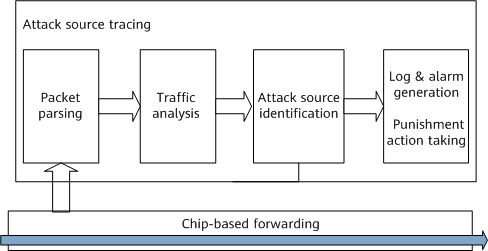
Attack Source Tracing
Attack source tracing protects the CPU against denial of service (DoS) attacks. A device enabled with attack source tracing analyzes packets sent to the CPU, collects statistics on the packets, and considers packets exceeding the configured threshold as attack packets. The device finds the source user address and port based on packet information, generates logs and alarms to alert network administrators, and takes punishment actions.
The detailed process is as follows:
- Packet parsing: The device parses packets to be sent to the CPU based on IP addresses, MAC addresses, and ports. A port is identified by physical port plus VLAN.
- Traffic analysis: The device counts the number of received protocol packets based on IP addresses, MAC addresses, or ports.
- Attack source identification: When the number of packets sent to the CPU in a unit time exceeds the threshold, the device considers that an attack has occurred.
- Processing after identification: After detecting an attack, the device sends a log or alarm to notify the network administrator or directly implements punishment (for example, discarding attack packets).
Attack source tracing processAttack source tracing also provides the whitelist function. After legitimate users are added to a whitelist, the device does not perform source tracing or punishment actions on packets from these users, so that such packets can be sent to the CPU for processing. A whitelist can be flexibly configured based on ACLs or ports.
Attack Defense
Before rate-limiting all packets, a device enabled with attack defense analyzes the content and behavior of packets sent to the CPU to determine whether these packets are attack packets. If so, the device takes defense approaches on these packets. Attack defense mainly defends against the following attacks: malformed packet attacks, fragmentation attacks, TCP SYN flood attacks, UDP flood attacks, and ICMP flood attacks.
Which Attacks Can Local Attack Defense Defend Against?
Malformed Packet Attack
Attack Type |
Characteristics |
Identification Criteria |
|---|---|---|
Flood attack from IP null payload packets |
An IP null payload packet has only a 20-byte IP header, and no data section. |
The data section of an IP packet is missing. |
Attack from IGMP null payload packets |
A normal IGMP packet consists of a 20-byte IP header and an 8-byte data part, equating to a total length of 28 bytes. An IGMP null payload packet, on the other hand, consists of less than 28 bytes. |
The total length of an IGMP packet is less than 28 bytes. |
LAND attack |
A Local Area Network Denial (LAND) attacker targets the defects in the three-way handshake mechanism of TCP, sending a SYN packet in which both the source and destination addresses are the target host's address and the source and destination ports are the same. After receiving the SYN packet, the target host creates a null TCP connection by using its own address as both the source and destination addresses, and retains this connection until it times out, wasting network resources or even crashing the system. |
The source and destination addresses or source and destination ports of TCP SYN packets are the same. |
Smurf attack |
An attacker sends an ICMP Request packet with a source address as the target host's address and a destination address as the broadcast address of the target network. As such, all hosts on the target network receive the ICMP Request packet, after which they send ICMP Reply packets to the target host. This inevitably leads to the target host receiving an excessive number of packets, consuming excessive resources or even crashing the system or network. |
The destination address of an ICMP Request packet is a broadcast address or subnet broadcast address. |
Attack from packets with invalid TCP flag bits |
A TCP packet contains six flag bits: URG, ACK, PSH, RST, SYN, and FIN.
|
The flag bits of a TCP packet meet one of the following conditions:
|
Fragmentation Attack
A fragmentation attack is an attack in which error fragments are sent to a target device, which then crashes, restarts, or consumes a large amount of CPU resources when processing such fragments, ultimately impacting services. Fragmentation attack defense enables a device to detect packet fragments in real time and discard or rate-limit them to protect the device.
Fragmentation attacks are classified into the following types.
- Excess-fragment attack: An IP packet is fragmented into over 8189 fragments, causing the device to consume a large amount of CPU resources when reassembling packets.
- Excess-offset attack: An attacker sends a fragment with an offset value larger than 8189 to a target device, which then allocates memory space to store all fragments, consuming a large amount of resources.
- Repeated fragment attack: In a repeated fragment attack, fragments are sent to a target host multiple times. As a result, the target host may experience high CPU usage or a memory error. Such an attack is carried out in one of the two ways: The same fragments are sent multiple times, or different fragments with the same offset are sent.
- Syndrop attack: A Syndrop attack exploits the mechanism of IP fragmentation to put the second fragment into the first. The offset of the second fragment is smaller than that of the first fragment, and the offset plus the data field of the second fragment does not exceed the tail of the first fragment. A Syndrop attack uses TCP packets that carry a SYN flag and also IP payload.
- Error fragment attack: The second fragment of an IP packet is put into the first. That is, the offset of the second fragment is smaller than that of the first fragment. Based on protocols and payload lengths, such attacks are classified into Syndrop attacks, NewTear attacks, Bonk attacks, and Nesta attacks.
When an excess-fragment attack, an excess-offset attack, a Syndrop attack, or an error fragment attack occurs, the device discards all fragments. When a repeated fragment attack occurs, the device applies the committed access rate (CAR) limit to packet fragments, reserves the first fragment, and discards all the remaining repeated fragments to protect the CPU.
TCP SYN Flood Attack
A TCP SYN flood attack exploits the vulnerability of the TCP three-way handshake. During the TCP three-way handshake, when the receiver (target device) receives the initial SYN packet from the sender (attacker), it returns a SYN+ACK packet to the sender. The connection remains in a half-open state while the receiver waits for the final ACK packet from the sender. If the receiver does not receive the ACK packet, it retransmits a SYN+ACK packet to the sender. Finally, after several retransmission attempts, the receiver shuts down the session and then updates the session in memory. The period from the first SYN+ACK packet being sent to session teardown is approximately 30 seconds.
During this period, an attacker may send thousands of SYN packets to all open interfaces, and never responds to SYN+ACK packets from the receiver. This causes memory overloading on the receiver and prevents the receiver from accepting new connection requests. The receiver then disconnects all existing connections.
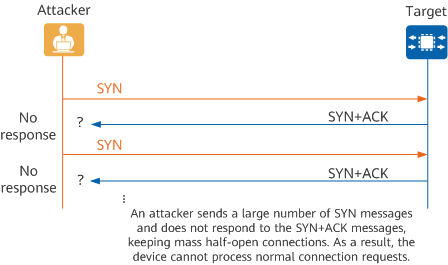
TCP SYN flood attack
With defense against TCP SYN flood attacks enabled, the device rate-limits TCP SYN packets and discards SYN packets exceeding the rate limit to ensure that system resources are not exhausted if an attack occurs.
UDP Flood Attack
A UDP flood attack is an attack in which a large number of UDP packets are sent to a target device within a short time, causing the target device to be busy with these UDP packets and fail to process normal services. UDP flood attacks are classified into two types:
- Fraggle attack: An attacker sends UDP packets where the source address is the target device's address, the destination address is the broadcast address of the target network, and the destination port is port 7. If multiple hosts use UDP echo services on the broadcast network, the target device receives excessive response packets from these hosts and becomes occupied while processing these packets.
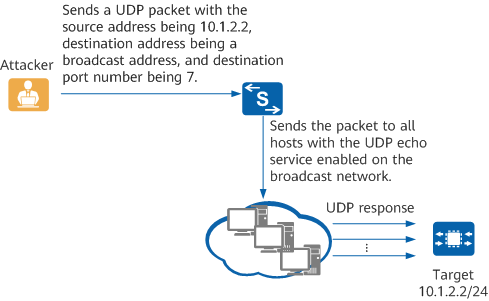
Fraggle attack
The device with defense against UDP flood attacks enabled considers packets from UDP port 7 as attack packets and discards them.
- UDP diagnosis port attack: An attacker sends a large number of UDP request packets to the target device's UDP diagnosis ports (such as 7-echo, 13-daytime, and 19-Chargen), causing flooding and consuming network bandwidth resources. In addition, as the target device consumes CPU resources when responding to these UDP request packets, the system becomes overloaded and cannot process normal services.
The device with flood attack defense enabled considers packets from UDP ports 7, 13, and 19 as attack packets and discards them.
ICMP Flood Attack
A network administrator typically monitors a network and rectifies faults using the ping tool as follows:
- The source host sends an ICMP Echo message to a target device.
- Upon receiving the ICMP Echo message, the target device sends an ICMP Echo Reply message to the source host.
If the target device receives many ICMP Echo messages from an attacker, it becomes occupied and unable to process other data packets. As a result, normal services are affected.
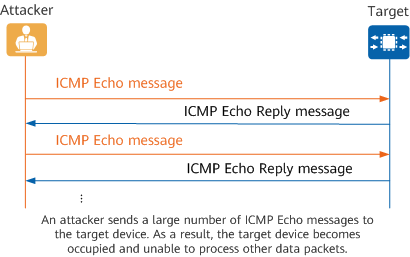
ICMP flood attack
With defense against ICMP flood attacks enabled, the device rate-limits ICMP messages to ensure that system resources are not exhausted if an attack occurs.
- Author: Fu Xiaoqin, Meng Xianhai
- Updated on: 2024-02-27
- Views: 2931
- Average rating: