What Is a DDoS Attack?
Distributed denial-of-service (DDoS) attack is a malicious attempt to overwhelm one or more targets with a massive influx of Internet traffic, ultimately depleting the target's network resources. This results in the target system's inability to connect to networks or provide normal services. DDoS attacks can be categorized into three types based on the location of the attack: network-layer attacks, transport-layer attacks, and application-layer attacks. Attackers frequently use a combination of these attack types, leading to an increase in threats especially as the complexity of attacks constantly evolves. The economic and brand losses caused by DDoS attacks can be significant for the targeted organizations — there is also a risk of core service data being stolen. Therefore, the DDoS defense system is widely implemented across various industries to effectively block and mitigate the impact of DDoS attacks on normal services.
DDoS Attack Types
DDoS attacks can be categorized into three types based on the targeted network layers: network-layer attacks, transport-layer attacks, and application-layer attacks.
Network-Layer Attacks
The network layer is responsible for routing and forwarding data packets between different networks. DDoS attacks at this layer aim to deplete network bandwidth resources. Common attack subcategories include ICMP flood attack, ARP flood attack, and IP fragmentation attack.
Attack Subcategory |
Attack Mechanism |
|---|---|
ICMP Flood attack |
The Internet Control Message Protocol (ICMP) is a protocol in the TCP/IP protocol suite used to transmit control messages between IP hosts and routers. ICMP's design characteristics make it readily usable for attacking. When an attacker sends numerous ICMP packets to the target system or network, the target host consumes a large amount of CPU resources to process and respond to the packets, exhausting device resources. This further leads to the device becoming unable to provide services for authorized users. |
ARP Flood attack |
The Address Resolution Protocol (ARP) is used to resolve IP addresses into MAC addresses. When a host broadcasts an ARP request message, all hosts on the same network segment can receive the message. This provides an opportunity for attackers to launch attacks by sending a large number of ARP requests, aiming to exhaust limited network resources by using useless broadcast information and leading to network congestion. Because ARP has no built-in authentication mechanism, hosts can cache any ARP replies they receive in their ARP table. This vulnerability enables ARP spoofing, where attackers can manipulate mappings between IP and MAC addresses by sending bogus data. |
IP Fragmentation attack |
IP fragmentation is an Internet Protocol (IP) process that breaks packets into smaller pieces (fragments) so that the resulting pieces can travel across a link with a smaller maximum transmission unit (MTU) than the original packet size. The fragments are then reassembled by the receiving host. IP fragmentation is commonly used on networks. It can be used in DDoS attacks, whereby an attacker sends deliberately fragmented data packets to the target system or network, expecting the target system or network to reassemble the data packets. This consumes many resources, leading to resource exhaustion. |
Transport-Layer Attacks
The transport layer is responsible for transferring data across a network and provides error-checking mechanisms and data flow controls. DDoS attacks at this layer intend to overload target servers or network devices. Common attack subcategories include SYN flood attack, ACK flood attack, and UDP flood attack.
Attack Subcategory |
Attack Mechanism |
|---|---|
SYN Flood Attack |
SYN flood is one of the original DDoS attacks on the Internet. This classic attack leverages the TCP three-way handshake mechanism. An attacker typically uses tools or control zombie hosts to send many TCP/SYN packets with variable source IP addresses or ports to the server. After the server responds to these packets, numerous half-open connections are generated. Once system resources have been exhausted, the server can no longer provide normal services. |
ACK Flood Attack |
In an ACK flood attack, the attacker tries to overwhelm the target with many fake ACK packets (carrying oversized payloads) through a botnet, causing link congestion. Alternatively, the attacker sends requests with variable source IP addresses and ports at a very high packet rate, attempting to overload the forwarding device. As a result, the network breaks down or the server's performance deteriorates, causing the target server to deny normal services. |
UDP Flood Attack |
UDP flood attacks are used frequently for larger bandwidth DDoS attacks. These attacks allow a hacker to overwhelm ports on the target host with IP datagrams containing the stateless UDP protocol. The receiving host checks for applications associated with these UDP datagrams and, upon finding that none exist, it sends back a Destination Unreachable packet. Once the target host is overwhelmed by attack traffic, the system does not respond. As a result, authorized users cannot use the system. |
Application-Layer Attacks
The application layer provides common network application services, such as email, web browsing, file transfer, and other applications. DDoS attacks at this layer aim to limit the availability of applications to its intended users. Common attack subcategories include DNS flood attack, HTTP flood attack, and CC attack.
Attack Subcategory |
Attack Mechanism |
|---|---|
DNS Flood Attack |
The attacker manipulates many zombies to initiate massive domain name query requests to the target, aiming to interrupt the DNS resolution of the domain. Such attacks compromise the capability of websites, APIs, or web applications to respond to legitimate traffic. As a result, legitimate users cannot find the address used to invoke specific resources, leading to temporary service interruption or even service unavailability. |
HTTP Flood Attack |
|
CC Attack |
CC attacks are mainly used to attack web pages. Generally, the attack target is the server that provides web page access services. An attacker sends many seemingly valid requests to the victim server through the proxy server. The CPU usage stays at 100% for a long time, and there are connections that cannot be processed completely. As a result, normal access is terminated and the system breaks down. |
DDoS Attack Landscape
According to Global DDoS Attack Status and Trend Analysis in 2022 the current DDoS attack landscape exhibits the following characteristics:
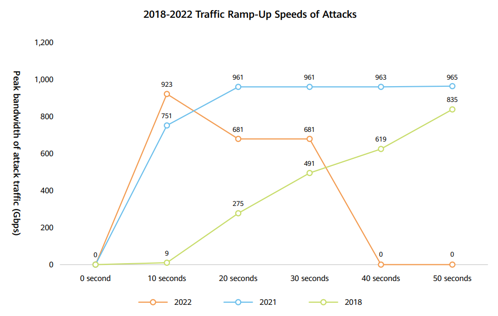
- Traffic of volumetric attacks is accelerated in seconds, and the ramp-up speed reaches a record high, challenging the response speed of the defense system.
Terabit-strong attacks feature fast flooding, which is a noticeable signature of volumetric attacks. The peak attack traffic ramps up to 800 Gbps to 1 Tbps, taking 20 seconds in 2021 but only 10 seconds in 2022.
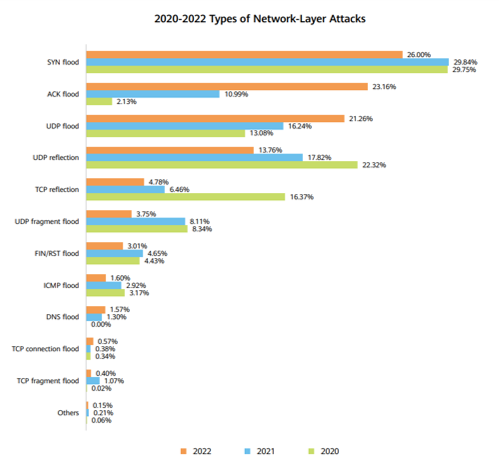
- Network-layer and application-layer attacks continuously use the "fast flooding" tactic, and the attack complexity continuously evolves.
57.40% of network-layer attacks and 40.49% of application-layer attacks last for no more than 5 minutes.
In 2022, SYN flood, ACK flood, UDP flood, UDP reflection, and TCP reflection attacks were the top 5 network-layer attacks. Over the past three years, the proportions of ACK flood and UDP flood attacks have increased year by year.
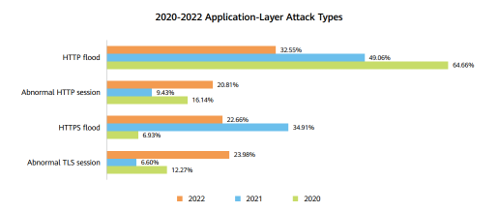
In 2022, with the gradual use of TLS to secure HTTP traffic, the proportion of HTTP flood attacks decreased compared with previous years. However, TLS-layer attacks were active, further increasing the proportion of TLS abnormal session attacks.
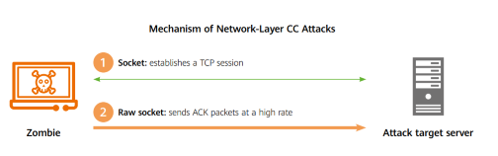
- The continuous evolution of network-layer CC attacks poses an increasing threat and challenges the automation of the defense system.
In network-layer CC attacks, threat actors combine the forged source flood attack technique with the session layer attack technique. Because of the obvious attack effect, CC attacks are widely used to attack HTTP and HTTPS ports. In such an attack, threat actors also use an attack tactic that combines both high-rate and low-rate data streams, making defense far more difficult.
From 2021 to 2022, network-layer CC attacks evolved into multiple variants, making them one of the most difficult-to-defend attacks on the Internet.
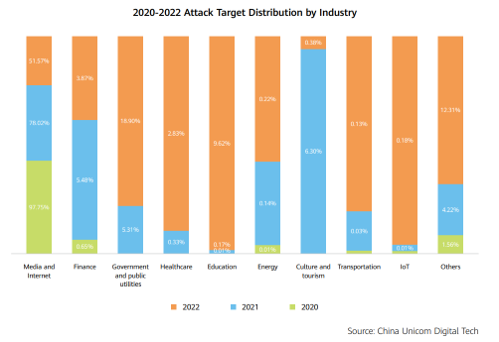
- The media and Internet, government and public utilities, education, finance, and healthcare industries are the top 5 attack target industries.
In 2022, the proportion of attacks targeting the education industry, the healthcare industry, and the government and public utilities industry increased by 56.6 times, 8.6 times, and 3.6 times, respectively since 2021. The Industrial Internet, as an emerging field, becomes the new target of attacks. In 2022, the Industrial Internet was attacked 18 times more frequently than it was in 2021.
DDoS Defense System
The key to mitigating DDoS attacks is how to accurately distinguish malicious traffic from normal traffic. In addition, the response speed of the DDoS defense system becomes an increasingly important factor because volumetric attacks can reach an intended scale in seconds.
Based on its in-depth understanding of customer requirements and professional security research, Huawei has launched the resilient and robust AntiDDoS System to defend against DDoS attacks.
- Superb performance
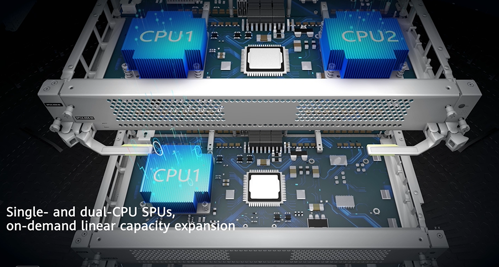
The NP collaborates with the CPU to accelerate defense. A standalone device in the AntiDDoS12000+SecoManager Solution can offer up to 2.4 Tbps defense performance, efficiently guarding against volumetric attacks.
- Millisecond-level response
The AntiDDoS1900+SecoManager Solution can respond to attacks within seconds or even milliseconds, analyze attack traffic behavior in a multi-dimensional way, and quickly block the attacks, achieving zero impact on services.
- Precise defense
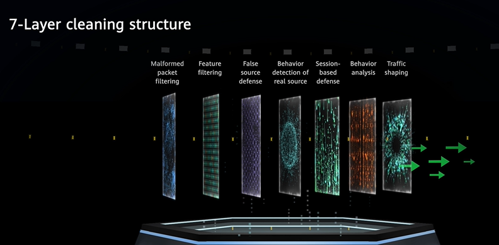
The AntiDDoS System provides Seven-layer intelligent filtering that allows for multi-dimensional behavior analysis on hundreds of complex DDoS attacks. This helps accurately identify and filter out malicious traffic while protecting mission-critical service systems such as web, app, and API systems.
- Intelligent O&M
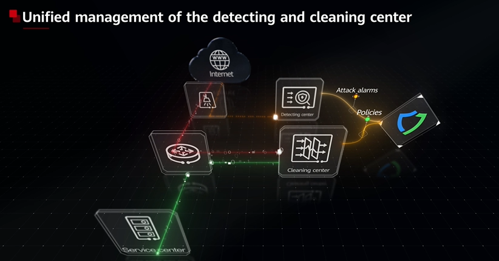
The AntiDDoS device can work with SecoManager Security Controller to implement automatic defense. SecoManager provides multiple industry policy templates to automatically defend against 99% of attacks. In addition, automatic policy tuning is provided for false negative flows, which helps continuously improve DDoS protection capabilities. Huawei AntiDDoS series helps slash O&M costs and implement intelligent O&M management.
- Author: Zhao Zhigang
- Updated on: 2023-07-26
- Views: 2122
- Average rating: