What Is Sandboxing?
In the computer field, sandboxing is a security mechanism that isolates running programs, such as untrusted processes or code, to restrict their access permissions. The term "sandbox" comes from the concept of the children's playground sandbox, an isolated area for imaginative and unrestricted play. Similarly, a digital sandbox provides a virtual environment to execute programs. The virtual environment contains some virtual hardware and software resources, such as file systems, networks, and operating systems, to run applications or processes. A sandboxed program can access only the limited number of resources inside the sandbox, without affecting the external application, system, or platform. This prevents the program from permanently changing other programs or data in the computer. In the cybersecurity field, sandboxing isolates malicious files to identify unknown attacks.
Principles of Sandboxing
Three technologies are involved in sandboxing: virtualization, access control, and anti-evasion.
- Virtualization
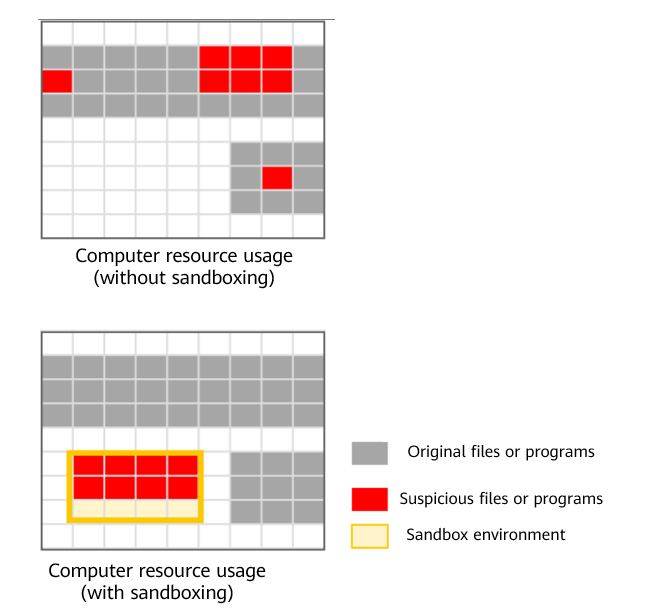
Virtualization is a resource management technology. It abstracts physical resources of a computer—including the CPU, memory, and disk space—into virtual resources for resource reallocation. As shown below, a sandbox is equipped with virtualization to ensure that untrusted resources are protected and run normally in an isolated environment. In short, suspicious or to-be-tested programs are isolated in the sandbox and run by using internal resources, without affecting external programs and ensuring the security of external resources.
Sandboxing mechanismBased on virtualization layers, sandboxes can be classified into system-level sandboxes and container-level sandboxes. A system-level sandbox is a special virtual machine, usually containing a complete set of virtualized computer software architecture, that is, virtual devices and an operating system. However, a container-level sandbox is like a container deployed in an application, comprising isolated files, programs, and resources possibly required. Compared with the system-level sandbox, the container-level sandbox occupies less memory and hard disk space.
What distinguishes the sandbox from a typical VM or container is its focus on security isolation, that is, to create an isolated environment so that anything happens within the sandbox exerts no external impact. However, the focus of a typical VM or container is application deployment. They provide an isolated deployment environment for applications to run normally, without being affected by any external changes.
- Access control
When a sandboxed program must access external resources for normal running, access control rules can be applied to the program for behavior restrictions. To implement access control, a program monitor and an access control rule engine are usually required. The program monitor monitors the program's behaviors and submit them to the access rule control engine. Based on access rules, the access rule control engine determines whether to allow the program to use the external resources.
- Anti-evasion
Once the sandboxing mechanism is detected, the malware reacts to bypass the sandbox's detection and analysis. To achieve this, the following anti-evasion technologies are necessary:
- Hide the information about the hardware registry containing fixed character strings of VMs from viruses.
- Return a message indicating that a symbolic link does not exist when a virus attempts to create the symbolic link for a driver by opening a VM or a kernel debugger.
- Hide unique service processes in VMs from viruses.
- Hide unique application software information in VMs from viruses.
- Intercept the system serial number registry query action and returns a serial number that is not suspected.
Application of Sandboxing
In cybersecurity, sandboxing is mainly used to detect viruses and prevent the spread of unknown software vulnerabilities.
Based on the virus signature database, traditional virus detection fails to detect or defend against unknown viruses. For instance, when signatures of an unknown virus are not included in the signature database, the antivirus product fails to detect the virus-infected file and does not block it. As a result, the endpoint which receives the file is infected. As virus attacks are increasingly growing in sophistication, such kind of passive defense is out of date. To counter this problem, sandboxing is introduced. Specifically, a sandbox offers an isolated environment to run suspicious files or programs. Then it examines each command in active state and searches for any suspicious behaviors, such as self-replication, file overwriting, and other actions that are common to viruses. If a high-risk action is detected, the file or program can be considered to be dangerous.
Therefore, the sandbox can effectively build a security line of defense against unknown viruses, transform defense from passive to proactive, and effectively mitigate zero-day attacks or advanced persistent threats (APTs). Figure 1-2 shows the sandbox detection process.
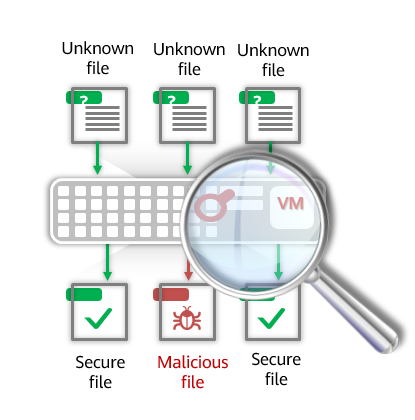
In addition, cybersecurity experts can use sandboxing to analyze the behavior and program of malware. In other words, cybersecurity experts can examine threats in detail by observing the behavior and process of malware in the sandbox and analyze how the target host is infected. The outcome will be applied to subsequent malware prevention on hosts.
Sandbox detection process
Benefits of Sandboxing
Sandboxing comes with several benefits:
- Protect hosts and operating systems
Unknown suspicious files run in the sandbox, reducing the risk of virus infection and intrusion on hosts.
- Prevent unknown threats such as zero-day vulnerabilities
Signature-based defense is used against known attacks and is outdated in coping with rapidly evolving threats. Sandboxing is an effective way to protect networks as it can prevent unknown threat malware that exploits zero-day vulnerabilities. A sandbox can isolate threats, thereby effectively blocking the spread of threats on the intranet.
- Collaborate with other security devices such as firewalls for protection
The sandbox can collaborate with other security devices deployed on the enterprise network, such as firewalls, intrusion prevention systems (IPSs), antivirus software, and endpoint security software. After identifying unknown threats, the sandbox can share the threat information with other security devices to block similar threats across the network.
- Prevent future attacks
Sandboxing provides a virtual environment for security experts to study new threats, observe how hosts are infected, and integrate the research results into future threat defense.
Differences Between Cloud-based Sandboxing and Appliance-based Sandboxing
Based on deployment modes, there are two types of sandbox setups: appliance-based sandboxing and cloud-based sandboxing. However, the two types of sandboxing offer the same functions, that is, both can isolate and test undetected programs or unknown threats.
- Appliance-based sandboxing
Appliance-based sandboxing is deployed on a physical server and can examine suspicious files, URLs, and code on physical devices. This, however, could pose a challenge to large enterprises or enterprises with numerous remote office personnel, because once their endpoints are disconnected from the intranet, they are no longer protected by the sandbox. Another challenge is the huge costs on the purchase, management, and maintenance of physical devices. In this sense, cloud-based sandboxing is a more economical option. Appliance-based sandboxing is used for independent government and enterprise campus networks or customers requiring that data be transmitted only within a site.
- Cloud-based sandboxing
Cloud-based sandboxing is conducted in the cloud instead of using physical devices. It detects malicious files or software without affecting any other physical devices on the cloud and intranet. In addition, it protects all devices on the enterprise network regardless of their locations. This means that remote office personnel can also be protected. Cloud-based sandboxing does not require physical servers, greatly saving costs on purchasing, managing, and maintaining physical servers. In addition, cloud-based sandboxing can be used only when customers give permission to send files to the cloud sandbox.
Sandboxing Practice: Huawei FireHunter6000 Series
Huawei FireHunter6000 series is a detection system for next-generation APTs, accurately identifying unknown malicious files. FireHunter6000 directly restores network traffic, extracts files from the traffic or does that based on next-generation firewalls (NGFWs), and analyzes the files in the virtualized environment to detect unknown malicious files.
FireHunter6000 contains a unique Advanced Detection Engine (ADE) and works with NGFWs. Through cloud-based and local technologies, such as reputation scanning and real-time behavior analysis, FireHunter6000 collects and analyzes the static and dynamic behaviors of the software, detects and blocks gray traffic, and displays traffic reports in real time. This effectively prevents the spread of unknown threats and losses of core information assets in enterprises. The sandbox is especially applicable to finance and government agencies, energy providers, and high-tech organizations.
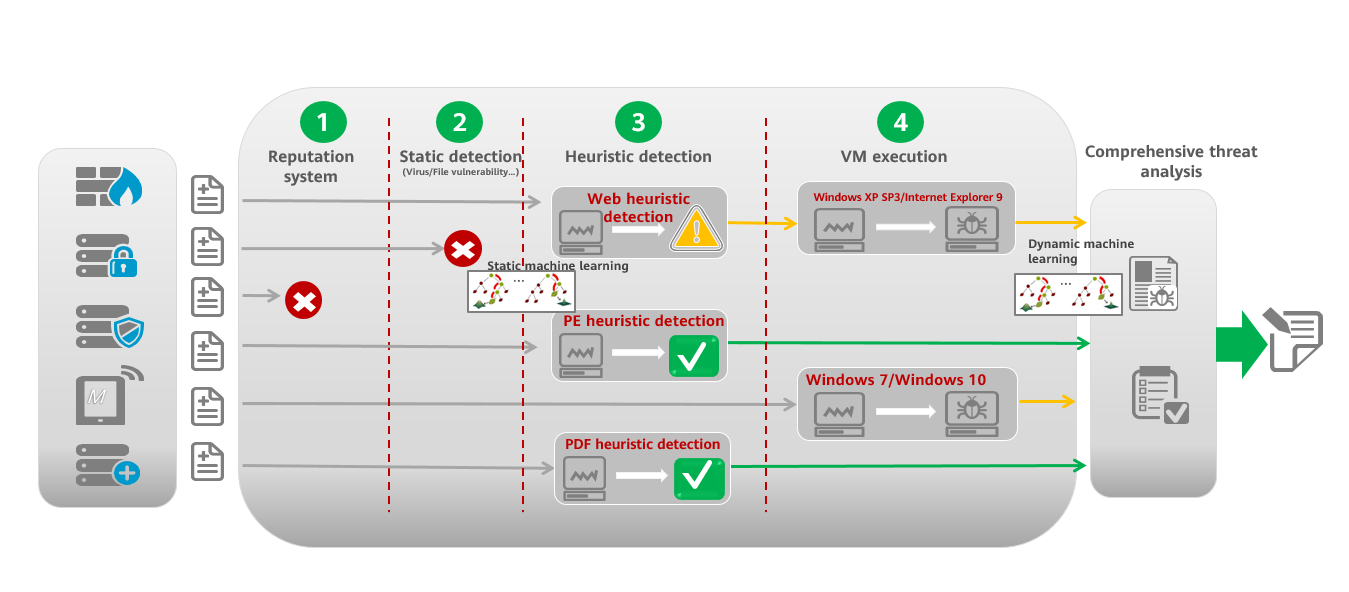
Figure 1-3 shows the technical principles of the ADE in FireHunter.
The file detection process includes reputation system scoring, static detection, heuristic detection, and VM execution. The comprehensive threat analysis engine then performs correlation analysis on the detection results and conducts threat determination to present the final threat detection result. Sandboxing is used during heuristic detection and VM execution. Using the in-depth Windows behavior analysis sandbox based on the Euler+Wine virtual environment, the ADE can dynamically execute and analyze samples in the following ways:
- Deeply parses basic file information and detects abnormal formats and information.
- Dynamically performs detection to extract key behavior data of files, such as key API functions, malicious operations, and abnormal communications.
- Monitors the key dynamic memory applied for and released during the running of malware in a timely manner, and mines malicious IOC and malicious code information.
- Monitors dynamic behavior data during file running, including process operations, file operations, and network operations.
- Implements anti-evasion by detecting various mainstream evasion methods, such as operating system evasion, time evasion, registry evasion, debugging evasion, and network evasion, to properly trigger malicious behaviors of malware.
- Monitors all Windows API calls in a fine-grained way to provide rich data and better detection effect.
Compared with manual behavior signature extraction, behavior signature extraction based on FireHunter6000 significantly improves the virus detection rate with the help of the in-depth Windows behavior analysis sandbox and AI-powered dynamic behavior detection.
- Author: Zhu Simiao
- Updated on: 2023-12-13
- Views: 663
- Average rating: