What Is a Watering Hole Attack?
A watering hole attack is a network attack technique. Its name is derived from predators in the natural world, who wait near watering holes for an opportunity to attack their prey when they are most vulnerable. Attackers conduct early investigations and employ social engineering tactics to identify websites frequently visited by their target victims (usually a particular group), and then deploy malicious programs on those websites. When the victims access the compromised websites, they become infected with the malware.
In general, the purpose of a watering hole attack is to infect the victim's computer to obtain access to the victim's company network. Compared with other social engineering attacks (such as phishing), watering hole attacks are more difficult to detect because they exploit legitimate websites that are not blacklisted. Due to the high level of trust in these websites, visitors may lower their guard and therefore be more vulnerable to such an attack.
Watering Hole Attack Mechanism
A watering hole attack consists of the following four phases:
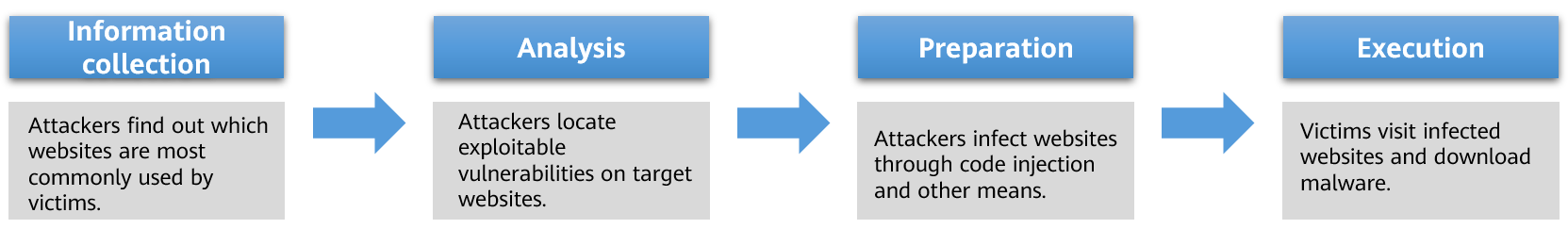
Four phases of a watering hole attack
- Information collection
In the information collection phase, attackers profile their target victim groups, collect information, and find out which websites are most commonly used by victims. The profile information includes public information from search engines or victims' social media home pages, as well as information obtained by illegal means (such as social engineering, spyware, and keyloggers). Attackers typically target websites that have weaker security measures, such as small- and medium-sized websites, or those lacking adequate technological and financial support. Large websites pay significant attention to network security, deploying a large number of professional security devices and hiring many professional network security engineers to maintain the network. This drastically increases the cost of launching such attacks.
- Analysis
After selecting target websites, attackers often analyze these websites to find vulnerabilities in domain names and subdomain names that they can further exploit. Zero-day vulnerabilities are security vulnerabilities that have not yet been patched and can be easily exploited by attackers. Attackers who discover these vulnerabilities can easily infiltrate a network even if it has the most stringent network protection measures.
- Preparation
In the preparation phase, attackers use a range of tactics — such as code injection or DNS spoofing — to infect websites and change the execution process or target website address of the websites. Attackers may either redirect victims to a fake website that has been infected with malware, or embed malware into the original web page through drive-by downloads, leading to victims downloading and installing the malware without being aware.
- Execution
Once the websites have been infected, attackers can wait for victims to fall into the trap. When victims visit the infected websites, the browser automatically downloads malware from these websites, which then infiltrates the victims' computers. Attackers typically use remote access Trojans (RATs) as their malware of choice. This type of malware gives the attacker remote control of the user's computer and access to sensitive personal data, including personal and account information. Additionally, the attacker can use the compromised computer as a stepping-stone to gain further access to the user's enterprise network.
Common Tactics of a Watering Hole Attack
Attackers use various techniques to infect websites when carrying out watering hole attacks. The following describes common techniques employed in such attacks, along with corresponding countermeasures.
Cross-Site Scripting
Cross-Site Scripting (XSS) attacks are a type of injection attack, whereby attackers exploit XSS vulnerabilities to steal cookies, hijack sessions, inject malicious HTML or JavaScript code into pages, or redirect victims to a malicious website built by the attackers. XSS vulnerabilities are primarily caused by website developers failing to properly filter special characters in user-entered text before inserting them into HTML. This creates an opportunity for attackers to submit malicious code. To reduce the risk of XSS vulnerabilities, exercise caution when using HTML escape characters during development.
SQL Injection
SQL injection is a serious security vulnerability that attackers exploit by sending malicious SQL query statements to the database server through web applications that do not properly filter user-entered data. These malicious query statements can enable attackers to perform malicious operations, including data deletion, modification, or reading, and even take control of affected applications. To prevent SQL injection, it is essential to use parameterized queries, check and filter input data, apply the principle of least privilege, and conduct regular security checks and updates.
DNS Spoofing
In a DNS spoofing attack, an attacker pretends to be the victim's DNS server to hijack the DNS request sent from a web browser to a website, and direct the victim to a different website. There are two methods for changing the DNS settings of a user: brute force cracking and system vulnerability exploitation. Compared to other types of attacks, DNS spoofing is more challenging to detect as most victims are unable to directly identify any tampering with their DNS servers. Rather, the attack can only be detected when the consequences of forged web pages become apparent when carrying out operations. For this reason, to prevent DNS spoofing, it is vital to improve security awareness, use the DNS server of the latest version, install patches in a timely manner, and use the intrusion prevention and detection system.
Drive-by Download
Through a drive-by download, an attacker embeds malware into the interface of a legitimate website to trick the victim into downloading the malware to their computer without any knowledge or consent. The attacker can then use the malware to further infect other computers in the user's organization. Typical ways for attackers to perform drive-by downloads include installing malicious plug-ins or writing shellcode to memory. Because the attack target of a drive-by download is usually an outdated system or software service, continuous update of the system and software version can reduce the risk of drive-by downloads.
Malvertising
Malvertising is often used by attackers to spread malware. When a user intentionally or unintentionally clicks on a malicious advertisement on a web page, they may download malware or be redirected to a malicious website. To prevent malvertising, you need to install antivirus software and ad blockers that prevent access to unknown websites. In addition, you need to regularly update the browser and operating system.
Zero-day vulnerabilities are security vulnerabilities that have not yet been patched, while zero-day attacks are network attacks that exploit these vulnerabilities in system or software applications. Because victims have almost no defense against zero-day attacks, such attacks can be extremely destructive. Attackers often use automatic test tools and reverse engineering technologies to search for these vulnerabilities, and subsequently bypass strict network protection measures, infiltrate the network, and launch zero-day attacks. While it is difficult to defend against zero-day attacks, building a comprehensive defense system and improving personnel's awareness can effectively reduce the probability of such attacks and minimize the resulting losses.
Infamous Watering Hole Attacks
Watering hole attacks are not the most common form of social engineering attacks, but they have a high success rate and can cause significant damage once successful. In recent years, several infamous watering hole attacks have occurred, including:
NotPetya Attack
In 2017, an attacker infected a government website in a country, causing users to unknowingly download the NotPetya malware. The malware rapidly spread throughout the country's network, resulting in huge losses amassing to approximately US$10 billion as it wiped all content from victims' hard drives.
CCleaner Attack
In 2017, a company's website was infiltrated by an attacker who concealed malware within the installation file of the company's software product, CCleaner. The modified installation file containing the malware was subsequently downloaded by 2.27 million CCleaner customers worldwide.
Adobe Flash Watering Hole Attack
In 2019, attackers placed watering hole traps on several charity websites. When a victim accessed these infected websites, a fake Adobe Flash download window popped up. Once the malware was downloaded, a backdoor was installed on the victim's computer, allowing the attacker to remotely control the computer, modify files, and access personal and computer activity data.
How Do We Prevent Watering Hole Attacks?
The best way to defend against a watering hole attack is to prevent the attack from occurring in the first place.
For organizations, the following measures can be taken:
- Strengthen network security management: Organizations should establish a comprehensive network security system and take appropriate security measures to prevent watering hole attacks. This includes deploying firewalls, implementing access control, and regularly updating software and operating systems. Additionally, it is recommended that organizations conduct regular security tests to ensure that their existing security measures can properly defend against a range of network attacks.
- Educate employees: Organizations should educate and train their employees on watering hole attacks. This helps employees understand such attacks, and how to identify and avoid falling into traps. Improving employees' security awareness also helps reduce the probability that they browse insecure web pages and lowers the risk of downloading malware from web pages.
- Back up data: Organizations should back up data regularly to ensure that data can be easily restored in the event of data loss or damage.
For individuals, it is crucial to regularly update their operating system and software, as well as install antivirus software and endpoint detection and response (EDR) software on their personal devices. This ensures that vulnerabilities and defects are promptly addressed, and their computers are safeguarded against viruses and malware attacks.
How Does Huawei Help Protect Against Watering Hole Attacks?
Huawei's products and solutions are designed to assist you in mitigating watering hole attacks.
- HiSec Solution
The HiSec solution makes threat detection, threat response, and security O&M more intelligent, improving threat defense capabilities and security O&M efficiency. The zero-trust solution continuously monitors security risks associated with endpoints and users, automatically rejects all traffic without specific permissions, and continuously authenticates and authorizes each device, user, and network flow. Taking a zero trust approach for all external traffic is an important measure for preventing watering hole attacks and gaining insight into attack signs in advance.
- HiSec Insight Security Situational Awareness System
HiSec Insight uses big data platform technologies and intelligent detection algorithms to perform multi-dimensional correlation analysis on masses of data, enabling real-time detection of various security threat events and complete restoration of the entire kill chain. It also provides a comprehensive view of the network security situation. What's more, HiSec Insight supports behavior analysis technologies, which can detect security vulnerabilities that can be exploited by watering hole attacks by comparing individual behavior patterns with standard behavior patterns.
- FireHunter6000 Series Sandbox
The FireHunter series sandboxes use the multi-engine virtualized detection technology and traditional security detection technology to identify malicious files and C&C attacks transmitted on the network. In doing so, it effectively prevents the spread of unknown threats and the loss of enterprise core information assets.
- HiSecEngine USG6000E/6000F Series AI Firewalls
The USG series AI firewalls implement strict inbound and outbound traffic control, safeguarding networks against both internal and external threats. With advanced features such as application identification, intrusion prevention, and antivirus, these firewalls are highly effective at thwarting watering hole attacks. In addition, they can promptly access the latest threat intelligence, accurately detect and counter vulnerability-specific attacks, and provide robust protection against web-based threats such as SQL injection and XSS attacks.
- Author: Zhu Simiao
- Updated on: 2023-07-27
- Views: 1213
- Average rating:







