What Is a Security Policy
A security policy is a set of rules used to protect a network. An administrator can configure security policies in the system to control network access behavior, protect a specific network against attacks from an "untrusted" network, and allow legitimate communication between two networks. The security policy is the core security function of a device. It checks the data flows passing through the device, permits legitimate traffic that complies with the security policy, and blocks illegitimate traffic to ensure network security through access control.
How do I Create a Security Policy?
A security policy consists of match conditions and actions. After receiving a packet, a device matches the packet attributes against the match conditions of the security policy. If all conditions are matched, the packet successfully matches the security policy, and the device processes the packet and subsequent bidirectional traffic according to the action defined in the security policy. As such, you need to set appropriate match conditions and the corresponding actions during the creation of a security policy.
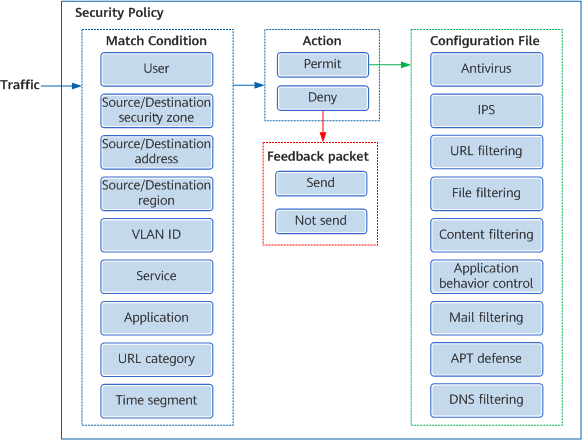
Composition of a security policy
Match Conditions
The match conditions of a security policy describe traffic characteristics which are used to filter traffic. A security policy includes the following match conditions:
- Who: indicates the user who sends the traffic.
- Where: indicates the traffic source and destination, including the source/destination security zone, source/destination IP address, source/destination region, and VLAN.
- What: indicates the service, application, or URL category to be accessed.
- When: indicates the time segment.
In a security policy, match conditions are optional and can be selected based on the network scenario. More specific match conditions in a security policy will more accurately filter the traffic. You can use only the source/destination IP address, source/destination port number, and protocol as the match condition, or use the application and user identification capabilities to more accurately and conveniently configure security policies.
Action
A security policy has two basic actions — permit and deny — to determine whether traffic is allowed to pass through.
Match conditions such as users, terminals, time segments, addresses, regions, services, applications, and URL categories, as well as various profiles required for content security checks exist as objects on a device. You can create an object and then reference it in multiple security policies.
Configuration File
If the action of the matched security policy is permit, you can use the configuration file to further perform a content security check on the traffic.
Content security check functions include antivirus, IPS, URL filtering, file blocking, content filtering, application behavior control, mail filtering, APT defense, and DNS filtering. Each content security check has its own application scenarios and actions. How the device processes traffic is determined by the results of all content security checks.
Feedback Packet
If the action of the matched security policy is deny, you can choose to send feedback packets to the server or client to quickly terminate the session, thereby reducing system resource consumption.
How Does a Security Policy Work?
You can create multiple security policies on a device to permit or block different service flows. The matching rules and filtering mechanism for multiple security policies are as follows.
Rules of Matching Against Security Policies
Each security policy contains multiple match conditions, and the relationship between them is AND. Traffic matches a security policy only when it matches all conditions. If multiple values are configured in a match condition, they are in the OR relationship, wherein traffic matches the condition as long as it matches any one value.
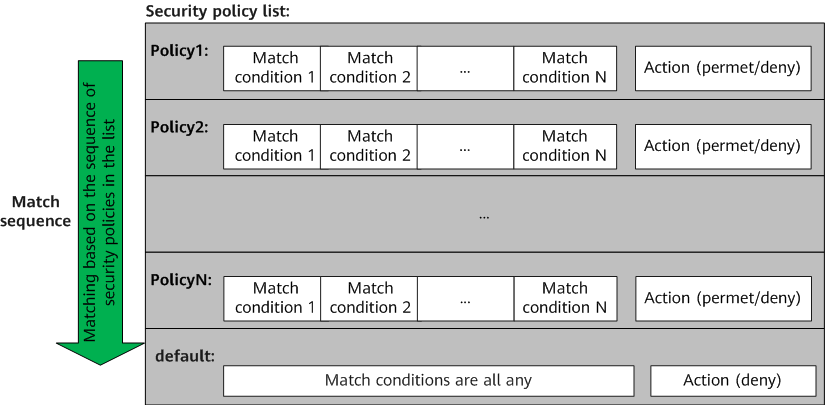
Rules of matching against security policies
When multiple security policies are configured, they are listed by configuration sequence by default. The security policy configured earlier is displayed in the upper part of the list and has a higher priority. The device matches traffic against security policies one by one from the top of the policy list until a matched security policy is found. As such, the sequence of configuring security policies is important. You need to configure policies with the more specific conditions before those with general conditions. If a specific security policy is placed after a general security policy, it may never be matched.
For example, to allow all PCs excluding two temporary ones (10.2.1.1 and 10.2.1.2) on subnet 10.2.1.0/24 to access the FTP server with an IP address of 10.1.1.1, you need to configure security policies in the following sequence.
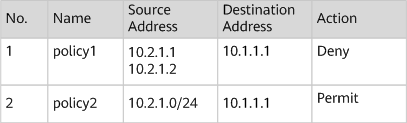
Example for configuring the sequence of security policies
Of these two security policies, policy1 has more specific conditions than policy2. However, if policy2 is configured first, policy1 will never be matched. As a result, the two temporary PCs (10.2.1.1 and 10.2.1.2) can still access the FTP server.
Security Policy Filtering Mechanism
For the same data flow, you only need to configure a security policy for traffic on the forward path (that is, in the direction in which access is initiated); no security policy is required for traffic on the return path. That is, a session entry is created after the first packet matches the security policy. Subsequent packets will then match the session entry without matching the security policy, improving service processing efficiency.
The following uses the access from a client PC to the web server as an example to describe the filtering mechanism of security policies.
- First packet process: When the request packet sent from the client PC to the web server reaches the device, the device matches the packet against the security policy. If a match entry exists, the device allows the packet to pass through. At the same time, a session, which contains the information about the packet sent by the client PC, is established.
- Subsequent packet process: Upon receipt of a response packet sent by the web server, the device searches the session table. If the information in the packet matches that in the session table and complies with the definition of subsequent packets in the protocol specifications, the packet is considered a subsequent response packet for the PC to access the web server and therefore is allowed to pass through.
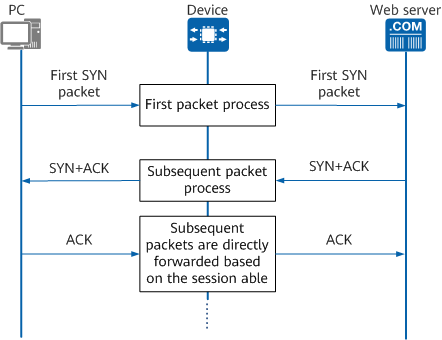
Client PC accessing a web server
How Do I Configure a Security Policy for NAT?
NAT is classified as source NAT, destination NAT, or bidirectional NAT based on the address translation mode.
- Source NAT: translates the source IP address of a packet.
- Destination NAT: translates the destination IP address of a packet.
- Bidirectional NAT: translates both the source and destination IP addresses of a packet.
The following figure shows the sequence for processing security policies and NAT on a device.
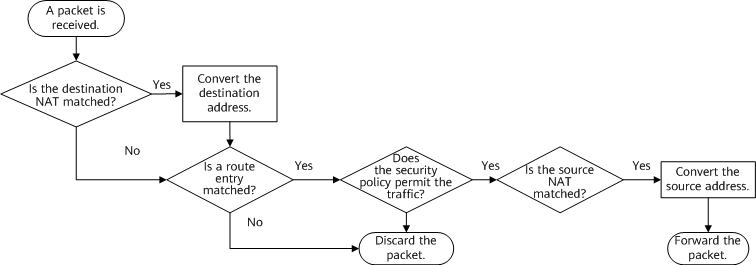
NAT service process
According to the NAT service process:
- As destination NAT is performed before a security policy check, the destination address in the security policy must be set to the post-NAT address.
- As source NAT is performed after a security policy check, the source address in the security policy must be set to the pre-NAT address.
What Is a Good Security Policy?
Services demand faster connections from networks, whereas the increasingly active cybercrime has evolved into service threats. Managing and planning high-quality security policies not only helps to strike a balance between performance and security, but also facilitates subsequent management and maintenance.
Establishing a Standard Security Policy Management Process
The security policy management process is a part of the information security policy and is designed to ensure that technology serves the service. As the security policy list of devices becomes increasingly large and management continues to grow in complexity, the organization needs to establish a process for reviewing and testing all policy applications. Pay attention to the following aspects:
- The applicant of the service party initiates a request for adding a security policy. The business director evaluates the necessity of the security policy and submits it to the security team.
- The security team evaluates the risks associated with the application submitted by the service party and determines the specific security policy implementation solution.
- The security policy is deployed and verified to ensure that it can meet the requirements.
- All security policies must be recorded. The security team can then view the records to understand the intent of each security policy and establish an association between the security policy and the application process.
Complying with Proper Security Policy Planning Principles
- Divide a network into security zones.
- Adhere to the minimum authorization principle.
- The policy sequence is very important. Commonly used and accurate policies should take priority.
- Identify and control both incoming and outgoing traffic.
- Periodically audit and optimize security policies.
- Author: Feng Yuanyuan
- Updated on: 2023-07-04
- Views: 7135
- Average rating:







