What Is GRE?
Generic Routing Encapsulation (GRE) is a tunneling technology that encapsulates data packets of one network protocol with another network protocol, so that the encapsulated packets can be transmitted using the latter network layer protocol. It provides a way to implement VPN.
Why Do We Need GRE?
GRE is a tunneling technology that defines how to encapsulate data packets of one network protocol with another network protocol, so that the encapsulated data packets can be transmitted using the latter network layer protocol.
For packet transmission, a backbone network generally uses a single network protocol, such as IPv4, whereas non-backbone networks may use other protocols, such as IPv6 and Internet Packet Exchange (IPX). If the backbone and non-backbone networks use different protocols, they cannot exchange packets. GRE resolves this issue by encapsulating the packets of one protocol into those of another protocol.
On the network shown in the following figure, group1 and group2 are non-backbone networks running Novell IPX, and term1 and term2 are non-backbone networks running IPv6. The backbone network runs IPv4. To transmit packets between group1 and group2 and between term1 and term2 over the backbone network, use GRE to establish a tunnel between DeviceA and DeviceB. When DeviceA receives a packet from group1 or term1, DeviceA encapsulates the packet into a GRE packet. The GRE packet is then encapsulated into an IPv4 packet for forwarding.
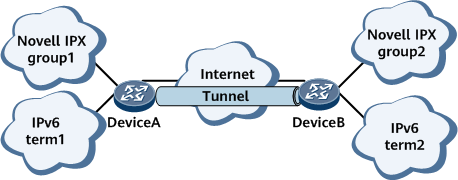
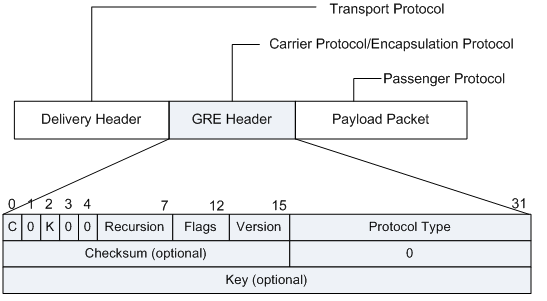
GRE networking
How Does GRE Work?
Upon receiving a packet (such as an IPX packet) that needs to be encapsulated and routed, a device adds a GRE header to it and then encapsulates it with another protocol, such as IP. After that, IP is responsible for forwarding the packet. The following figure shows the encapsulated packet format.
- Payload Packet: is received by the system and needs to be encapsulated and routed.
- Passenger Protocol: is used by the packet before encapsulation.
- Encapsulation Protocol: is used to encapsulate the passenger protocol packet. It is also called the carrier protocol.
- Transport Protocol (Delivery Protocol): is used to transmit the encapsulated packet.
The following table describes each field in the GRE header.
Field |
Length |
Description |
|---|---|---|
C |
1 bit |
Checksum bit. If it is set to 1, the Checksum field is present in the GRE header; if it is set to 0, the GRE header does not contain the Checksum field. |
K |
1 bit |
Key bit. If it is set to 1, the Key field is present in the GRE header; if it is set to 0, the GRE header does not contain the Key field. |
Recursion |
3 bits |
Number of times that a packet is encapsulated by GRE. The value of this field increments by 1 each time the packet is encapsulated. If the packet is encapsulated more than three times, it is discarded. This field prevents a packet from being encapsulated infinitely. |
Flags |
5 bits |
Reserved field. Currently, this field must be set to 0. |
Version |
3 bits |
Version field, which must be set to 0. Version 1 is used by PPTP as defined in RFC 2637. |
Protocol Type |
16 bits |
Type of the passenger protocol. |
Checksum |
16 bits |
Checksum of the GRE header and the payload. |
Key |
31 bits |
Key field used to authenticate the packet at the receive end. |
The transmission of packets over a GRE tunnel can be divided into two phases: encapsulation and decapsulation. As shown in the following figure, a private network packet from the ingress PE to the egress PE is encapsulated on the ingress PE and decapsulated on the egress PE.
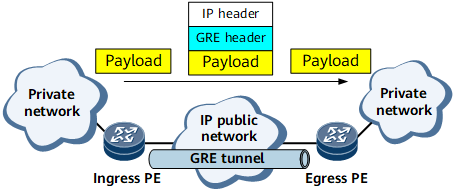
Communication between private networks over a GRE tunnel
The encapsulation and decapsulation process is as follows:
- Upon receipt of a packet, the ingress PE forwards it for processing by the passenger protocol. This protocol determines that the outbound interface is a GRE tunnel interface.
- The ingress PE sends the packet to the corresponding tunnel interface and adds a GRE header to the packet.
- The ingress PE adds an IP header containing the source and destination addresses to the packet based on the configuration.
- The ingress PE searches the public network routing table for the outbound interface based on the destination address in the IP header and then sends the packet to the outbound interface.
- Upon receipt of the packet, the egress PE analyzes the IP header and finds that the destination is itself.
- The egress PE removes the IP header and GRE header.
- The egress PE determines that the passenger protocol of the packet is a protocol running on a private network and forwards the packet to that private network for processing. The private network then forwards the packet accordingly.
Application of GRE on a Network
Enlarging the Operation Scope of a Network with Limited Hops
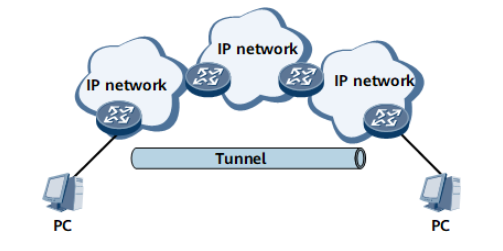
Enlarging the network operation scope
IP runs on the network shown in the preceding figure. Assume that IP limits the hop count to 255. The two PCs cannot communicate if the hop count between them exceeds 255. Some hops can be hidden (therefore reducing the hop count between the PCs) by using a tunnel. This makes it possible to enlarge the network operation scope.
Connecting Discontinuous Sub-networks to Establish a VPN
GRE tunnels can be used to connect discontinuous sub-networks to establish a VPN across a WAN.
For example, two VPN sub-networks, site 1 and site 2, are in two different cities. By setting up a GRE tunnel between their PEs, you can connect the two sub-networks to establish a continuous VPN.
GRE, which applies to both L2VPNs and L3VPNs, can be used in either CPE-based or network-based VPN scenarios:
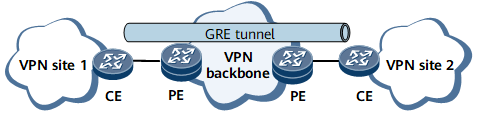
- In a CPE-based VPN scenario, both ends of a GRE tunnel reside on CEs, as shown in the following figure.
GRE in a CPE-based VPN scenarioIn this mode, the CE refers to the customer premises equipment (CPE).
- In a network-based VPN scenario, both ends of a GRE tunnel reside on PEs, as shown in the following figure.
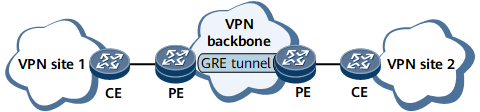
GRE in a network-based VPN scenario
Generally, the VPN backbone network uses LSPs as public network tunnels. However, LSPs cannot be used as public network tunnels if the core devices (Ps) on the backbone network provide only the IP function and the PEs at the network edge provide MPLS functions. In this case, you can use GRE tunnels instead of LSPs in an L3VPN or L2VPN solution provided for the backbone network. The following figure shows the format of a private network packet transmitted on the VPN backbone network.
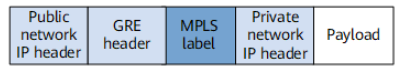
Format of a GRE packet containing an MPLS label
GRE tunnels can also be used as non-MPLS VPN backbone network tunnels. In this case, a GRE packet cannot contain any MPLS label when being transmitted on the VPN backbone network. The following figure shows the format of such a packet.
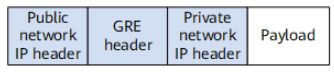
Format of a GRE packet without any MPLS label
Connecting a CE to an MPLS VPN over a GRE Tunnel
To connect a CE to an MPLS VPN, a physical link is generally used to directly connect the CE to a PE on the MPLS backbone network. Specifically, the CE and PE must be on the same network. In this networking, the VPN must be associated with the corresponding physical interface used by the PE to connect to the CE.
In some cases, however, it is not possible to directly connect CEs and PEs over physical links, as shown in the following figure. For example, for multiple organizations that connect to the Internet or IP backbone network, their CEs and PEs are geographically dispersed and cannot directly access the PEs on the MPLS backbone network. These organizations cannot directly access the sites inside the MPLS VPN through the Internet or IP backbone network.
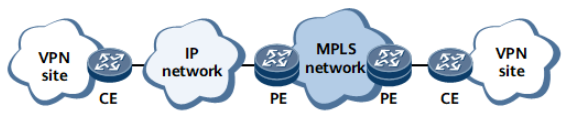
CEs accessing an MPLS VPN backbone network through an IP backbone network
To connect a CE to the MPLS VPN and ensure data transmission security, connect the CE to a PE on the MPLS backbone network over the public network or a private network and establish a GRE tunnel between the CE and PE. Because the GRE tunnel can be regarded as a physical interface, you can associate a VPN with such an interface on a PE.
There are three scenarios where a GRE tunnel is used for MPLS VPN access:
- Over a private network: The GRE tunnel is associated with a VPN instance. The source interface (or source address) and destination address of the GRE tunnel belong to this VPN instance.
- Over a public network: The GRE tunnel is associated with a VPN instance. However, the source and destination addresses of the GRE tunnel are public IP addresses and do not belong to the VPN instance.
- Over a VPN: The GRE tunnel is associated with a VPN instance (such as VPN1), but the source interface of the GRE tunnel is bound to another VPN instance (such as VPN2). The GRE tunnel traverses VPN2.
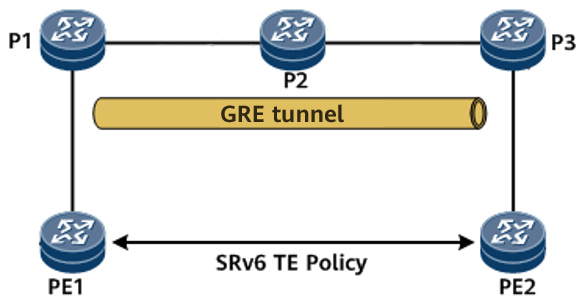
SRv6 TE Policy over GRE
In the following figure, P1, P2, and P3 do not fully support IPv6 and a bidirectional SRv6 TE Policy needs to be established between PE1 and PE2. In this case, a GRE tunnel can be established between P1 and P3, and then an SRv6 TE Policy can be established over the GRE tunnel.
Relationships Between GRE, VPN, IPsec, and L2TP
As tunneling technologies in the data communication field, VPN, IPsec, and L2TP are common protocol models used by communication devices. The three technologies complement each other in terms of performance, function coverage, and application scenarios to meet the communication requirements in various scenarios.
GRE vs. VPN
GRE can be used to implement VPN. Simply put, a VPN is a point-to-point, virtual, secure, and logical channel. Based on networking models, VPNs can be classified into virtual private dialup networks (VPDNs), virtual private routing networks (VPRN), virtual private wire services (VPWSs), and virtual private LAN services (VPLSs). A VPRN can be implemented using a conventional VPN protocol such as GRE or using MPLS. Therefore, GRE is only a mechanism for implementing VPN.
GRE vs. IPsec
Both GRE and IPsec are tunnel-related concepts. Their main difference lies in security. GRE can create an unencrypted tunnel between two networks running different protocols, whereas IPsec can create an encrypted tunnel over an IP network. IPsec uses encryption and identity authentication mechanisms to prevent eavesdropping and data tampering. Currently, IPsec can encrypt only unicast packets, not multicast packets. GRE can encapsulate multicast packets into unicast packets but cannot encrypt packets. This is why GRE is often used together with IPsec.
GRE vs. L2TP
GRE and L2TP are both tunneling protocols. Their main difference is that L2TP is a user access protocol whereas GRE is a network protocol. Therefore, L2TP involves only user-side access, and GRE involves only network-side tunnel connectivity. In addition, the packet structures of GRE and L2TP are quite different. GRE packets contain only GRE headers and tunnel payloads, whereas PPP and Ethernet frames are encapsulated into L2TP packets at the user access side.
- Author: Huang Hefei
- Updated on: 2023-12-13
- Views: 1936
- Average rating: