What Is IPsec?
Internet Protocol Security (IPsec) is a suite of protocols and services that provide security for IP networks. It is a widely used virtual private network (VPN) technology. IP packets lack effective security mechanisms and may be forged, stolen, or tampered with when being transmitted on a public network, such as the Internet. To solve this problem, the communicating parties establish an IPsec tunnel for encrypted transmission of IP packets. This ensures secure transmission of IP packets on an insecure network, such as the Internet.
What Is an IPsec VPN?
Virtual private network (VPN) is a technology for establishing a private network on a public network. It is a logical network over a public network such as the Internet, allowing user data to be transmitted through a logical link. This is different from a traditional private network, where user data is transmitted through an end-to-end physical link.
Common VPN protocols include IPsec, Secure Sockets Layer (SSL), Generic Routing Encapsulation (GRE), Point-to-Point Tunneling Protocol (PPTP), and Layer 2 Tunneling Protocol (L2TP). IPsec is a commonly used VPN technology and applies to multiple network access scenarios.
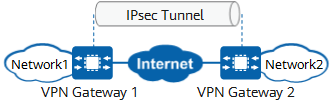
IPsec VPN is a VPN technology that uses IPsec for remote access. The technology allows establishing an IPsec tunnel between two or more private networks on a public network and using encryption and authentication algorithms to ensure the security of VPN connections.
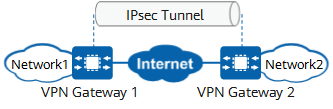
IPsec VPN protects point-to-point communication by establishing secure tunnels between hosts, between hosts and network security gateways, or between network security gateways (such as routers and firewalls). It operates at the IP layer to encrypt and authenticate data packets.
Compared with other VPN technologies, IPsec VPN is more secure because data is encrypted for transmission in IPsec tunnels. However, the configuration and networking deployment of IPsec VPN are more complex.
IPsec VPN
How Does IPsec Work?
- Interested traffic identification. After a network device receives a packet, it matches the 5-tuple of the packet against the configured IPsec policy to determine whether the packet needs to be transmitted through an IPsec tunnel. The traffic that needs to be transmitted through an IPsec tunnel is known as interested traffic.
- Security association (SA) negotiation. An SA defines elements for secure data transmission between the communicating parties. These elements include security protocols, data encapsulation modes, encryption and authentication algorithms, and keys used for data transmission.
After identifying interested traffic, the local network device initiates SA negotiation with the peer network device. In this phase, the communicating parties use the Internet Key Exchange (IKE) protocol to establish IKE SAs for identity authentication and key information exchange, and then establish IPsec SAs for secure data transmission based on the IKE SAs.
- Data transmission. After IPsec SAs are established between the communicating parties, they can transmit data over an IPsec tunnel.
To ensure data transmission security, Authentication Header (AH) or Encapsulating Security Payload (ESP) is used to encrypt and authenticate data. The encryption mechanism ensures data confidentiality and prevents data from being intercepted during transmission. The authentication mechanism ensures data integrity and reliability and prevents data from being forged or tampered with during transmission.
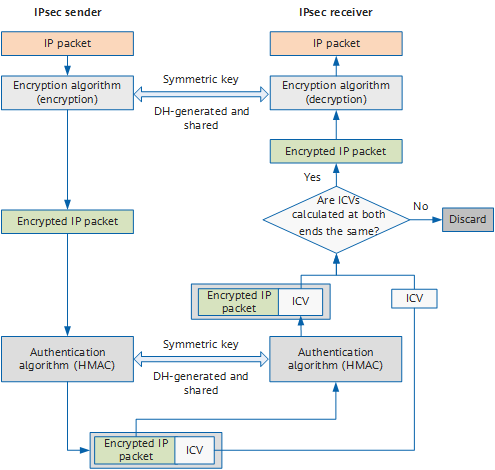
In the following figure, the IPsec sender uses the encryption algorithm and encryption key to encrypt an IP packet, that is, it encapsulates the original data. Then the sender and receiver use the same authentication algorithm and authentication key to process the encrypted packets to obtain the integrity check value (ICV). If the ICVs obtained at both ends are the same, the packet is not tampered with during transmission, and the receiver decrypts the packet. If the ICVs are different, the receiver discards the packet.
IPsec encryption and authentication process - Tunnel teardown. In most cases, session aging (session disconnection) between two communication parties indicates that data exchange between the two communication parties is complete. To save system resources, the tunnel between the two communication parties is automatically torn down when the tunnel idle timeout period is reached.
What Are the 3 Protocols in IPsec?
Internet Key Exchange (IKE)
IKE is a UDP-based application-layer protocol and is mainly used for SA negotiation and key management.
IKE has two versions: IKEv1 and IKEv2. Compared with IKEv1, IKEv2 fixes multiple acknowledged cryptographic vulnerabilities, improves security performance, simplifies the SA negotiation process, and improves the negotiation efficiency.
IKE is a hybrid protocol that combines the Internet Security Association and Key Management Protocol (ISAKMP), Oakley, and SKEME. ISAKMP defines the IKE SA establishment process. The core of Oakley and SKEME is the Diffie-Hellman (DH) algorithm, which is used to securely distribute keys and authenticate identities on the Internet for secure data transmission. The encryption key and verification key required by IKE SAs and IPsec SAs are generated and can be dynamically updated through the DH algorithm.
Authentication Header (AH)
AH is used to authenticate the data source and check the integrity of IP packets. That is, AH ensures that the source of IP packets is trusted and the data is not tampered with. AH, however, does not provide the encryption function. An AH header is appended to the standard IP header in each data packet. AH checks the integrity of the entire IP packet.
Encapsulating Security Payload (ESP)
ESP can encrypt data in addition to authenticating the data source and checking the integrity of IP packets. An ESP header is appended to the standard IP header in each data packet, and the ESP Trailer and ESP Auth data fields are appended to each data packet. ESP in transport mode does not check the integrity of IP headers. Therefore, ESP cannot ensure that IP headers are not tampered with.
AH and ESP can be used independently or together. When AH and ESP are used together, ESP encapsulation is performed before AH encapsulation, and AH decapsulation is performed before ESP decapsulation.
What Ports Are Used in IPsec?
In IPsec, the IKE protocol uses UDP port 500 to initiate and respond to negotiations. Therefore, to ensure that IKE negotiation packets can pass through a gateway, you need to configure a security policy on the gateway to permit packets with UDP port 500. In addition, in the IPsec NAT traversal scenario, packets with UDP port 4500 need to be permitted.
AH and ESP are network layer protocols and do not involve ports. To ensure successful IPsec tunnel setup, you need to configure a security policy on the gateway to enable the AH (IP protocol number 51) and ESP (IP protocol number 50) services.
IPsec VPN vs SSL VPN
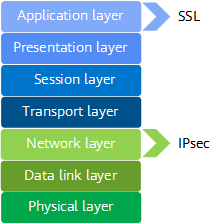
- Working layers of the OSI reference model
OSI defines a seven-layer framework for network interconnection: physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer. IPsec works at the network layer and directly runs over the Internet Protocol (IP). SSL, working at the application layer, is an application-layer protocol that encrypts HTTP traffic instead of IP packets.
Working layers of IPsec and SSL - Configuration and deployment
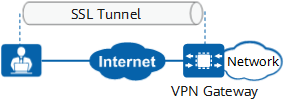
IPsec VPN is applicable to site-to-site networking. In this networking, VPN gateways must be deployed at each site, or remote users need to install dedicated VPN clients. Therefore, the configuration and deployment are complex, and the maintenance cost is high. SSL VPN is applicable to client-to-site networking. In this networking, remote users only need to install the specified plug-in on the standard SSL-supporting browser. A VPN gateway is deployed in a data center for centralized management and maintenance. Therefore, the configuration and deployment are simple, and the maintenance cost is low.
IPsec VPN
SSL VPN - Security
IPsec works at the network layer to protect all data transmitted between sites. IPsec VPN requires remote users to install a dedicated VPN client or deploy a VPN gateway at the site. User access is checked by the client or gateway in terms of user authentication rules, security policy rules, or content security filtering. Therefore, IPsec VPN is more secure. SSL VPN does not require dedicated clients or gateways at access sites. Therefore, SSL VPN is more vulnerable to security threats.
- Access control
IPsec works at the network layer and cannot implement fine-grained access control based on applications. SSL VPN is more flexible in fine-grained access control. Network administrators can classify network resources into different types based on application types. Each type of resources has different access permissions.
- Author: Xi Youyuan
- Updated on: 2024-01-10
- Views: 38235
- Average rating: