What Is a VPN?
A virtual private network (VPN) is a virtual private communication network established over a public network by an Internet service provider (ISP) or network service provider (NSP). It meets enterprises' requirements for network flexibility, security, cost effectiveness, scalability, and more.
Why Do We Need a VPN?
Background
The use of IT technologies in modern enterprise business operations is on the rise. For example, these technologies are being applied to enterprise resource planning, voice over IP (VoIP), video conferencing, and remote training. By leveraging IT technologies, enterprises can achieve office automation and access information more efficiently. And as the Internet economy develops, enterprises expand into new locations, cooperate with an increasing number of partners, and demand greater office mobility. As a result, these enterprises need to connect their headquarters and branches through carrier networks to form enterprise networks, allowing staff to easily access these networks from outside of office buildings.
During the initial stages, telecom carriers used leased lines to provide Layer 2 connections for enterprises. However, leased lines come with the following drawbacks:
Long construction time
High prices
Difficult management
After the emergence of asynchronous transfer mode (ATM) and frame relay (FR) technologies, telecom carriers began using virtual circuits (VCs) to provide point-to-point (P2P) Layer 2 connections for clients. This allowed clients to establish Layer 3 networks and transmit IP and other data over the P2P Layer 2 connections. Compared with leased lines, VCs are more cost-effective and can be established in a shorter period of time. Moreover, VCs allow users from different private networks to share the same carrier network.
The drawbacks of such traditional private networks are as follows:
VCs rely on media such as ATM or FR, which means that carriers need to build ATM or FR networks covering all service areas in order to offer VPN services based on these technologies. This can result in significant network construction costs.
ATM or FR networks cannot provide the speed required by Internet applications.
The deployment of ATM or FR networks is a complex process. When a new site is added to an existing ATM or FR network, the configurations of all edge nodes that connect to the site need to be modified.
While traditional private networks can help boost enterprise profits, they often fall short in terms of flexibility, security, economy, and scalability. To address these issues, VPNs — simulated private networks carried over IP networks — have been introduced as a substitute for traditional private networks.
VPNs are virtual private communication channels established over public networks by Internet service providers (ISPs) or network service providers (NSPs).
Characteristics
A VPN has the following two basic characteristics:
Private: It provides the same private network experience as a traditional private network, ensuring that VPN resources remain completely independent of the underlying transport network resources. This means that the resources of a VPN are exclusively reserved for users who belong to the VPN, and the security of the VPN can be fully guaranteed to protect internal information from external interference.
Virtual: Users within a VPN communicate with each other over a public network that is also accessible to non-VPN users. A VPN is essentially a logical private network, and the underlying public network is referred to as a VPN backbone network.
Leveraging these two characteristics, an IP network can be partitioned into multiple logically isolated networks, which can be applied in a wide range of scenarios. For example, they can be used to solve interconnection issues within an enterprise (such as interconnecting different departments), or they can be used to provide new services (such as creating a VPN specifically for IP telephony) to address issues related to IP address shortage, QoS guarantee, and the development of new value-added services.
Benefits
Compared with traditional private networks, VPNs offer the following benefits to users:
Enhanced security: Secure connections are established between the headquarters and remote workers, branches, partners, or suppliers to ensure confidentiality. This is especially crucial for e-commerce and the integration of financial networks with communication networks.
Improved cost-effectiveness: VPNs leverage the public network for data transmission, enabling businesses to establish connections with remote offices, remote workers, and business partners at lower costs.
Support for mobile services: VPN users can access the network anytime and anywhere, meeting the growing demand for mobile services.
QoS guarantee: A QoS-capable VPN, such as a Multiprotocol Label Switching (MPLS) VPN, can provide varying levels of QoS guarantee.
VPNs offer the following benefits to carriers:
Enhanced operations: VPNs can enhance network resource utilization, increasing profits for ISPs.
Flexible configuration: Carriers can easily add or remove VPN users through software configuration, without the need for any hardware modifications.
Multi-service support: In addition to providing basic VPN interconnection services, SPs can also provide advanced services, such as network outsourcing, service outsourcing, and customized services.
VPNs enable enterprises to focus less on network operations and maintenance and more on achieving their business goals. This feature has made VPNs increasingly popular among enterprises. With VPNs, a carrier can use a single network to provide multiple types of services — including best-effort IP forwarding, VPN, traffic engineering, and differentiated services (DiffServ), reducing network construction, maintenance, and operation costs.
In summary, VPNs are secure, reliable, easy to manage, and highly scalable and flexible. Users can use VPN services as long as they have Internet access, regardless of their locations.
How Are VPNs Classified?
With the development of network technologies, numerous VPN technologies have emerged and gained widespread adoption. VPNs can be categorized into various types from different perspectives.
Service Application
VPNs are classified as follows based on service applications:
Intranet VPN
An intranet VPN serves as an extension or alternative to traditional private networks or enterprise networks, connecting distribution points within an enterprise over a public network.
An intranet VPN is a secure network that connects an enterprise's headquarters, branches, regional offices, and remote workers over a public network. VPNs are commonly used by banks and governments to construct their intranets.
Chain businesses, including chain stores, storage and logistics companies, and gas stations, are typical examples of enterprises that utilize intranet VPNs.
Extranet VPN
An extranet VPN expands the accessibility of specific resources from an enterprise network to external users, including suppliers, business partners, and customers. These VPNs are established over the public network between enterprises that share common interests.
Establishing an extranet through traditional private lines involves complex network management and access control, and may even entail the installation of compatible user-side network devices. Although an extranet can be set up in dial-up mode, doing so is a complicated process as configurations for different extranet users must be performed separately. Furthermore, constructing and maintaining such an extranet is costly, particularly if users connecting to it are dispersed over a wide area. Consequently, many enterprises began abandoning the use of extranets, resulting in complex and inefficient business processes between enterprises.
An extranet VPN resolves the preceding issues for it is easy to construct and manage. The implementation technology of an extranet VPN is the same as that of an intranet VPN. This is why enterprises today often use VPN technologies to build extranets. To ensure QoS, the intranet is not directly used for external communication by an enterprise. Furthermore, communication data between enterprises is typically sensitive, and so the extranet needs higher security than the intranet. The access privileges of extranet VPN users can be configured and managed through firewalls or other methods.
- Access VPN
An access VPN allows employees on the move, working from home, or located in small remote offices to access an enterprise's internal servers through inexpensive dial-up media. This enables them to establish private network connections with the enterprise's intranet and extranet. Access VPN connections are categorized as either client-initiated or network access server (NAS)-initiated.
Networking Model
VPNs are classified as follows based on networking models:
- VPDN
A virtual private dial-up network (VPDN) provides access services for enterprises, small ISPs, and mobile workforces.
The VPDN access scope includes the coverage areas of both the public switched telephone network (PSTN) and integrated services digital network (ISDN). Typically, a VPDN employs peer-to-peer (P2P) connections and is implemented through protocols such as Layer 2 Tunneling Protocol (L2TP) and Point-to-Point Tunneling Protocol (PPTP).
Compared with other types of VPNs, a VPDN offers higher security and more flexible authentication mechanisms and accounting modes, and supports dynamic address allocation.
- VPRN
A virtual private routing network (VPRN) connects the headquarters, branches, and remote offices through virtual network management devices. Unlike other types of VPN, a VPRN forwards data packets at the network layer. To enable this, each VPN node on the public network must establish a dedicated VPN routing and forwarding table (VRF) that contains network-layer reachability information for each VPN. These dedicated VRFs guide the forwarding of data flows between VPN nodes and between VPN nodes and user sites.
A VPRN can be implemented using a conventional VPN protocol such as Generic Routing Encapsulation (GRE) or using MPLS.
- VPWS
A virtual private wire service (VPWS), also called a virtual leased line (VLL), simulates the traditional leased line service by using an IP network to provide asymmetric and low-cost digital data network (DDN) services. From the perspective of users, such a virtual leased line is similar to a traditional leased line.
A VPWS network is compatible with traditional private networks, such as ATM and FR networks, allowing carriers to smoothly upgrade such networks to VPWS networks.
VPWS, as a virtual leased line technology, is mainly used at the access and aggregation layers. VPWS is classified into circuit cross connect (CCC), static virtual circuit (SVC), LDP, and more. PWE3, an E2E Layer 2 service transport technology, is an extension to LDP VPWS.
- VPLS
A virtual private LAN service (VPLS) is an extension of LANs over the IP public network, allowing such LANs to interwork.
A VPLS is also called a transparent LAN service (TLS). Unlike a common P2P L2VPN, a VPLS enables a service provider (SP) to offer an Ethernet-based multipoint service to users over an MPLS backbone network.
The use of Ethernet is increasingly widespread due to advantages such as flexible definition of VLANIF interfaces, high bandwidth, and low costs.
While VPRN and VPWS networks can also provide LAN services, they are subject to the following limitations of traditional Ethernet technologies:
- The broadcast storms of frames with unknown destination MAC addresses cannot be limited.
- The extension of the Spanning Tree Protocol (STP) is limited.
- The VLAN address space is limited.
VPLS technology is capable of overcoming such limitations. Unlike traditional networks, the VPLS backbone network does not need to run STP. Instead, it utilizes full-mesh connections and split horizon to eliminate routing loops. In the case of unknown unicast and multicast frames, VPLS discards, broadcasts, or locally processes these frames. As a result, VPLS can extend the coverage of VLANs to a national or even global scale.
Operational Mode and Implementation Layer
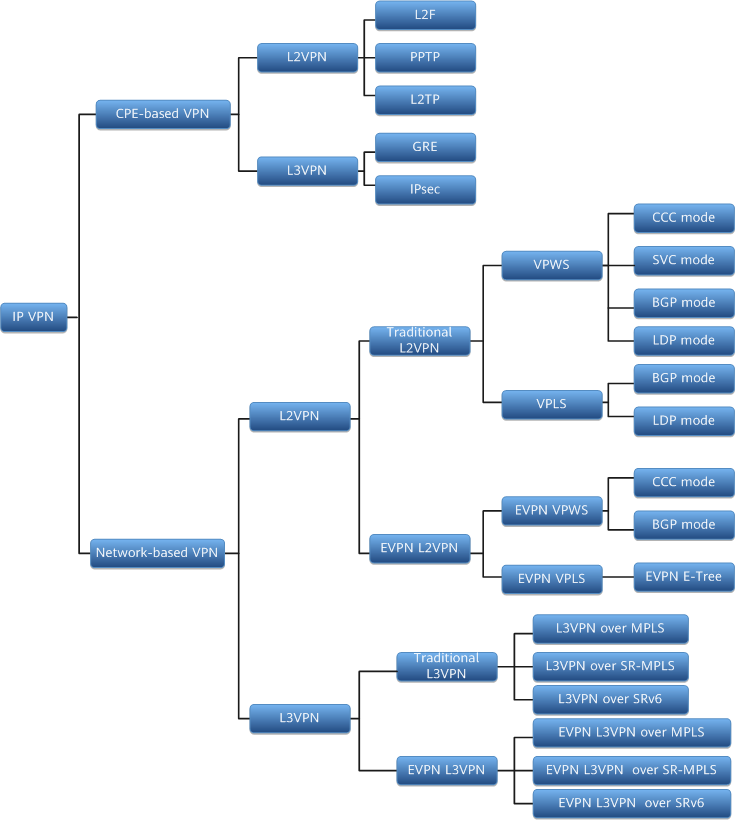
Classification based on operational modes and implementation layers
As shown in the preceding figure, VPNs can be classified as follows based on operational modes:
- CPE-based VPN
In a CPE-based VPN scenario, users are responsible for establishing, managing, and maintaining the VPN. This requires the deployment of related VPN tunneling protocols, such as GRE, L2TP, and PPTP, on user devices.
In a CPE-based VPN scenario, user-side network devices initiate requests for VPN connections, eliminating the need for special support from carriers in VPN implementation.
A CPE-based VPN is difficult to implement and offers poor service scalability, and is mainly used at the access layer.
- Network-based VPN
In a network-based VPN scenario, the ISP is responsible for establishing, managing, and maintaining the VPN, while also granting users some degree of control over the services. The network-side devices are responsible for implementing functions and features. As for the user-side network devices, they do not require any special VPN functions, needing only to support network interconnection.
This mode reduces user investment, improves service flexibility and scalability, and brings new benefits to carriers.
As shown in the preceding figure, VPNs can be classified as follows based on implementation layers:
- L2VPN
In CPE-based VPN mode, L2VPN can be of the GRE, L2TP, or PPTP type.
In network-based VPN mode, L2VPNs include traditional L2VPNs and Ethernet virtual private network (EVPN) L2VPNs, such as VPWS, VPLS, EVPN VPWS, and EVPN VPLS.
VPWS applies to large enterprise networks carried over WANs, whereas VPLS applies to small enterprise networks carried over MANs. In VPLS, PEs must obtain the MAC addresses of private network devices to prevent broadcast storms. Storing these MAC addresses consumes a significant amount of storage resources, and the protocol overhead is heavy. L2VPNs use only the Layer 2 links of SP networks, enabling them to support multiple Layer 3 protocols. While L3VPNs also support multiple Layer 3 protocols, they have more restrictions than L2VPNs.
EVPN is a next-generation full-service transport VPN solution. EVPN addresses the limitations of traditional L2VPN by enabling load balancing and minimizing network resource consumption. Additionally, EVPN has the advantages of IP VPN traffic balancing and flexible deployment to Ethernet. These advantages have made EVPN a popular choice for large-scale Layer 2 DCN interconnection scenarios.
- L3VPN
In CPE-based VPN mode, L3VPNs include GRE VPNs and IPsec VPNs.
In network-based VPN mode, L3VPNs include traditional L3VPNs and EVPN L3VPNs — such as L3VPN over MPLS, L3VPN over MPLS, L3VPN over SR-MPLS, EVPN L3VPN over MPLS, and EVPN L3VPN over SRv6. EVPN unifies the control planes of various VPN services and uses BGP extensions to transmit Layer 2 or Layer 3 reachability information. EVPN separates the forwarding plane from the control plane and is capable of transmitting L3VPN services, reducing protocol complexity.
The following figure shows the differences between L2VPNs and L3VPNs.
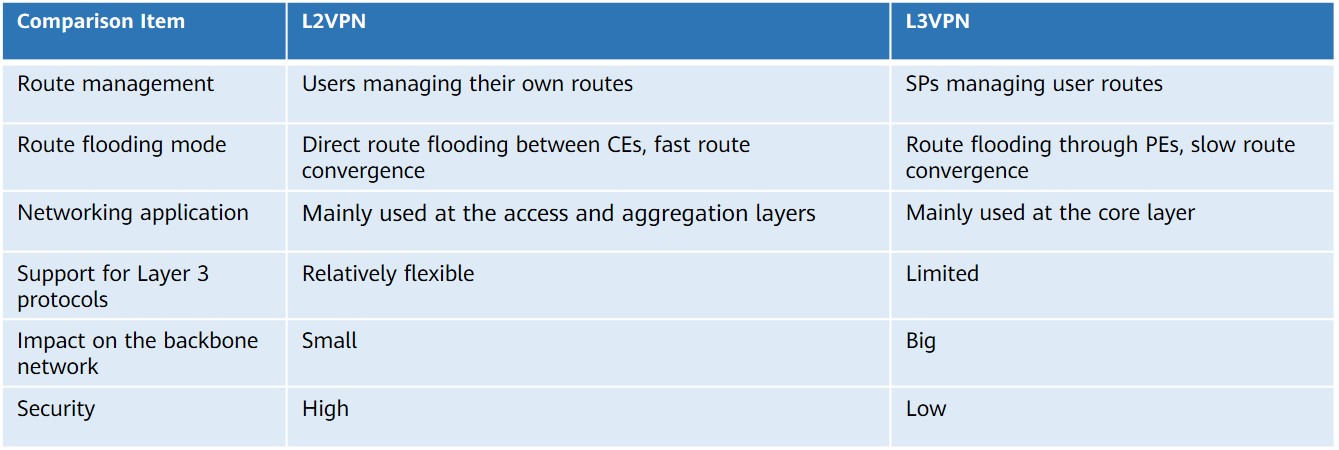
Differences between L2VPNs and L3VPNs
Network Structure
A typical VPN has the following three layers:
- Access layer
The devices at the access layer provide access services for users. These devices do not need to implement many functions, but must provide a large number of access interfaces. The MANs used in large metropolitan areas are expected to possess strong access-layer performance. Typically, a CE is dual-homed or multi-homed to access-layer nodes. Dual homing can be achieved through either physical or logical means. In physical dual homing, a CE accesses two nodes over two physical links; in logical dual homing, a CE accesses two nodes deployed in a ring topology.
- Aggregation layer
The aggregation layer has either a mesh or ring topology, depending on actual requirements.
- Backbone layer
The backbone layer must have a full-mesh topology and be capable of multi-level backup. The devices on the backbone layer are generally connected through high-speed interfaces.
How Does a VPN Work?
Fundamentals
VPNs are based on the idea of tunneling. They use various tunneling technologies to encapsulate VPN packets, so that these packets can be transparently transmitted over dedicated data transmission channels on the VPN backbone network.
Architecture
VPN technology is much more complex than P2P technology. VPN implementation requires network connections to be deployed between users and covers network topology planning, route calculation, and user joining and leaving maintenance. The VPN architecture comprises the following parts:
VPN tunnel: includes tunnel establishment and management.
VPN management: includes automatic VPN configuration and the management of VPN configurations, members, and attributes. Automatic VPN configuration refers to the establishment of a one-to-one relationship between VPN internal links in an L2VPN after information about the peer links is received by the local link. VPN attribute management refers to the management of attributes of multiple VPNs on PEs for the differentiation of VPN address spaces.
VPN signaling protocol: exchanges and shares VPN resources between CEs in a VPN. For an L2VPN, information about data links is exchanged; for an L3VPN, routing information is exchanged; for a VPDN, information about single data links is exchanged. In some scenarios, the signaling protocol is also used for VPN member discovery.
Implementation Modes
A VPN can be implemented in the following modes.
VPN Tunnel + VPN Management
In this mode, the VPN architecture comprises the following parts:
VPN tunnel establishment
VPN management, including the deployment of policies related to VPN management, accounting, and QoS
Traditional IP VPNs, such as IPsec VPNs and GRE VPNs, use this implementation mode.
Tunneling + VPN Management + VPN Signaling Protocol
In this mode, the VPN architecture comprises the following parts:
VPN tunnel establishment
VPN management, including automatic VPN configuration and the management of VPN configurations, members, and attributes
VPN signaling protocol, which is used to exchange and share VPN resources between CEs on a VPN
VPNs that adopt this implementation mode include Martini VLL, PWE3, Martini VPLS, and VPDN.
Instantiation
In instantiation mode, all VPNs are instantiated at Layer 2 and Layer 3, and instances of private forwarding information are created for them. Besides tunnel management, an instantiated VPN also involves member discovery, member management, and automatic configuration.
VPNs that use this implementation mode include traditional L3VPNs, EVPN L2VPNs, EVPN L3VPNs, and Kompella L2VPNs (including Kompella VPLS and Kompella VLL).
Working Process
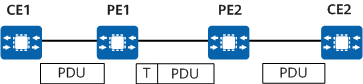
VPN working process
The basic working process of a VPN is as follows:
- CE1 sends a user packet to PE1.
- Upon receipt, PE1 transmits the packet in either encrypted or unencrypted format, according to the rules set by the network administrator.
- If the data needs encryption, PE1 encrypts the entire data packet (including the source and destination IP addresses), attaches a data signature to it, and encapsulates it with a new header (containing the tunnel label and security information). If the data does not need encryption, PE1 simply encapsulates the data packet with a new header (containing tunnel label information).
- PE1 sends the encapsulated data packet to the remote device PE2 through the public network tunnel.
- Upon receipt, PE2 checks the destination IP address of the data packet. After finding that the destination of the packet is itself, PE2 decapsulates the packet. If the packet is encrypted, PE2 decrypts it after verifying that its digital signature is correct and then sends it to CE2. If the packet is not encrypted, PE2 directly sends it to CE2.
- Author: Han Ming
- Updated on: 2023-07-20
- Views: 2985
- Average rating:







