What Is an MITM Attack?
Man-in-the-middle (MITM) attacks can hijack sessions. An attacker in the middle of communications hijacks the session between the two communication parties and manipulates the communication process without their knowledge. In this way, the attacker steals information or uses fake identities to access the service systems. An MITM attack is a broad concept. It contains many specific attacks, such as Wi-Fi spoofing, email hijacking, DNS spoofing, and SSL hijacking. MITM attacks are often used to steal personal information such as user login credentials, emails, and bank accounts. The attacks are extremely destructive to online systems such as e-banking, online games, and online transactions.
How Does an MITM Attack Work?
An example is used to explain what an MITM attack is. Assume that you come to a cafe, use a laptop, and search for Wi-Fi access points. You find one with the cafe name, connect to it for accessing the Internet, and log in to various online systems. The browser displays a message indicating that the connection is insecure. However, you ignore the message and choose to continue the access. In this case, an MITM attack may have occurred. Your actions on the Internet are monitored by attackers, who can intercept your personal information, such as accounts, home addresses, and email addresses.
Message indicating that the connection is insecure
In the preceding example, an MITM attack consists of two steps:
- An attacker attempts to insert themselves into the link between the two communication parties to intercept communication traffic. As a result, they can steal data or use fake identities to access the service systems.
For example, Wi-Fi spoofing mentioned above is a common method used in the MITM attacks. Once a user accesses the Internet through a fake Wi-Fi router, subsequent communication traffic passes through the fake Wi-Fi router, and all Internet behaviors are monitored by the attacker. In addition to Wi-Fi spoofing, techniques such as malware delivery, DNS spoofing, and ARP spoofing are also commonly used in the MITM attacks.
- After inserting themselves in the communication link, the attacker can manipulate the communication between the two parties and start operations such as stealing data or using fake identities to access service systems.
Technologies such as forging certificates and decrypting traffic may be involved here. In the previous example, the attacker forges a certificate of the website server accessed by the user and sends the fake certificate to the browser. As a result, the browser cannot verify the authenticity of the certificate. After the user chooses to continue the access, the attacker establishes connections with the user and the server without the user's knowledge. Then, the attacker can decrypt the traffic to steal or tamper with the data.
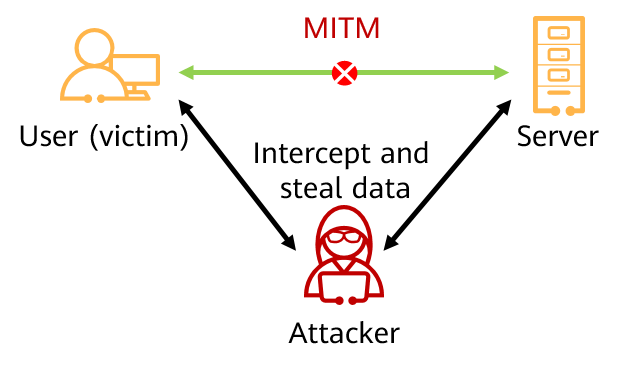
MITM attack process
There Are Five Common Types of MITM Attacks
Attackers can typically exploit various techniques to launch MITM attacks. The following part describes common attack types and technologies.
Wi-Fi Spoofing
As mentioned above, it is the simplest and commonly used method to launch MITM attacks. An attacker creates a malicious Wi-Fi access point whose name is related to the environment, for example, a cafe. The access point name is confusing and the Wi-Fi is not encrypted. When a user accidentally connects to the malicious Wi-Fi access point, all the subsequent communication traffic will be intercepted by the attacker, and the personal information will be stolen.
ARP Spoofing
ARP spoofing is also called ARP poisoning. An attacker pollutes the ARP cache of a user so that the user traffic can be sent to the attacker's host. Access requests initiated by LAN users are forwarded by a gateway. A user first sends an ARP request to obtain the MAC address corresponding to the gateway IP address. An attacker impersonates the gateway and replies to the user with their own MAC address. The user adds the incorrect MAC address to its ARP cache. In this case, all subsequent traffic of the user is sent to the attacker host.
DNS Spoofing
DNS spoofing is also called DNS hijacking. The first step for a user to access the Internet is to send a DNS request to the DNS server to obtain the IP address corresponding to the domain name of a website. Then, the DNS server returns the mapping between the domain name and the IP address. Attackers can tamper with the IP address corresponding to the domain name to redirect user access during this process. The user thinks that they are still accessing a legitimate website, but actually accessing a fake website with the IP address specified by the attacker.
For example, in a well-known DNS spoofing attack, an attacker hijacked the DNS server settings of more than 4 million computers through malware and directed DNS requests to the attacker's DNS server. As a result, the attacker returned fake website IP addresses and obtained illegal income of US$14 million.
Email Hijacking
Attackers hijack the email servers of banks or other financial institutions. The email servers contain a large number of user email accounts. Then, attackers can monitor users' email exchange, or even impersonate banks to send emails to individual users. This helps obtain user information and trick users into performing operations such as bank transfer.
For example, in 2015, attackers defrauded the bank clients of 6 million euros in a country. In this attack, attackers can access bank email accounts and exploit malware or other social engineering methods to trick clients into transferring money to an account.
SSL Hijacking
Currently, most websites are accessed in HTTPS mode. That is, SSL connections are established between users and website servers, and data is verified and encrypted based on SSL certificates. HTTPS can reduce MITM attacks. However, attackers still attempt to use various technologies, such as SSL hijacking, to damage HTTPS. SSL hijacking is also called SSL certificate spoofing. An attacker forges a website server certificate, replaces the public key with its own public key, and sends the fake certificate to the user. In this case, the user's browser displays a message indicating that the connection is insecure. However, if the user does not have strong security awareness and continues the connection, the attacker can control the communication between the user and the server, decrypt the traffic, and steal or even tamper with the data.
In addition, attackers may directly intrude digital certificate issuers and steal real certificates of well-known websites. In 2011, a digital certificate issuer was attacked. As a result, more than 500 well-known website certificates were stolen, leaking a great amount of users' personal information.
How Can MITM Be Prevented?
Although MITM attacks are diversified and difficult to identify, we can still take some measures to reduce attack risks. The following lists some common measures to prevent MITM attacks.
- Do not randomly connect to public Wi-Fi networks. Connect only to known and trusted Wi-Fi networks to prevent traffic from being maliciously hijacked. Do not use the default password of a router for your own Wi-Fi network. Set a high-strength cryptographic protection for a password against being cracked.
- Ensure that an HTTPS website is accessed. You can install the open-source HTTPS Everywhere browser plug-in to enable a browser to automatically connect to an HTTPS website.
- Do not ignore an alarm indicating that the certificate is insecure. If the alarm is generated, the website may be insecure.
- Use VPN for remote access to protect communication traffic.
- Do not open phishing emails which typically disguise themselves as legitimate sources and require users to click links. Identify phishing emails and do not click links in emails. Otherwise, malicious software may be downloaded or you are redirected to malicious websites.
- Install and update antivirus software in time.
- Deploy firewalls and endpoint security software in enterprises and institutions to block malicious attacks and provide security awareness training for employees. Use multi-factor authentication for service systems to increase the difficulty of cracking.
Huawei Security Products Protect You from MITM Attacks
Huawei AI firewalls provide multiple VPN functions to protect your communication traffic and prevent attackers from inserting themselves into communication links. The built-in intelligent detection engine efficiently detects malicious files and blocks attacks when attackers spread malware.
- Author: Liu Shui
- Updated on: 2023-11-22
- Views: 640
- Average rating:







